Sharing 'hash list' so that Google, Twitter, Facebook etc automatically block violating images for eradicating child pornography

ByFranie Frou Frou
Google / Twitter · Facebook · Microsoft · Yahoo! which each have a huge SNS and search service One of the world's leading IT companies such as "for the purpose of eradicating child pornographic images"Hash listIt was revealed that it shares it.
Hash List "could be game-changer" in the global fight against child sexual abuse images online
https://www.iwf.org.uk/about-iwf/news/post/416-hash-list-could-be-game-changer-in-the-global-fight-against-child-sexual-abuse-images-online
Facebook, Google and Twitter block 'hash list' of child porn images - Telegraph
http://www.telegraph.co.uk/technology/internet-security/11794180/Facebook-Google-and-Twitter-to-block-hash-list-of-child-porn-images.html
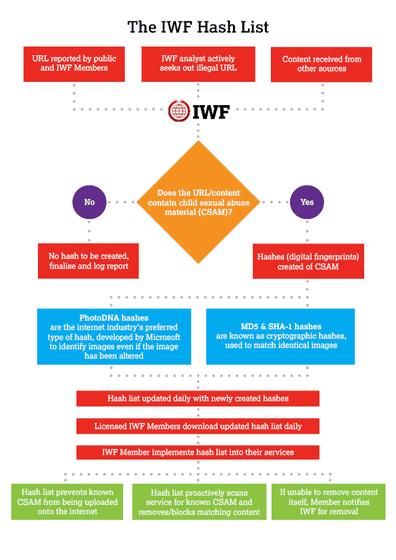
Internet Monitoring Foundation(IWF) has collected tens of thousands of child pornographic images so far. These are assessed by highly trained analysts and are known as "fingerprints in the digital world" by running special codesHash valueIs determined.
A system that automatically detects the same hash value on the Internet by applying the hash value of accumulated child pornographic image and automatically blocks everything recognized as a child pornographic image is currently under development . The same system has already been used for copyright protection in Dropbox, Google and others.

ByMike Licht
IWF announces that it will soon release the "hash list" of child pornographic images gathered by the group to IT companies for the purpose of blocking specific images from the hash value. In addition, it also reveals that the child pornographic image identification system applying the hash value developed by Google is widely shared by other IT companies.
If a system in which child pornographic images are automatically blocked is introduced in full scale, Google · Twitter · Facebook · Microsoft · Yahoo! Even if you attempt to publish child pornographic images on services provided by such as, you will be blocked automatically. Also, since copy images other than the original image also contain the same hash value, it means that they can be blocked at once.
"IWF's hash list plays a truly important role in battle to eradicate child pornographic images on line.This system recognizes and deletes images instantaneously and that child pornographic images are uploaded on the internet I will prevent it, "said Suzie Hargreaves, chairman of IWF. According to IWF, the hash list can be used to detect child pornographic images on storage services, upload services, image search services, filtering services, SNS, chat, data center and any other services.
Conceptual diagram showing how the IWF hash list works
Related Posts:
in Web Service, Posted by logu_ii







