New hacking techniques to tamper with e-mails, can also be tampered with received e-mails

ByDivya Thakur
A security researcher reported a method that allows you to rewrite mails that should have been harmless URLs at the time of receiving mails to harmful URLs by manipulating them later. This will allow attacks that spy off spam filters and security filters.
Introducing the ROPEMAKER Email Exploit | Mimecast Blog
https://www.mimecast.com/blog/2017/08/introducing-the-ropemaker-email-exploit/
Simple Exploit Allows Attackers to Modify Email Content - Even After It's Sent!
http://thehackernews.com/2017/08/change-email-content.html
This method, named Ropemaker (Remotely Originated Post-Delivery Email Manipulation Attacks Keeping Email Risky / an attack that remotely modifies e-mail after sending mail) is a researcher of security company Mimecast What was reported by Francisco Ribeiro.
According to Ropemaker, Mr. Ribeiro proves that it can be said that "after sending the URL or the like described in the mail sent by the attacker himself / herself, after reaching the other's inbox, replace it with a malicious URL" Did. This makes it possible to deliver mails by spam filters and security filters without requiring direct access to the recipient's computer.
According to Matthew Gardiner, Senior Product Marketing Manager at Mimecast, Ropemaker is a common part of email and web technologies, especially CSS and HTML abuse. "Web technology has made text-based emails visually attractive and dynamic, but this also makes it possible for attacks," he said.
Mail using CSS reads information on the outside, so even if the mail arrives at the other party, by replacing CSS, you can change the URL displayed in the mail at the recipient's hands from harmless to malicious It is possible to change to. For example, in the following inbox, the URL containing the word "GoodURL" is displayed ... ...
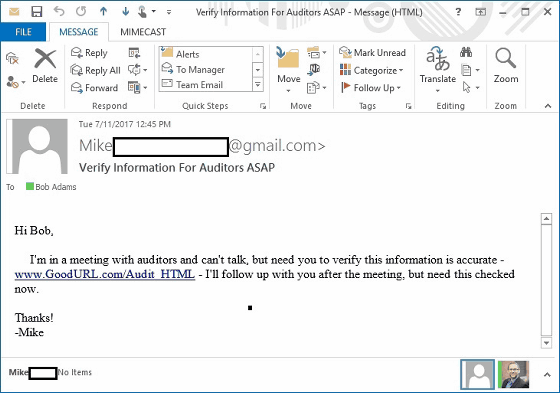
By modifying the CSS side, I changed the above character to the word "BadURL".

Ropemaker allows an attacker to direct a recipient to a website that exploits personal information. In addition, Ropemaker can generate variations by attacker's creativity and techniques, for example, writing text in tabular form and then using CSS to create "display part" and "display part" The method said that it is more difficult to detect than the URL replacement type because it is possible to create a state that "no URL is written" at the time of receiving the mail.
Although it is said that attacks using Ropemaker were not found at the time of article creation, it is pointed out that there is a possibility that "just not detected". It is recommended that you use web-based clients such as Gmail, iCloud, Outlook, etc. in order not to match Ropemaker attacks.
Related Posts:
in Security, Posted by darkhorse_log