It is a vulnerability to be hijacked by merely receiving MMS on 95% of Android terminal, and measures are taken

Zimperium zLabs Joshua Drake found a vulnerability that is highly dangerous that it would be possible to take over the terminal even if the other party did not open the message if it sent a video message. It is equivalent to 95% of Android OS-equipped smartphones and tablets, and it is said to be 950 million if you fix it.
Experts Found a Unicorn in the Heart of Android - Zimperium Mobile Security Blog
http://blog.zimperium.com/experts-found-a-unicorn-in-the-heart-of-android/
This is a media player framework used by Android "StagefrightVulnerability. For example, a video message is sent to the target terminalMMSIn this case, if you receive MMS, the attack succeeded as well. Since it is also possible to erase the sent message itself, even if the state that "MMS reception notice that I do not remember is displayed but the message itself has not reached anywhere" is already said that the terminal is under attack There is a possibility.
That is,Spear phishingIt does not even need the operation of "the victim opens a PDF file and opening a link", and unilaterally exploits the vulnerability while sleeping to make an attack, and before it awakens, Even erasing it is possible.
A case example of Mr. Drake's attack is as follows. First of all, MMS reception notification saying "video was sent in Hangout" is displayed on the lock screen. The point to note is that at this point the attacker can execute arbitrary code.

When you receive images and videos with MMS, a preview is displayed, but this also triggers code execution.
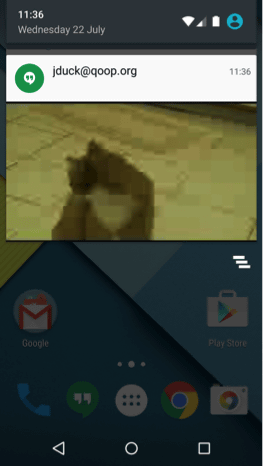
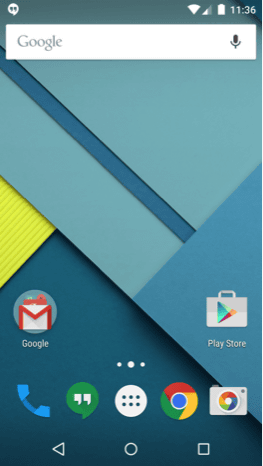
Even if you unlock it as "What's coming," there is no particular change.
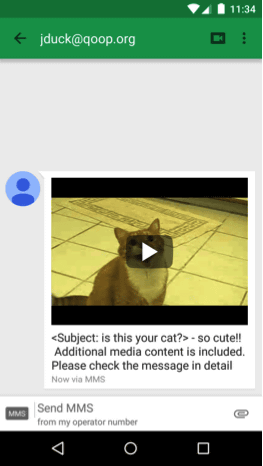
And I will open the video that I received with MMS. Then, when the message is opened, when the video is played, and the code are repeatedly executed.
Since this "Stagefright" media player framework has been introduced from Android 2.2, if it is an Android 2.2 or later terminal, it may be vulnerable in Android 5.1.1 as shown in the image above. The Android 4.1 and earlier terminals which account for 11% of the Android terminals currently on the market are particularly dangerous.
Zimperium reported a vulnerability to Google as of April and Google already received the information and provided the patch to the manufacturer. It seems that ASUS has already distributed patches for Zenfone 2.
I got a report that the ASUS Zen Phone 2 is patched already. Great job@ ASUS@ ASUSUSA! Anything else patched?
- Joshua J. Drake (@ jduck)2015, July 28
Twilio's Greg Baugues wrote the current countermeasure method, but what I can do for the moment is "Do not receive MMS automatically".
Posted by Greg Baugues on July 27, 2015 in Tips, Tricks & Sample Code
https://www.twilio.com/blog/2015/07/how-to-protect-your-android-device-from-stagefright-exploit.html
For example, if you are mainly using Google Hangouts, first launch the application, tap the hamburger icon and tap Settings.

Tap "SMS"

If you uncheck "Automatic acquisition of MMS" on the lower side OK.

If you are using a messenger, tap the icon in the upper right and tap "Settings".

Tap "Advanced settings"

It is OK by turning "Auto acquisition" off (toggle switch on the left).

This method is not a fundamental solution simply by saying "It will not receive MMS automatically", so it is a place where as soon as possible a patch release is awaited. Until then, refraining from using the terminal seems to be the only countermeasure.
Mr. Drake said about the matter on August 5Black Hat USA 2015, And August 7DEF CON 23I am planning to talk with you.
· Continued
Only 95% of what Android clicks on Twitter link - Respond to "Stagefright" attacks taken over by simply playing video - Beginning with GIGAZINE

Related Posts:
in Software, Smartphone, Posted by logc_nt