Windows Notepad vulnerable

A remote code execution vulnerability has been discovered in the Windows Notepad application. Microsoft has announced that it has rated the vulnerability as 'Important.'
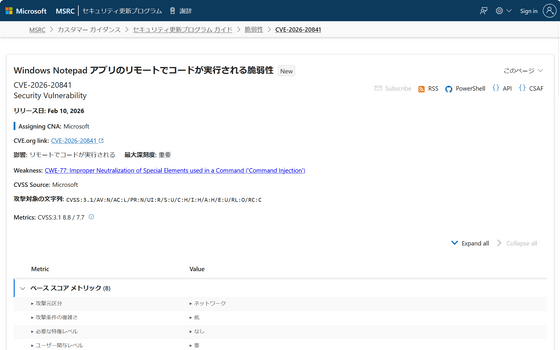
CVE-2026-20841 - Security Update Guide - Microsoft - Windows Notepad App Remote Code Execution Vulnerability
Thanks to Microsoft adding all those extra features to Notepad, it now unfortunately sports one more: An exploitation vulnerability with a high security rating | PC Gamer
By exploiting the Notepad vulnerability, an attacker could trick a user into clicking a link in a Markdown file opened in Notepad, causing the application to launch an unverified protocol to load and execute a remote file.
This allows the attacker to collect data or perform other malicious actions on the computer, and if the user has administrative privileges, the attacker also has those privileges.

Microsoft has disclosed the issue as CVE-2026-20841, and it has a Common Vulnerability Scoring System (CVSS) base score of 8.8 and a time-lapse score of 7.7, making it a 'high' security issue. A patch has already been completed, and the fix will be applied by applying the February 2026 Windows Update.
This type of vulnerability requires that the computer is connected to a network for an attacker to gain remote access, and it only works if the user opens a Markdown file and clicks on a link within it. This is why it's important not to download files whose origin you can't verify, and never click on links you don't know.
Markdown support in Notepad began in 2025. Technology media PC Gamer criticized, 'Given the simplicity of this issue, Microsoft should have anticipated this possibility before blindly expanding Notepad's functionality.'
Windows 11 Notepad finally supports formatting and Markdown, and you can revert to pure Notepad in settings - GIGAZINE
Related Posts: