How does 'OAuth 2.0' used to give access permission on SNS etc. work?

'
Everything You Need to Know About OAuth (2.0)
https://gravitational.com/blog/everything-you-need-to-know-about-oauth/
In account authentication, there are multiple factors such as the account owner and services that provide accounts such as Facebook and Spotify. In OAuth, the following four types of roles called 'roles' are used for each factor in authentication. It is said to be given to.
-Resource owner: An element that allows access to a protected resource. Account owner
· Resource server: A server that provides protected resources and handles access requests.
-Client: An application that wants to access the resource server and perform actions on behalf of the resource owner.
· Authorization server: A server that allows clients to access the resource server.
Mr. Mody explains the flow of authentication with OAuth based on the case where Bob who has a Spotify account links Facebook and Spotify.
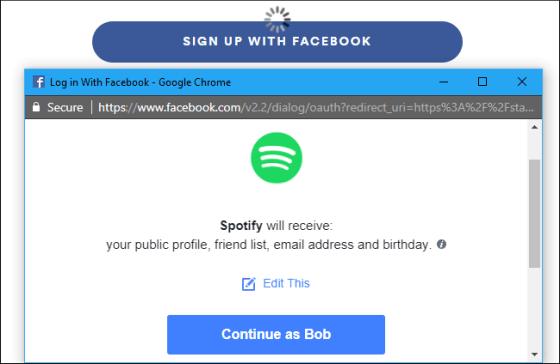
Spotify will first send a message to Bob, the 'resource owner' who owns the account, requesting access to Bob's public profile, friends list, email address, and birthday, Mody said. Here, Spotify is the “client”. Bob then authorizes Spotify to collect the data. Authorized Spotify notifies Facebook API of authorization. The Facebook API validates the authorization and sends an
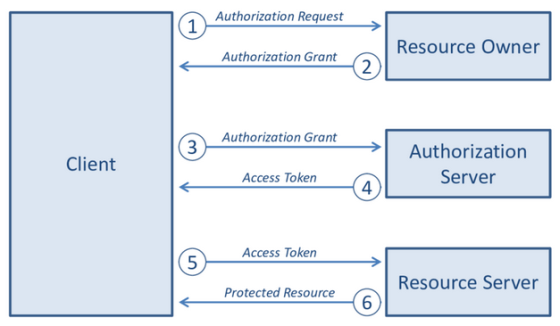
The access token has a variable called 'scope'. Mr. Mody compares the relationship between access token and scope to a movie ticket, the access token is the ticket itself, the scope is the name of the movie written on the ticket. There are generally four types of scopes: 'read access', 'write access', 'read/write access', and 'no access'. It is explained that there is another token called 'refresh token' that is used to automatically obtain a new access token when a resource cannot be obtained due to expiration etc.
Considering again the example of a movie theater, there are multiple OAuth authorization flows, as there are multiple ways to purchase movie tickets, such as 'how to buy at a movie theater' and 'how to buy online'. That. Mr. Mody
'Authorization code grant' is the most general authorization flow, which is a method for the client to exchange the unique code received from the authorization server for tokens. By dividing the steps required to receive the token into two stages, the authorization server can confirm important information about the client before issuing the token. Authorization code grant using PKCE extension is a method to transfer hash to confirm that communication between client and server is not intercepted using PKCE.
'Client authentication' is a flow used when the client requests access authorization to the client itself. In this case, the client makes a request that includes the variables 'client_id' and 'client_secret'. The 'device code' is a flow used by devices such as game consoles and smart TVs that sign in using a controller and virtual keyboard.

Mody explains OAuth authentication using the OAuth implementation for single sign-on on GitHub. First, the application is authenticated between resource owners, and the resource owner requests authentication from the authorization server. Since authentication is performed by the authorization code grant, the authorization server issues the authentication code and access token to the application. The application that converted the authentication code into an access token sends the access token to the resource server to access the resource.
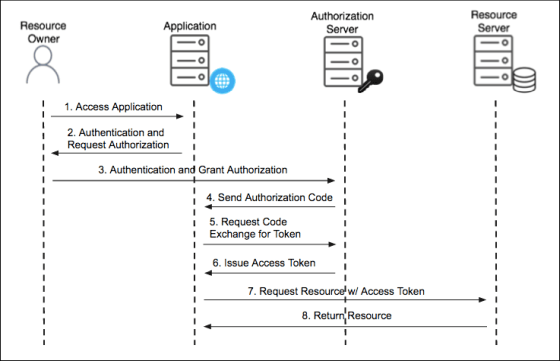
OAuth offers the convenience of being overlooked, but it's a complex protocol and it takes a long time to implement. 'I hope you have a comprehensive and complete understanding of OAuth,' commented Mody.
Related Posts:
in Software, Web Service, Web Application, Posted by darkhorse_log