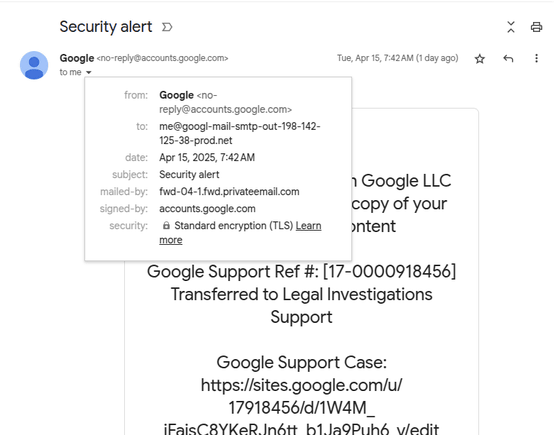
Phishing email attack that appears to be sent from 'no-reply@google.com'

It has been revealed that there are
Phishers abuse Google OAuth to spoof Google in DKIM replay attack
https://www.bleepingcomputer.com/news/security/phishers-abuse-google-oauth-to-spoof-google-in-dkim-replay-attack/
Google Spoofed Via DKIM Replay Attack | EasyDMARC
https://easydmarc.com/blog/google-spoofed-via-dkim-replay-attack-a-technical-breakdown/
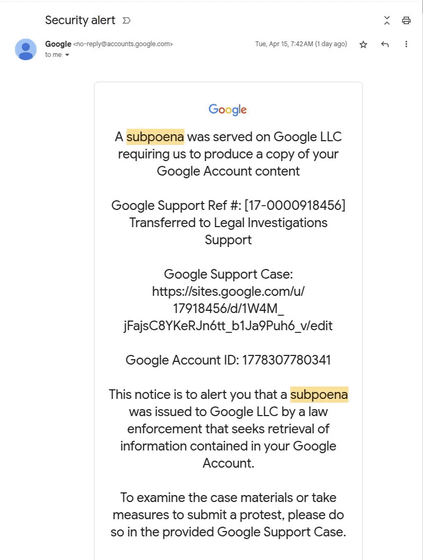
Nick Johnson , a developer of the Ethereum Name Service (ENS) , a decentralized open naming system that can interact with the Ethereum blockchain, received a security warning email that appeared to be from Google, stating that he had received a subpoena from a law enforcement agency seeking information about his Google account.
Below is a screenshot of the email Johnson received: Because it looks almost legitimate, 'there is a high chance of fooling non-technical users who don't know where to look for signs of fraud,' security media BleepingComputer points out.
However, Johnson notices that the URL for the support portal in the email is hosted on
When you visit the support portal, you'll see a fake webpage that's a perfect replica of a Google support page. 'The only clue that this page is a phishing page is that it's hosted on sites.google.com instead of accounts.google.com,' Johnson said. Email authentication platform EasyDMARC also points out that 'just because a domain looks real doesn't mean the content hosted on it is real.'
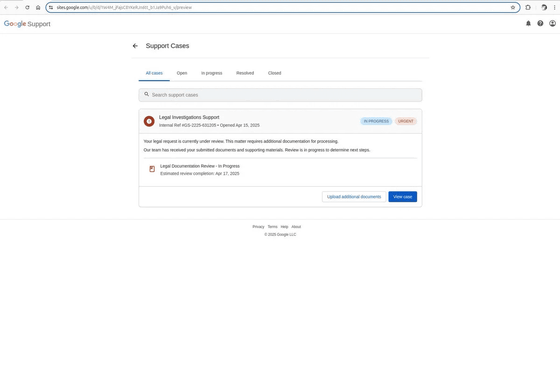
EasyDMARC points out that 'Google Sites is part of Google Workspace, and any authenticated user can create a custom website hosted under Google Workspace. Its ease of use, cost savings, and native integration with Google services make it popular for internal and public content, but its convenience has been weaponized by attackers.' EasyDMARC lists the following three reasons why Google Sites is dangerous:
Anyone with a Google account can create a site that looks legitimate and is hosted on a trusted Google-owned domain.
No custom hosting or domain registration is required, allowing attackers to leverage Google's
Attackers can embed fake content (fake login screens, credential-harvesting forms, misleading CTAs ) under domains that pass public trust and automatic link validation checks.
Johnson speculates that the fake support portals were designed to harvest credentials in order to compromise recipients' Google accounts.
One of the clever things about this phishing email is that it appears to pass Google's DomainKeys Identified Mail (DKIM) validation using a technique called a DKIM replay attack .
Specifically, the attacker would first need to receive a genuine email from Google 'no-reply@accounts.google.com' that contained a valid DKIM signature, then the attacker would extract and save the email itself, including the headers and body, without modifying anything that was signed by DKIM.
DKIM works by applying a digital signature to certain headers and the body of an email when it is first sent. This signature is generated using the sender's private key and attached as a header to the email itself.
When a message is forwarded, the original DKIM signature typically remains intact, as long as the content and headers of the email it is signed on remain unchanged. Because forwarding services often store the original message intact, the DKIM signature remains valid and can be verified using the sender's public DNS record.
The attackers then sent the spoofed messages using email addresses from Outlook, a Microsoft email service, which passed the messages to a custom SMTP service that acted as an intermediate relay, keeping the spoofing away from Google.
The message will be received by Namecheap's mail infrastructure (PrivateEmail) and mail forwarding will be provided by four systems: mta-02.privateemail.com, DIR-08, fwd-04.fwd.privateemail.com, and fwd-04-1.fwd.privateemail.com.
You sign up for a Google Workspace account (free trial) and verify your domain with a DNS TXT record. Then you create a Google OAuth app and grant it access to your account. The problem is that Google sends alerts or notifications to a privately registered email address that verifies your domain but has a different MX record than Google.
Another problem is that Google allows you to put anything you want in the app name field, and you can even put 'no-reply@account.google.com' as the from address, which will result in a reply address of your choice.
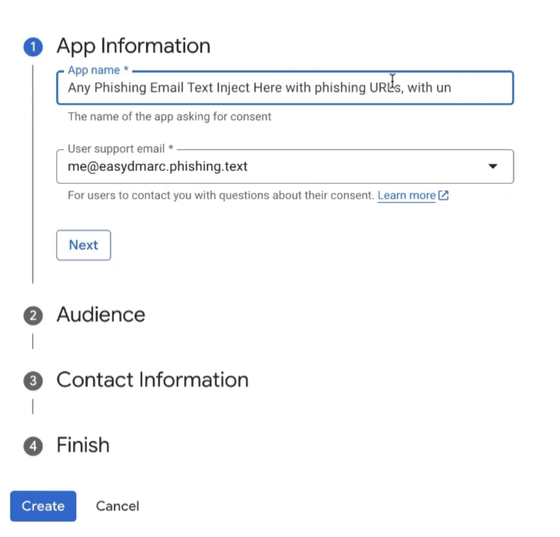
As a result, the 'From' and 'Signed-by' addresses of the email will be Google addresses, and the 'mailed-by' address will be 'fwd-04-1.fwd.privateemail.com'.
The same phishing email attack reported by Johnson has also been attempted on platforms other than Google. A similar phishing email attack targeting PayPal users was reported in March 2025. In the case of phishing email attacks targeting PayPal users, BleepingComputer has found that attackers can use the gift address option to create phishing email attacks linked to PayPal accounts.
Johnson submitted a bug report to Google, and Google initially responded that the process was working as intended, but later said it was working to fix the OAuth vulnerability.
Related Posts:
in Web Service, Security, Posted by logu_ii







