It turned out that location information and personal information were easily available from the '3P Swapping lovers' dating app

by
Security issues are often pointed out for dating apps that support men and women's encounters, and in the past there were also cases where about 37 million personal information leaked from the world's largest SNS for married people Ashley Madison doing. And, a new security service company, Pen Test Partners , reported that users' location information and personal information could be easily obtained from dating apps for '3P and lover swapping enthusiasts'.
Group sex app leaks locations, pics and personal details.Identifies users in White House and Supreme Court | Pen Test Partners
https://www.pentestpartners.com/security-blog/group-sex-app-leaks-locations-pictures-and-other-personal-details-identifies-users-in-white-house-and-supreme-court/
Pen Test Partners investigated a dating app called “ 3fun ”. By installing the iOS version or Android version application, it is touching that you can find a partner who is interested in 3P living in the vicinity and swapping, even for transgender, gay and bisexual users That's it. 3fun has announced that 1.5 million users are registered worldwide and explains that there are many users in New York, Los Angeles, Chicago, Washington, DC, etc.
3fun uses the user's location information, so you can search for people who live nearby. Some dating apps, such as Grindr, a dating app for gay men, not limited to 3fun, use the smartphone's GPS function to display location information between users. However, 3fun does not specify the location information using the GPS function, and it seems that the location of the user is specified by transmitting the 'latitude and longitude' of the location where the user is from the smartphone as it is.

by rawpixel.com
Pen Test Partners pointed out that this system has a much greater security risk than positioning using GPS. To make matters worse, 3fun users can control location information on / off from the app, but this filtering only works on the app. In other words, even if the location information setting is turned off, the location information from the smartphone itself is sent to the 3fun server and is not displayed on the mobile application interface.
Pen Test Partners has announced that it has discovered a problem where the user's location information accumulated on this server can be obtained via the API. This is an image showing the location information of users in the UK.
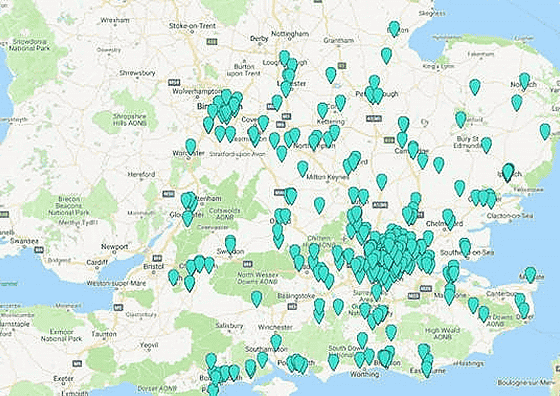
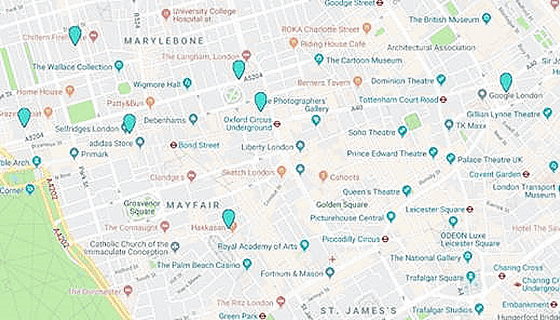
It is also possible to know more detailed location information such as in London.
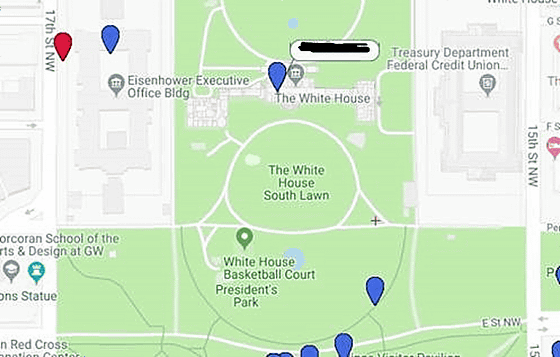
The user situation in Washington DC is like this.
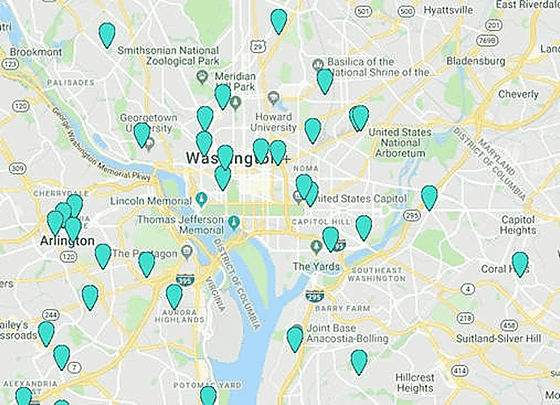
There was also a user in the middle of the White House. However, technically, it is possible to tamper with the location information sent to the server, so it is possible that someone pretends to be a power person as a joke.
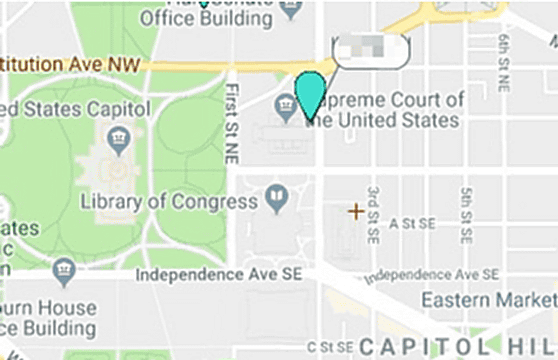
It was said that users in the United States Supreme Court could also be found.
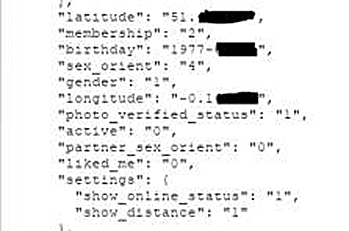
In addition, the data that can be obtained from the server is not limited to location information, but it is also possible to obtain data that includes the date of birth that makes it easy to identify the individual user. By combining location information and date of birth, you can locate individuals with considerable accuracy.
Furthermore, by using the API, it is possible to obtain photo data that is denied access from the app due to privacy settings. Pen Test Partners believes that there are many vulnerabilities in 3fun apps and APIs, and there will be more problems than what we found this time, but verifying all the problems is very States that it is impossible. In addition, based on the gender and sexual orientation of the available users, we investigated the `` gender ratio of heterosexuals '', and it seems that the ratio of heterosexual men and straight women was 4: 1. .
On July 1, 2019, Pen Test Partners reported to 3fun to report a security issue and ask them to fix it. Although 3fun seems to have responded quickly and solved the problem, Pen Test Partners said it was a pity that the user's personal information had been compromised for a very long time.

by Pixabay
Related Posts:
in Mobile, Web Service, Security, Posted by log1h_ik