The North Korean original OS "Red Star" can easily hack just by opening the link though security performance is ugly

North Korea developed its ownRed Star OSIs one of the sellers that is more secure than any other OS such as Windows, but by a new survey, it is possible to remotely access from the outside by opening a specific link on Red Star OS It turned out to be.
RedStar OS 3.0: Remote Arbitrary Command Injection - My Hacker House
https://www.myhackerhouse.com/redstar-os-3-0-remote-arbitrary-command-injection/
North Korea's Linux-based Red Star OS can be Hacked Remotely with just a Link
http://thehackernews.com/2016/12/redstar-north-korea.html
The development of the North Korean OS "Red Star" based on Linux was revealed in 2006. Although it is Red Star OS used in North Korea as an OS that is not open to the outside, version 2.0 will leak to the media in 2010.
North Korea developed its own domestically produced OS "Red Star", technically "10 years late" - GIGAZINE
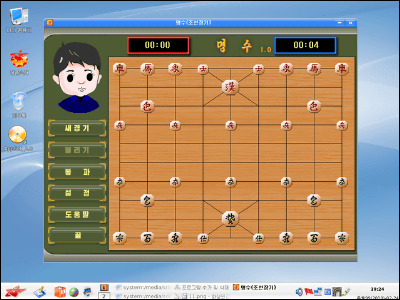
Version 2.0 is a Windows-like appearance. Known as the folk song of the Korean Peninsula as the start toneArirang"Is used and the calendar is also late · Start counting from the birth of President Kim Il Sung"Subject thoughtCalendar "had been adopted.
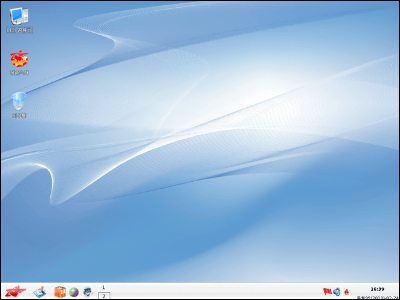
After that, in version 3.0 released in 2013, it changed to a Mac OS X-like desktop.
A fatal security hole is found in North Star's proprietary Mac OS X-like OS "Red Star" - GIGAZINE
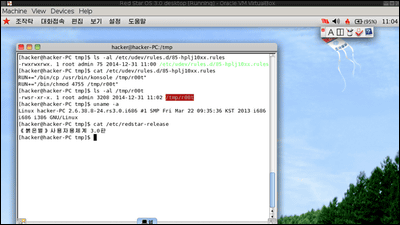
Version 3.0 of Red Star OS has security capabilities that can withstand attacks from abroad, and the government was able to forcibly restrict user's access. However, in reality, there is a fatal security hole in Red Star OS, it is possible to easily raise the user's authority to the administrator authority, all security measures established by North Korea are easily avoided It was reported that it was made possible.
And newly, security firm Hacker House's investigation shows that there is a fatal vulnerability that "PC users can remotely access by hackers simply by opening a link on Red Star OS" Turned out. Red Star OS has a Firefox-based browser called "Naenara" installed, but hackers said that code execution can be done by using mailto type URI.
Hacker House hacker noticed that registered handlers pass command line utilities "/ usr / bin / nnrurlshow" while examining vulnerabilities.Naenara says "mailto" or "cal" When handling a request, I mistakenly assume that the URI argument is a registered URI handler. "" Since Naenara does not sanitize such a URI request, it can easily execute code by passing an illegal request to the nnrurlshow binary. I will tell you.
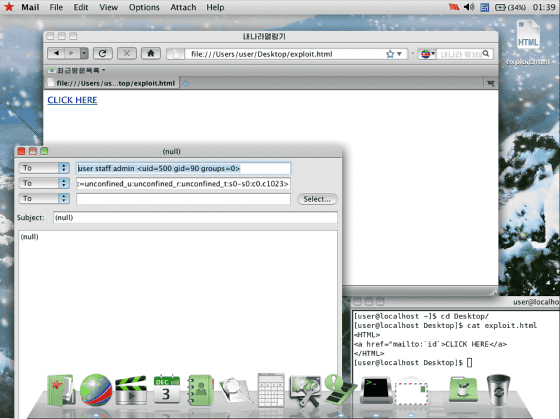
In addition, in 2015According to WhiteHat Security article, Naenara's comfort is that "the menu reminds me of the browser I used 5 years ago."
Related Posts:






