What does "Internet anonymity" bring to the world?

ByGirl_onthe_les
There are several services like real face names and names on the Internet like Facebook, but contrary to it there is no way that anyone in the real world made actions on the internet There is also technology to keep "anonymity" as it is. The BBC reports on how the anonymity is kept on the Internet, and what kind of influence will appear in the real world, where is the technology to keep this anonymity from the very beginning.
BBC News - Horizon: The defenders of anonymity on the internet
http://www.bbc.com/news/technology-29032399
According to MM Research InstituteShipment volume of domestic mobile phone handsets in 2013Was 39.29 million, of which the number of smartphones was 29.28 million, accounting for about 75% of the total. It is estimated that this ratio of shipments of smartphones will rise year by year, and it is expected to reach about 80% in fiscal 2017. In this way, regardless of where we look now, mobile phones are becoming smartphones, but with this popularization of smartphones, communication tools such as Skype have been explosively developed for Twitter, Facebook, LINE.
It is a modern society that these people can easily communicate with others no matter where they are, but it has become obvious that the US government intercepted such communication for more than five years.
What is the secret system "PRISM" that can peep directly at personal information on servers such as Google, Apple, Yahoo! and others? - GIGAZINE

Dr. Joss Wright working at the Internet laboratory at the University of Oxford said, "If there is information, we can predict what we will do in the future, and whether the information is original It is a very troubling point, sometimes giving power to someone regardless of whether it was originated with such intention, "said the US government who gathered all the information exchanged on the Internet I was talking about how horrible what I was doing.
Also, at the present time that every piece of information flies over the Internet from e-mail, voice chat, video chat, etc., personal lives are deeply connected with the Internet, and this analysis makes it possible to predict more accurate than ever I also point out that it is possible.

ByJustin Norman
◆ Fostering anonymity on the Internet
Outside of some communities, the name "David Chaumu" may not be so famous. However, Mr. Chaum is famous among computer scientists as one of the great visionaries of modern science.
Leaked the presence of a secret system "PRISM"Edward SnowdenIt has been found by Mr. USA that the National Security Agency (NSA) and the British Government Communications Headquarters (GCHQ) were interrogating large-scale information by intercepting communications, but in the early 1980's the Berkeley University Mr. Chaum, who served as a computer scientist, predicted that "computer networks all over the world will enable massive group surveillance."

By* Sax
Mr. Chaum seldom seems to accept an interview, but BBC'sHorizonSucceeded to interview exclusively. In the interview, Mr. Chaum said, "This is sad for me, but it is not surprising that privacy issues on the Internet became a big problem.Around the beginning of the 1980s, I already wrote about this in my own publication. "
Mr. Chaum is outstanding not only because he merely predicted privacy concerns on the Internet but also a system prototype that makes it difficult for information to be gathered by the surveillance system causing privacy problems I developed it myself.
The best example is "Mix NetworkWhat is called. This is an encryption method to hide the identity of the user without encrypting the message content, shuffle the sender's information with the proxy server "Mix" so that tracking of the routing protocol becomes difficult, It sends it to the node. This makes it difficult to identify the source and destination of communication using the Mix Network. As Mr. Chaum himself recognizes, this is a paradigm shift and has a major impact on the next generation of encryption technology.
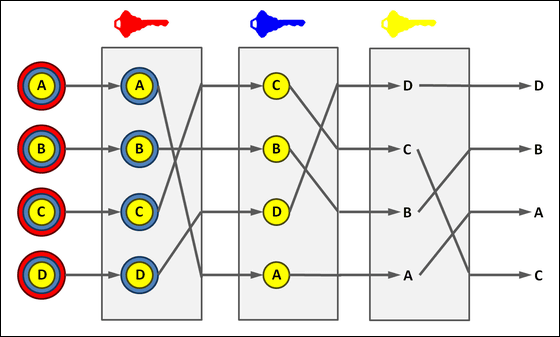
Due to his extraordinary insight, Mr. Chaum is called "a parent of nurturing anonymous communication" from the surroundings, and while there are many other encryption technologies, his encryption technology is anonymous communication technology Famous asTorIt seems that it is also becoming the basic principle of (Toa). This Tor software is a research facility of the US NavyU. S. Naval Research LaboratoryIt was born in a project led by NRL (NRL), which enables browsing while keeping anonymity on the Internet. If it is used, it becomes an important tool for Syria, Iran, China and other dissidents because it enables activities on the Internet without specifying individuals.
However, in areas such as the US and Europe, the usage that the US government initially assumed was not started.
◆ What the "anonymity" on the Internet brings to the real world
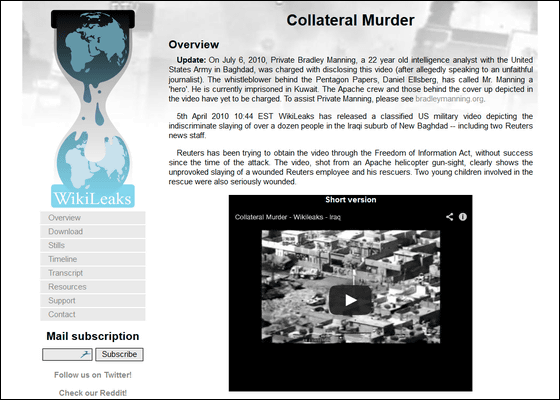
That "how to use" is to publish information on government agencies such as the US government to the public. Actually in 2011, Bradley Manning, an information analyst at the US military, uses Tor to leak confidential information of the military to Wikileaks, which is considered one of the biggest internal accusations in history I will.
Among the information leaked to Wikileaks by Mr. Manning was a recorded movie in which the US military aimed at ordinary people including two reporters of Reuters in Baghdad from Apache and killed 26 people from 18 people and this is the state power and gigantic We have made the position of the media called Wikileaks revealing secrets about companies firm.
On the following pages you can actually watch recorded movies.
Collateral Murder
It is the founder of such WikileaksJulian AssangiMr. Exile has now exiled to the Embassy of Ecuador to avoid arrest and forcible repatriation due to rape charges. When Horizon interviewed Mr. Assangi, Tor said that Tor was the technology he had been looking for before, "Tor was looking for for years, which can give freedom and anonymity to individual communications," I will.
Tor can hide the identity of the user from the traffic, "Tor is the first anonymous protocol that can balance rights," Asanji said. And due to the anonymity brought by Tor, many activists like Mr. Jacob Applebaum are taking action, such as using Wikileaks and Tor to reveal government secrets.
Technologies for maintaining anonymity such as Tor can be potential breakwaters such as government monitoring. But sometimes it helps the bad side of the Internet, for exampleSilk RoadAt the dark site like Tor, trading of banned drugs and various illegal acts have been repeated using Tor. Troels Oerting, a leader at Interpol's Cybercrime Division, which actually cracks Internet-related crimes, said, "Our clearedness rate is falling."
◆ Risk free crime
Apart from discussions on illegal acts on the Internet, we need to develop new technologies to make the Internet that we use everyday "more robust to surveillance", encrypt any data exchanged over the internet We need to be able to do it, BBC says.
Mr. Snowden said, "Encryption is a"Defense technique against dark magic"BBC is also preaching the importance of" encryption "as a minimum necessary for modern people to protect themselves.

ByEd Yourdon
Related Posts:
in Note, Posted by logu_ii