A person who used his blog name to hack Microsoft Exchange Server explained that 'I'm not hacking'

Shadowserver Special Report – Exchange Scanning # 5 | The Shadowserver Foundation
https://www.shadowserver.org/news/shadowserver-special-report-exchange-scanning-5/
No, I Did Not Hack Your MS Exchange Server — Krebs on Security
https://krebsonsecurity.com/2021/03/no-i-did-not-hack-your-ms-exchange-server/
The Shadowserver Foundation , a non-profit organization that helps identify and fix security threats, has been compromised by a backdoor and is communicating with a rogue domain called 'brian.krebsonsecurity.top' at 21,248 Microsofts. It reports that it has detected an Exchange Server.
According to The Shadowserver Foundation, attackers who launched hacking attacks are using Microsoft Exchange Server vulnerabilities that Microsoft has addressed in an emergency patch. This vulnerability was reported in January 2021 and became a hot topic.
The timeline for attacks and countermeasures after the discovery of Microsoft's Exchange Server vulnerability looks like this --GIGAZINE

The Microsoft Exchange Server vulnerability allows an attacker to gain complete remote control of Microsoft Exchange Server. The Shadowserver Foundation reports that an attack using this vulnerability to install a new backdoor, 'babydraco.aspx,' on the OWA folder of Microsoft Exchange Server was detected on March 26, 2021 local time. doing.
The Shadowserver Foundation uses a honeypot to execute a Microsoft Powershell script that multiple hosts infected with 'babydraco.aspx' fetch an executable file called 'krebsonsecurity.exe' from the IP address '159.65.136 .128'. Detected that you are doing.
This executable file, 'krebsonsecurity.exe', is designed to be undetected by security software by installing a root certificate, modifying the system registry, and instructing Windows Defender not to scan the file. And that. In addition, 'krebsonsecurity.exe' seems to be sending a small amount of traffic per minute to peep at the encrypted communication between Microsoft Exchange Server and '159.65.136 .128'.
The Shadowserver Foundation reports that more than 21,000 Microsoft Exchange Servers have been infected with 'babydraco.aspx'. However, it is unknown how many of these systems have downloaded a malicious executable file called 'krebsonsecurity.exe' from an invalid IP address.
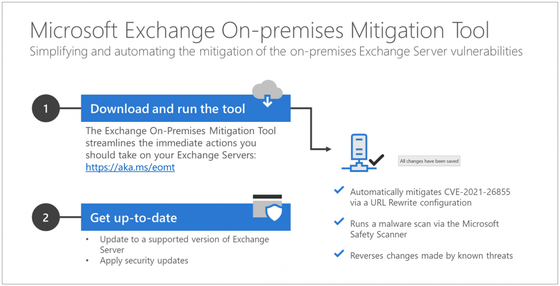
Note that Microsoft Exchange Server users who have not applied the patch released by Microsoft in early March 2021 can immediately protect their system by using the
Brian Krebs, who runs Krebs on Security, said, 'The motive of the cybercriminal who launched this hacking attack is unknown, but the malicious domain itself called'brian.krebsonsecurity.top'used in the attack is a cybercrime and It's used for harassment. I learned about this domain in December 2020, and one reader reported that it was used for the cryptocurrency mining botnet. ' I will.
'This isn't the first time I've used my name, portrait, or website I run for cybercrime or harassment to damage my reputation,' Krebs said. It has been around for 10 years, 'he said, saying that similar harassment has been repeated.
Related Posts:
in Software, Web Service, Security, Posted by logu_ii