Web browser password manager steals user information vulnerability
The Web browser has a function to record the login ID and password of the website and web service in consideration of the user's convenience. However, we found that there is a vulnerability in this password manager that stolen user information saved by a third party script.
No boundaries for user identities: Web trackers exploit browser login managers
https://freedom-to-tinker.com/2017/12/27/no-boundaries-for-user-identities-web-trackers-exploit-browser-login-managers/
Flaw In Major Browsers Allows 3rd-Party Scripts to Steal Your Saved Passwords
https://thehackernews.com/2018/01/browser-password-managers.html
The point of vulnerability was pointed out by the information technology policy center of Princeton University "Freedom to Tinker".
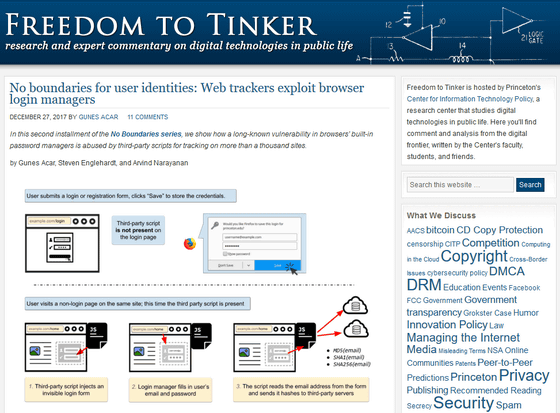
According to Freedom to Tinker, information is still safe at the time of recording user information in the password manager, but after that, another page with a tracking script by a third party charged on the same website (domain) is opened And the script displays an invisible login form. Then, the login information of this site is automatically entered by the password manager and it is stolen. In the case of a service using a mail address as a login ID, the mail address will be leaked.
Freedom to Thinker prepares a demo page that shows the process of actually stealing information.
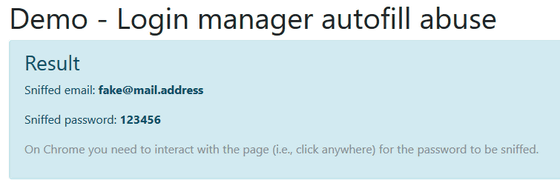
Demo - Login manager autofill abuse
https://senglehardt.com/demo/no_boundaries/loginmanager/
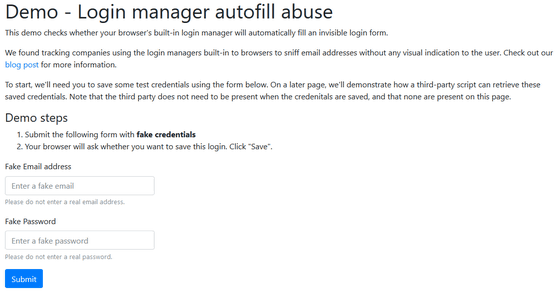
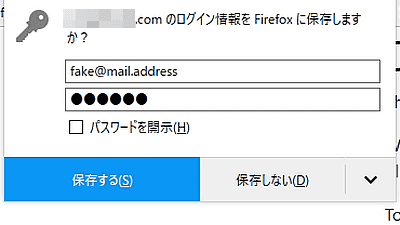
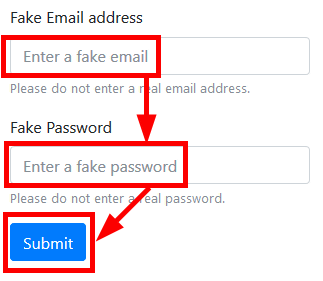
On the input form at the bottom of the page, enter the appropriate fake email address and also the appropriate fake password and click Submit. Although it is a demo page, please do not enter the e-mail address or password of the phone.
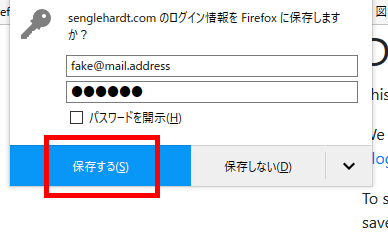
Click "Save" when a dialog asking whether to save login information appears. For Firefox this is the screen.
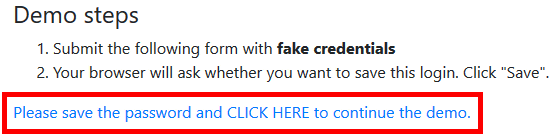
Click the character string "Please save the password and CLICK HERE to continue the demo." At the bottom of the page.
Then the page transitions and the fake email address and password you entered earlier was displayed. For Chrome, you need to click somewhere after moving the page.
According to Freedom to Thinker's survey, the same type of script was found in 1110 cases among the top 1 million sites in Alexa website ranking.
As a simple measure, first of all, do not save login information of untrusted sites in the password manager of the browser. Also, cutting off the auto-fill function of the browser is one hand.
Related Posts: