Three basic knowledge for using the net in "anonymous"

BySeq
Japanese internet is highly anonymousIt is said that it was based on the issue of whether to issue his or her real name to the end. By tracking the connected server and IP address, identification of individuals is possible to a certain extent.
Even if it is not a big talk so far, when you do not want your parents and brothers to see the connection history of PCs that your family shares, you do not want to leave your own action history on the net surprisingly There is. I would like to give you basic knowledge to use the net without leaving traces of yourself if you knew at such time.
Gadgetbox - How to create a fake identity and stay anonymous online
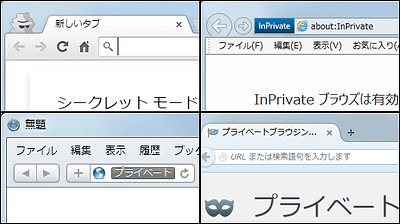
1: Use private mode of browser

Browsers such as Google Chrome and Firefox can use "Private Mode" which does not record browsing history or download history at all. In widely used browsers, you can switch modes with shortcut keys. Google Chrome and OperaCtrl + Shift + N, Firefox and Internet ExplorerCtrl + Shift + PYou can switch with.
2: Proxy server and VPN
ByAswirlymatrix
Even if you are using private mode,DNS (Domain Name System)Caches, cookies, etc. are recorded on the computer. If you do not want to keep your activity history on the web at all, you can make it look like a completely different person's access by letting it go through the Proxy server. Originally when you are connected to the Internet via Proxy server,Anonymous proxy site available from browserBy using, it is possible to disguise the original access location.
VPN (Virtual Private Network)By using virtual private network, by accessing servers and systems providing VPN service from the Internet, it can be used from the Internet in an environment similar to that of office dedicated lines or the like even from the outside or from home It refers to network service.
When connecting to the internal environment from the outside of the company, work such as releasing the firewall port was necessary in the past. By using VPN, it is possible to connect from the outside in the same environment as inside the company with the shortest distance. As the easiest way, use the service of the company that provides VPN. It is necessary to put the client software in the PC. By doing this, you can connect to the environment of the service provider by VPN connection using the Internet network.
3: Disposable e-mail address
 >
>
ByChidorian
A disposable email address is useful when you register for services that you do not intend to continue using, or when you need to contact someone who is somewhat unreliable. There are various services that provide disposable e-mail addresses, such as previously posted. Many software abroadFull-text display, 15-minute limited e-mail address "Quick Mail" corresponding to attached fileSome of them are compatible with Japanese as well.
Recently, it is not a dedicated service like the one mentioned above, but you can make double account as a function of web mail.Alias function of Gmail, You can create multiple accounts hanging from this account. By utilizing this function, it is possible to register multiple accounts on a net mail order site that is not supposed to be used continuously, and receive mails addressed to that address with this account.
◆For anonymous use, double-edged sword

ByAfu007
It is surprisingly difficult to use the Internet with all information anonymous even if we have taken measures to this point. It seems that it is quite difficult to think that a method of conducting online shopping without entering an address, name, etc., is quite difficult.
Some people may have noticed by looking at the above method, but these methods are the same as those used for crime, fraud, etc. However, there is also the word "knowledge is power", it is up to the person to exploit such knowledge or to use it in a good direction. You can not defend yourself when it is embarrassing if you avoid sharp content that can be exploited. Even if you do not actively use it yourself, it is meaningful to know.
Related Posts:
in Note, Posted by darkhorse_log