WikiLeaks releases a confidential document "Vault 7" that reveals the actual state of CIA's secret intelligence operations, such as "hacking and caring a car and recording a conversation in a room on a TV"

WikiLeaksOn March 7, 2017, a confidential document on the top secret operation of CIA "Vault 7"Has been released. A number of secret operations such as CIA collecting personal information using smartphone and smart TV, hacking cars, collecting data on French presidential election are revealed.
Vault 7 - Home
https://wikileaks.org/ciav7p1/
WikiLeaks Releases Trove of Alleged C.I.A. Hacking Documents - The New York Times
https://www.nytimes.com/2017/03/07/world/europe/wikileaks-cia-hacking.html
WikiLeaks CIA files: Spy agency looked at ways to hack and control cars to carry out assassinations | The Independent
http://www.independent.co.uk/life-style/gadgets-and-tech/news/wikileaks-cia-documents-files-spying-car-control-hack-central-intelligence-agency-a7616851.html
According to WikiLeaks, "Vault 7" is a confidential document collected from 2013 to 2016 and consists of 8761 documents that were kept at Cyber Intelligence Center of CIA Headquarters. Confidential materials covering hundreds of billions of rows have been distributed unauthorized to US government officials and hackers engaged in hacking, and one of them explains the acquisition route when one of them provided materials to WikiLeaks.
Since the simultaneous terrorist attacks in 2001, the CIA has a political advantage over the budget for the National Security Agency (NSA). Therefore, in the bureaucratic organization, the CIA was able to escape the obligation to disclose proprietary technology to rival NSA, now CIA hacking troops consisting of more than 5000 people have 1000 trojans, viruses, malware etc. 1000 WikiLeaks says that he has used his own hacking tool and has accumulated hacking ability as more codes than Facebook's code number are used.
According to WikiLeaks, CIA malware and hacking tools are being developed by the Engineering Development Group (EDG) of Software Development Division of Center for Cyber Intelligence (CCI) under direct control of CIA Directorate for Digital Innovation (DDI). WikiLeaks has released the organization chart of the CIA and has made the reality of the organization naked.
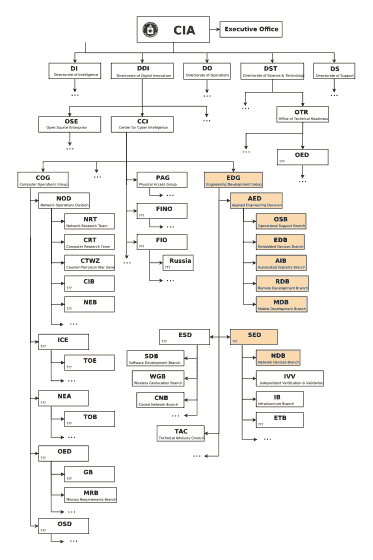
Cyber attack tool targeting various terminals
·tv set
According to WikiLeaks, CIA has developed a tool to hack Samsung's smart television in collaboration with British intelligence agency MI 5. When entering a smart TV, it puts the television in "fake" power OFF mode, and actually it is cheated as if the user is in an OFF state although the television is ON, and the conversation in the room is recorded And then sent it to the CIA server via the Internet. The service agreement of Samsung's smart television is revised as 2015 that "TV may capture audio data and audio data may be provided to third parties", the New York Times pointed out It is.

· Android
In order to hack smartphones, CIA not only develops tools that attack Android with nearly 85% global market share by CIA itself, but also purchases from GCHQ, NSA, server attack contractor, and 24 tools in 2016 It was said that it had equipped. This means that CIA can bypass the encryption function of WhatsApp, Signal, Telegram, Wiebo, Confide, Cloackman and can collect voice data and message traffic before being encrypted.
· IPhone
The share is 14.5%, which is a minority iOS compared to Android, but of course CIA is targeting it. The CIA was organizing a dedicated hacking team for iOS in order to develop malware that infects the iPhone and iPad and takes control of the terminal and extracts data. Besides proprietary iOS hacking tool, CIA also has a lot of cyber weapons obtained from GCHQ, NSA, FBI, cyber attack organizations. WikiLeaks points out the possibility of adopting a special organization even if the share is small because of the iPhone popular in the "elite layer" in business, politics, diplomacy.

· Windows and others
CIA said it is taking a lot of resources to infect Windows PCs and control them from the outside. Multiple attack systems are being developed by the division Automated Implant Branch (AIB). In addition, WikiLeaks says that it is also developing malware that supports multiple platforms such as Windows, Mac OS X, Solaris, Linux,
·Automobile
According to WikiLeaks, the CIA planned to hack highly computer controlled cars and trucks in October 2014. The document does not clarify the purpose of hijacking the car, but WikiLeaks guesses that it is to assassinate the target by controlling the car and causing an accident.

◆ Exploitation of vulnerability
The US government has released information on vulnerabilities found in the software under the Vulnerabilities Equities Process policy, but the CIA has exploited vulnerability information that is not publicly disclosed. According to WikiLeaks, CIA specific malware seems to be able to infect and control both Android and iOS software which manages President 's Twitter account. This malware exploits an undisclosed vulnerability, but as long as the CIA hides the information it will not be modified and will continue to be hacked.
◆ Base for EU intelligence activities · Consulate in Frankfurt
WikiLeaks reveals that the American consulate in Frankfurt, Germany, is the base of intelligence activities in Europe, the Middle East and Africa. A CIA hacker who enters and leaves the Frankfurt consulate has issued a black back cover diplomatic passport, and if it is asked "What is the purpose of the trip?" By answering "I will do technical support at the consular office" We can smoothly pass customs in Germany. CIA hackers operating in Frankfurt are free to move 25 European countries including France, Italy and Switzerland.
Many CIA 's electronic attacks are designed in consideration of physical contact. WiKiLeaks points out that if you attack a target PC with malware-containing USB memory, you can also enter networks separated from the Internet such as police databases.

CIA spokesperson Dean Boyd said about WikiLeaks "the largest intelligence publication in history" called "Vault 7", "CIA commented on the authenticity and content of intelligence documents Do not do it "to the New York Times, and the truth of Vault 7 is not clear. However, WikiLeaks said, "As CIA's hacking capability may be beyond delegated authority and should be discussed publicly," cyber attacks, privacy violations, national security and democracy The purpose is to raise issues of control and begin public discussion. From now on, Vault 7 will be scrutinized from various viewpoints and the operation of CIA will be discussed.
Incidentally, have you considered that criticism that the leak information of WikiLeaks could have a serious influence on the security of the state was taken into consideration, the name of the staff of the concrete staff, the organization name, etc. are replaced by the identification information, It also states that computer code on "weapons" will be kept private until a public consensus is obtained. By the way, Vault 7 which was released this time is just an introduction of a series of series, and it seems that further information will be released in the future.
· Continued
"Most of CIA hacking vulnerabilities have been addressed," Google and Apple announced, but still dangerous conditions continue - GIGAZINE

Related Posts:
in Note, Posted by darkhorse_log






