Apple's tracking prevention function 'Intelligent Tracking Prevention' is updated in iOS 13.3, what is its content?
by
Apple released 'iOS 13.3' and 'iPadOS 13.3' on Tuesday, December 10, 2019 local time. In addition to new features such as the ability to restrict children's calls, FaceTime, and messaging, this update also includes security-related updates. And Apple's Intelligent Tracking Prevention (ITP), which has been introduced to Safari since 2017, has been strengthened, and John 's WebKit engineer John Wilander explains how ITP has been strengthened.
Preventing Tracking Prevention Tracking | WebKit
https://webkit.org/blog/9661/preventing-tracking-prevention-tracking/
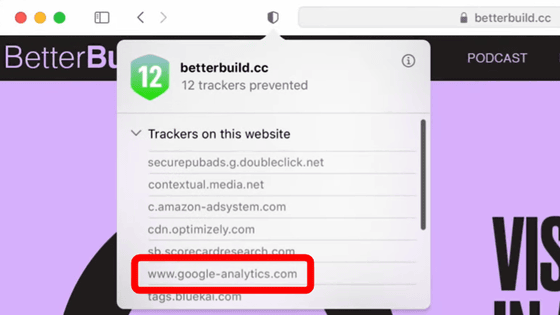
Content blocking and tracking prevention that change the handling of content depending on Origin and URL risk can be exploited in such a way that the Origin or URL set itself gives the browser uniqueness and detects that uniqueness. In order to prevent such misuse of tracking prevention, it is necessary to make it impossible to detect itself “what web content and website data can track the browser”. As a result, Apple makes it impossible to detect differences in how different websites are handled by different browsers, and Willander says that ITP has been devised to improve overall tracking prevention.
◆ Invention 1: Referrer downgrade
ITP has downgraded all cross-site request referrers to Origin only. Previously, this method was only taken for cross-site requests for classified domains. Due to this change, the referrer header for requests to 'https: //images.example' previously included 'https: //store.example/baby/strollers/deluxe-stroller-navy-blue.html' However, only 'https: //store.example/' will be written in the future.
◆ Device 2: All third-party cookies on websites without prior user interaction are blocked
ITP blocks all third-party requests from seeing a user's cookies, unless the third-party website is being manipulated by the user, regardless of the third-party domain status.
◆ Ingenuity 3: Storage Access API should consider cookie policy
Safari's original cookie policy restricts third parties from setting cookies, except those already set as first party. This has worked even after the introduction of ITP.
In order to avoid problems caused by ITP, there is a ' Storage Access API ' that enables first-party service authentication with embedded cross-site content while maintaining privacy. Apple newly clarified that the Storage Access API takes into account Safari's cookie policy when 'document.hasStorageAccess ()' is called. As a result, “document.hasStorageAccess ()” may be false for the following two reasons.
1: When ITP blocks cookies and detailed storage access is not allowed
2: When the domain does not have cookies, and therefore the cookie policy blocks cookies
by edar
Mr. Wilander also mentions the concern that the ITP status may leak to outside attackers because cookies are not sent from third parties. According to Wilander, the cookie was not sent because 'ITP blocked the cookie' 'Because the cookie policy blocked because it has never been visited' 'The cookie on the website expired `` Because users and ITP deliberately erased the cookie of the website '', there are several possible causes, so it is said that ITP status can not be confirmed by not sending cookie requests from third parties That is.
Related Posts: