Microsoft Exchange Server Hacking Allows FBI to 'Access Hacked Computers Throughout the United States'

It was reported in March 2020 that a hacker used a vulnerability in Microsoft Exchange Server to embed a 'web shell that enables remote control from the outside' on computers in tens of thousands of organizations across the United States. The U.S. Department of Justice has announced that the FBI has been approved by the court to access computers with embedded web shells and remove the web shells.
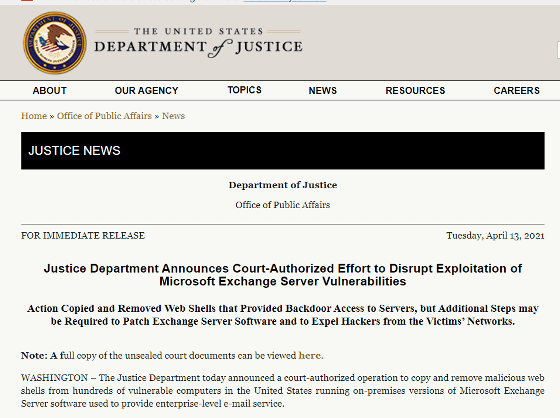
Justice Department Announces Court-Authorized Effort to Disrupt Exploitation of Microsoft Exchange Server Vulnerabilities | OPA | Department of Justice
https://www.justice.gov/opa/pr/justice-department-announces-court-authorized-effort-disrupt-exploitation-microsoft-exchange
MOTION TO PARTIALLY UNSEAL SEARCH WARRANT AND RELATED DOCUMENTS AND [PROPOSED] ORDER
(PDF file) https://www.justice.gov/opa/press-release/file/1386631/download
FBI Accesses Computers Around Country to Delete Microsoft Exchange Hacks
https://www.vice.com/en/article/y3dmjg/fbi-removes-web-shells-microsoft-exchange
It was widely reported in March 2021 that someone had exploited four vulnerabilities called 'ProxyLogon ' in Microsoft Exchange Server to instill a Web shell that could control the system completely remotely. It is believed that the attack was carried out by a Chinese government hacker, Hafnium, and some experts point out that 30,000 organizations, including the US government and private companies, have been hacked. In response, the Cybersecurity and Infrastructure Security Agency (CISA) of the Ministry of Land Security has issued 'Emergency Directive 21-02 ' to all agencies using Microsoft Exchange on-premises products and the private sector of the federal government. He requested that the system be disconnected from the network until a Microsoft patch was applied.
Due to the scale and urgency of this attack, Microsoft released security updates ahead of schedule and distributed patches. However, since the patch only fixes the vulnerability, it is effective as a precautionary measure for undamaged computers, but it does not detect and recover the system that has already been invaded.
In addition, Microsoft released a monthly Windows Update on April 14, 2021, in which security updates related to Exchange Server vulnerabilities are also distributed.
Today is the monthly 'Windows Update' day, Exchange Server vulnerabilities will also be fixed --GIGAZINE

Against this background, as of April 13, 2021, 'Hundreds of machines across the United States where the FBI is running a vulnerable Microsoft Exchange Server to remove the Web Shell from compromised computers. Accessing your computer 'has been approved by the court. The FBI is only allowed to remove web shells, not patch distribution or malware removal.
'By removing the web shell, the FBI prevents malicious attackers from using the web shell to access the server and installing other malware on the computer,' the court document said. After accessing the web shell, entering the password, copying the web shell as proof, and then issuing the command to delete it. '
'We are strong in the public and private sectors, along with previous government and private sector efforts, such as distributing patches and web shell removal tools,' said John C. Demers, assistant attorney for the Department of Justice's National Security Division. The partnership is demonstrated in the country's cybersecurity. Clearly there is still work to be done, but there is no doubt that the authorities are playing an integrated and essential role in this effort. ' Did.
The FBI is trying to contact all owners of computers affected by the attack about the above operations.
Related Posts:
in Security, Posted by darkhorse_log







