'Vulnerability to spoof address bar' exists in multiple browsers such as Safari on iPhone

Todd Beardsley, director of research at security firm
[Vuln Disclosure] Mobile Browser Bar Spoofing Vulnerabilities
https://blog.rapid7.com/2020/10/20/vulntober-multiple-mobile-browser-address-bar-spoofing-vulnerabilities/
This vulnerability is specified as ' CWE-451 ' in the Common Weakness Enumeration (CWE) of the Common Vulnerability Type List. Mobile browsers that have been pointed out to be vulnerable include Safari , Opera Touch , Bolt Browser , and RITS Browser .
The vulnerability involves tampering with when an attacker refreshes the browser's address bar when a web page loads, causing pop-up notifications to appear to come from any website or to be incorrectly displayed in a browser window. It has the potential to render content.
In either case, the victim must visit a website where attackers can post executable JavaScript. In other words, it is not possible to be attacked using this vulnerability via major sites such as Facebook and Twitter, but it is possible to be attacked via websites created by attackers.
Mr. Beardsley said, 'For example, when an attack using a vulnerability is launched via spam mail such as'There is an important message from the payer, please click this', the information on the address bar is tampered with and it is genuine. It will look like a PayPal page, in which case the attacker is likely to enter his credentials. '
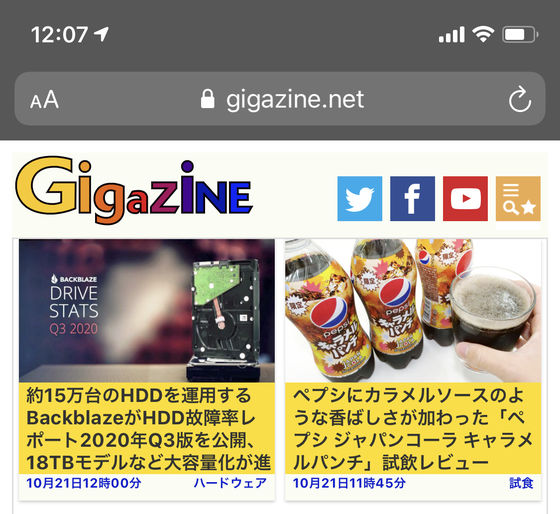
The image below is a proof of concept of 'vulnerability to disguise the address bar'. I'm seeing a fake website that says 'This is not Bing', but the address bar shows

Mobile browsers are one of the most frequently used apps for smartphones, and maliciously distorting their display can cause enormous confusion for users. 'Mobile browsers need a mechanism to validate the pages they display and the source of pop-up notifications,' Beardsley said, because 'the address bar shows how to check the source in a mobile browser.' It is said that it is because there is only 'check the URL'.
Another problem is that mobile browsers have a very limited area for displaying security information. For PC browsers, you can check the information about the SSL server certificate from the icon on the address bar, but you cannot check the SSL server certificate with the mobile browser.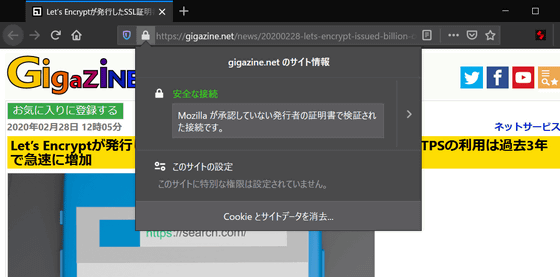
The address bar part of the mobile browser is also an area where developers are prohibited from modifying it, so it is almost like an inviolable area. Therefore, in order to fix the 'address bar spoofing vulnerability', the browser developer needs to deal with it, but when Mr. Beardsley notified the affected browser of the vulnerability, Safari / Opera Touch -Bolt
In addition, all browsers affected by the 'address bar spoofing vulnerability' are popular apps, and even the Bolt Browser, which has the fewest users, has posted more than 210,000 reviews, and the App In the Store, it is ranked 47th in the ranking. UC Browser, with its vulnerabilities unfixed, has been downloaded over 500 million times on Google Play.

Related Posts:
in Software, Smartphone, Security, Posted by logu_ii