An ad block avoidance service is hacked by a hacker and malware delivery

ByChristiaan Colen
A service that displays "unobtrusive advertisements" to website viewers using ad block, and provides analytics to users free of chargePageFair"Suited hacker attacks, the Web site was hijacked, and the user who tried to use the service as usual was exposed to the risk of malware.
Hackers use anti-adblocking service to deliver nasty malware attack | Ars Technica
http://arstechnica.com/security/2015/11/hackers-use-anti-adblocking-service-to-deliver-nasty-malware-attack/
Halloween RAT: NanoCore Served Via PageFair Service | News from the Lab
https://labsblog.f-secure.com/2015/11/02/halloween-rat-nanocore-served-via-pagefair-service/
Halloween Security Breach | Inside PageFair
http://blog.pagefair.com/2015/halloween-security-breach/
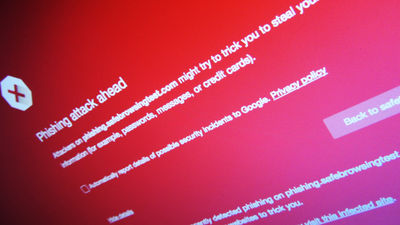
Hacker's attack started on October 31, which is a bit too halloween.Spear phishingEventually, the attacker accessed PageFair's content distribution network account, reset the password, and rewrote PageFair's JavaScript code. As a result, after about 90 minutes, PageFair is placed under hacker control, people visiting PageFair's user page are skipped to page 501 and a pop-up window appears saying "Please update Adobe Flash" It is urged to install Malware simulating Adobe Flash.
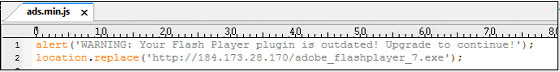
JavaScript that was actually reworked looks something like this.
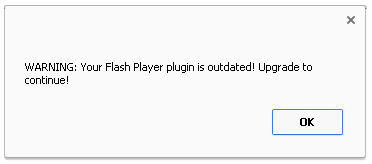
On page 501 the following popup window was displayed.
Shawn Branchfield, CEO of PageFair, said: "It is natural for people using our free analytics service to be disappointed and frustrated by this situation, so PageFair's analysis service I was exposed to the risk of hackers using malicious JavaScript.I'm very sorry that this kind of situation occurred and I guarantee to users that the same situation never happens again.
Security provider'sF-SecureAccording to this attack, this attack uses "Nanocore" malware. Since Nanocore only infects Windows-equipped machines and is detected when using antivirus software, the person who actually installed software installed 2 to 3% of people who were skipped on page 501, It seems that it has stayed at about 500 people.

ByEmma Brabrook
The case in this case seems to be an example showing that "There is a danger of hackers' attack even if you visit a website you know well."
Related Posts:
in Security, Posted by darkhorse_log