How Tailscale makes it easy to build a secure VPN network
As remote work becomes more common, secure and efficient network access is becoming increasingly necessary. Tailscale founder
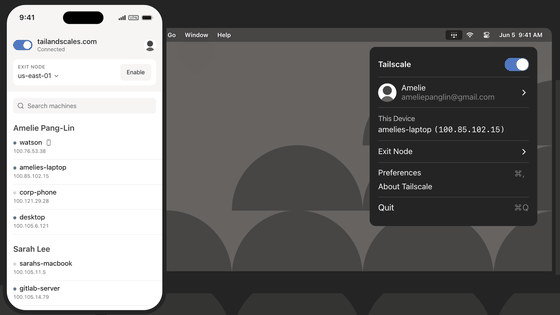
Tailscale: How it works
https://tailscale.com/blog/how-tailscale-works
◆Network infrastructure: WireGuard
Tailscale is based on the open-source WireGuard package, specifically its user-space Go implementation , WireGuard/wireguard-go . WireGuard creates extremely lightweight encrypted tunnels between computers, virtual machines, and containers called 'nodes.'
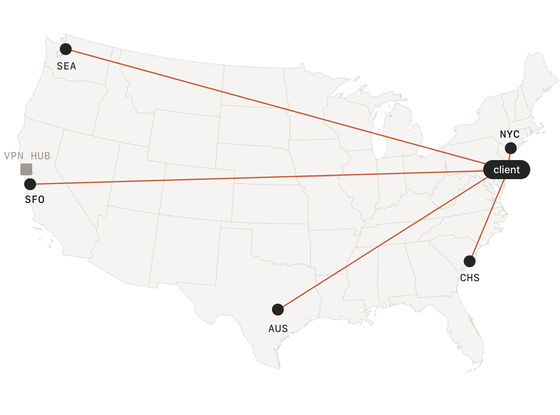
Hub-and-spoke network
Traditional VPNs use a 'hub-and-spoke' architecture, where each client device (such as a laptop) connects to a central 'concentrator' or VPN gateway.
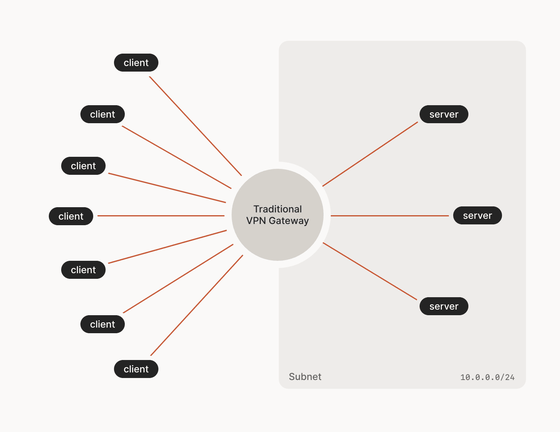
Hub-and-spoke works well, but it has its drawbacks. Typically, companies configure a single VPN concentrator and then set up secondary tunnels, but this can be difficult to scale. First, remote users may be close to or far from the VPN concentrator. If they are far away, they experience high latency when connecting. Second, the data center they want to reach may not be close to the VPN concentrator. If they are far away, they again experience high latency.
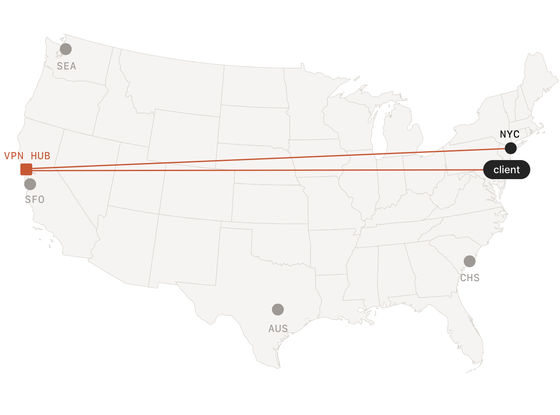
Because WireGuard creates lightweight tunnels, you can create a multi-hub setup without much trouble. The only problem is that each node needs a static IP address, an open firewall port, and a set of WireGuard keys. If you add more users or servers, you need to distribute new keys to all clients and servers.
◆Mesh network
In a hub-and-spoke network, individual nodes cannot communicate directly with each other, but there is a format that allows computers to exchange files directly with each other without using the cloud. A configuration in which all nodes are directly connected to other nodes is called a 'mesh network.'
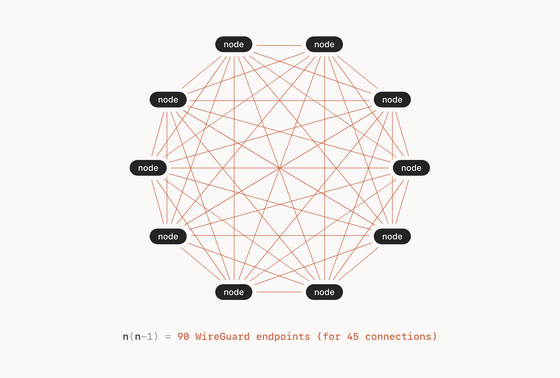
Mesh networks allow for efficient peer-to-peer application design, but a 10-node network requires 10 x 9 = 90 WireGuard tunnel endpoint configurations. Every node needs to know its own key plus nine additional keys, and every time you update a key or add or remove a user, you must update each node. Furthermore, nodes must somehow find each other. User devices rarely have static IP addresses, and public facilities like cafes, hotels, and airports don't allow for easy port openings behind firewalls. If your company has compliance requirements, you need the ability to block and audit traffic between all nodes.
◆Control plane: key exchange and reconciliation server
To create a mesh network, you use the Tailscale node software and interact with login.tailscale.com, which acts as a coordination server , similar to the hub-and-spoke model, but whose sole role is to exchange encryption keys and set network policy.
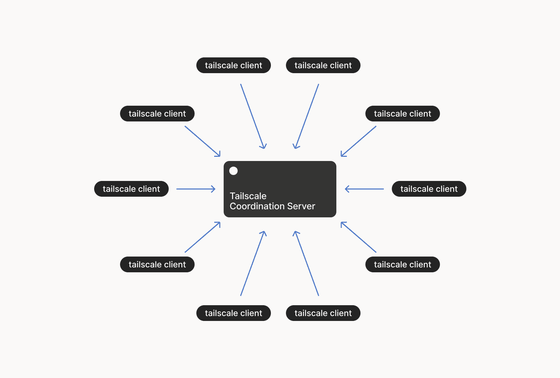
While traditional VPN concentrators centralize both management and data transfer, limiting performance, Tailscale's data processing capacity scales with the number of nodes.
Each node generates a random public/private key pair for itself and associates the public key with its identity.
It connects to a coordination server and creates a list of public keys and where the nodes currently reside.
Download the public key and address list.
Configure your WireGuard instance with the appropriate set of public keys.
Unlike hub-and-spoke networks, no unencrypted packets are sent, so their contents cannot be analyzed and leaked.
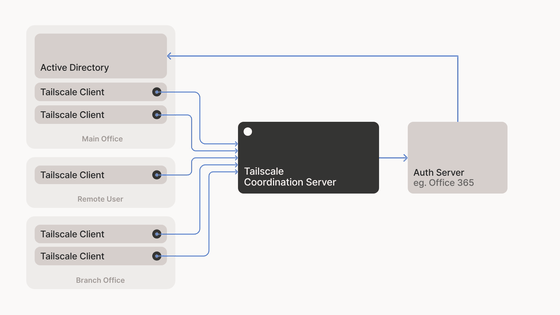
◆Login and two-factor authentication
The decision of which public key to send from the reconciliation server to which node is made through authentication to the reconciliation server. By outsourcing authentication to OAuth2, OIDC (OpenID Connect), or SAML providers such as Gmail, G Suite, and Office 365, Tailscale does not need to store user accounts or sets of certificates, allowing it to operate a highly reliable service while minimizing personally identifiable information.
Tailscale also activates instantly the moment you log in. For example, when you download the macOS/iOS app from the App Store and log into your account, it instantly creates a secure key dropbox for your domain and allows you to exchange public keys with other devices in the associated account/domain. Each node configures WireGuard with ultra-light tunnels to each of the other nodes, and you instantly have a mesh network.
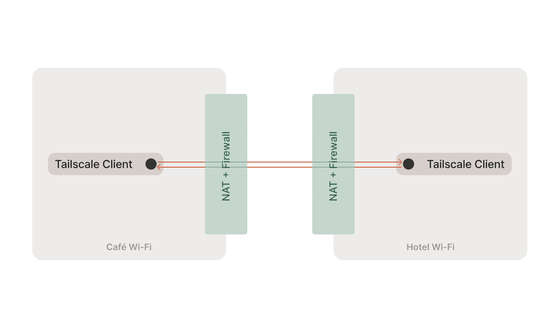
◆NAT traversal
Even in challenging environments such as those without static IP addresses, open ports, or overlapping NATs, Tailscale uses highly advanced
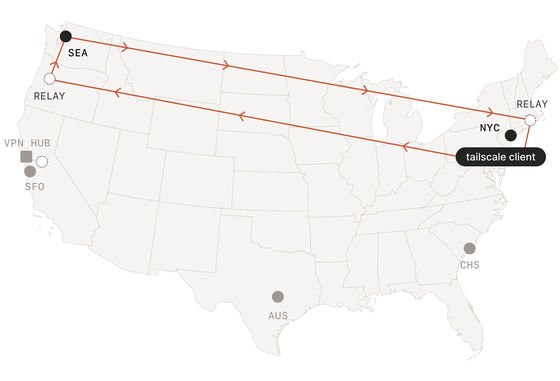
◆Encrypted TCP Relay (DERP)
Some even more stringent networks block UDP entirely, making it impossible to traverse using STUN and ICE, so Tailscale offers a network of DERP (Designated Encrypted Relay for Packets) servers , which perform the same role as ICE-standard TURN servers but use HTTPS streams and WireGuard keys instead of the traditional TURN recommended method.
◆ACL and security policy
Tailscale allows security policies to be stored in a central location on a coordination server and automatically distributed to each node, enabling central control of policies while still allowing efficient, distributed enforcement.
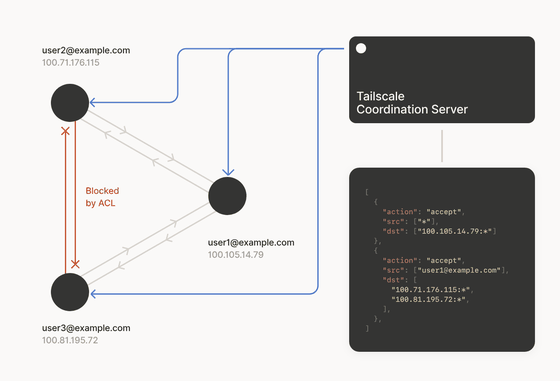
At a more granular level, the coordination server protects nodes by giving each node only the public key of the node it wants to connect to. This is an extremely powerful protection model, as other computers cannot decode encrypted packets or even request a connection. It prevents virtually any kind of protocol-level attack. As a result, Tailscale is particularly good at protecting legacy, non-web-based services that no longer receive updates.
◆Audit log
Tailscale allows each node to asynchronously log all internal network connections to a logging service on the coordinating server. Because logging occurs on both the source and destination machines, the logs are extremely difficult to tamper with. Tailscale's logging service has a controllable retention period and only logs metadata about how connections are established, not activity history or personal information.
◆ Phased deployment
Tailscale is also suitable for phased deployment: simply install the Tailscale node software on two devices and log in to both devices with the same user account or authentication domain. It runs on top of your existing network, allowing you to deploy securely without disrupting your existing infrastructure and security setup.
◆Zero Trust Networking
The end result will be what we call ' zero trust networking ,' a network that secures communications by always authenticating each other, safely eliminating older or unencrypted access methods.
Related Posts:
in Software, Web Service, Posted by darkhorse_logmk