We found a vulnerability capable of delivering smartphone's "spoofing", tracking, fake emergency bulletin on 4G LTE network

There is a vulnerability that makes it possible for third parties to "spoof" or spy eavesdropping of communications, tracking and spam transmission to the LTE network (4G) who would use the smartphone almost certainly It is pointed out by security experts.
LTEInspector: A Systematic Approach for Adversarial Testing of 4 G LTE
(PDF)http://wp.internetsociety.org/ndss/wp-content/uploads/sites/25/2018/02/ndss2018_02A-3_Hussain_paper.pdf
New 4 G LTE Network Attacks Let Hackers Spy, Track, Spoof and Spam
https://thehackernews.com/2018/03/4g-lte-network-hacking.html
This study was conducted by researchers from Purdue University and Iowa University in the USA. This team points out the danger by listing 10 new attack methods that can be executed on the actual LTE communication network. This vulnerability than those present in 4G communication protocol, which and to perform the transmission of the telephone call and text messages with malicious hackers to exploit the transmission of an emergency alert false, spoofing location information (Dodge ) To make it possible for criminals to produce favorable alibis for themselves.
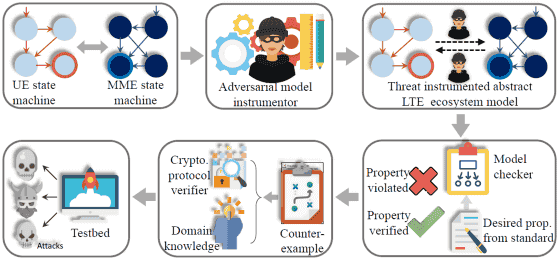
According to the research team, this vulnerability is based on three main processes included in the 4G communication protocolattach"detach"pagingIt is related to things. attach is a process performed when the terminal is switched on or returning from the aircraft mode, detach is a process carried out when the power is turned off or in the airplane mode, and paging is a function to call multiple terminals simultaneously .
Also, what should be noted in this report is that these vulnerabilities are not merely theoretically proven, but that they are actually practicable. The research team used the framework for testing "vulnerability detection"LTEInspector"It is confirmed that eight out of ten vulnerabilities are reproduced in the terminal actually inserted SIM card used in the United States. The 10 vulnerabilities are as follows.
· Authentication Synchronization Failure Attac
Traceability Attack
· Numb Attack
· Authentication Relay Attack
· Detach / Downgrade Attack
· Paging Channel Hijacking Attack
· Stealthy Kicking-off Attack
· Panic Attack
· Energy Depletion Attack
· Linkability Attack
Especially researchers point out that "Authentication Relay Attack" is the most dangerous. In this attack, the attacker not only enables the text message to be sent and received by disguising the victim's telephone number as his phone, but also makes it possible for the attacker to tailor the victim to one who is involved in the crime Thing. Also, by lowering the accuracy of the position information of the terminal, it is possible to hide inconvenient information for crime and to cheat position information when hacking attacks are done.
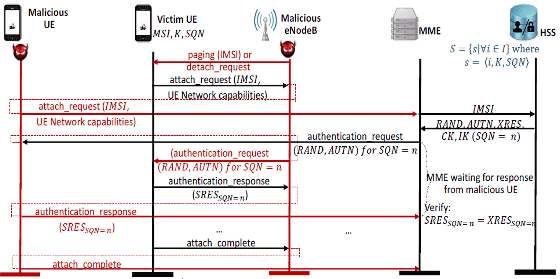
Also, by using "Panic Attack" (an attack by panic), an attacker can also send emergency information of fake to confuse society. And these problems are serious in that they can perform attacks relatively easily by using equipment that can be obtained from about 1,300 dollars to 3,900 dollars (about 160,000 yen to 410,000 yen).
The survey team has reported details to the parties that are deemed relevant for this issue, and is waiting for the problem to be solved. Also, make these problems runProof of conceptWe are not planning to announce the code until the problem is resolved.
Related Posts:
in Smartphone, Security, Posted by darkhorse_log