How does stolen credit card data end up in Apple or Google wallets?
There are many cases all over the world where people have leaked confidential information, including credit card numbers, to third parties and fallen victim to fraud. Krebs on Security, a security news site, has introduced how this information is leaked.
How Phished Data Turns into Apple & Google Wallets – Krebs on Security
If you have a smartphone, you have likely received an SMS message saying something like, 'We came to deliver your package, but you were not at home,' or 'You have an unpaid bill.'
According to Krebs on Security, phishing messages impersonating the U.S. Postal Service are likely to be sent through phishing kits sold by Chinese cybercriminals. Krebs on Security warns that if you access a phishing site via a message sent through such a kit, you risk having confidential information stolen.

According to Krebs on Security, these sites use several innovative techniques to maximize the victim's data: For example, a visitor may enter their information and then stop before hitting the 'send' button, but the site captures what is typed into the fields in real time, meaning that the information can be wiped even if the visitor never hits the send button.
If a person unsuspectingly submits their credit card number, they receive a one-time password from the financial institution to verify their identity, and then enter it into the website. The scammers then link this information to mobile wallets from Apple or Google, and sell the smartphones with the linked information in large quantities for several tens of thousands of yen each.
In addition, it has been confirmed that the scammers display a message saying 'Your card could not be processed' and urge the victim to use a different card, resulting in the theft of multiple pieces of information from each victim.
According to Ford Merrill, an employee of the Center for Strategic and International Studies, a US think tank, Chinese fraudsters are using several techniques to scam people, such as creating phishing sites that store information 'securely' so that it can be retrieved later even if the site is shut down, or sending spam messages using mass-created Apple and Google accounts.
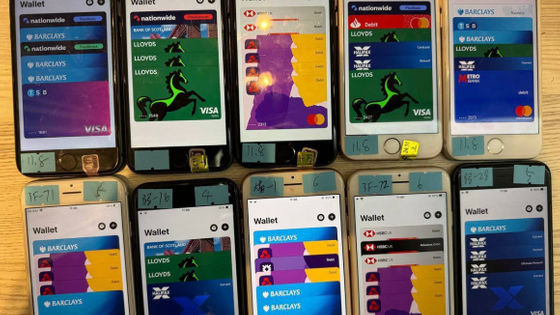
The latter is all done by hand, with images circulating of large numbers of smartphones being installed on racks.

Another technique involves taking an image of the stolen card details. When the image is scanned by an iPhone, the iPhone cannot distinguish whether the image is real or fake, so the card details can be added to the wallet without any hindrance. All that is left to do is receive a one-time password from the victim, and the takeover is complete.
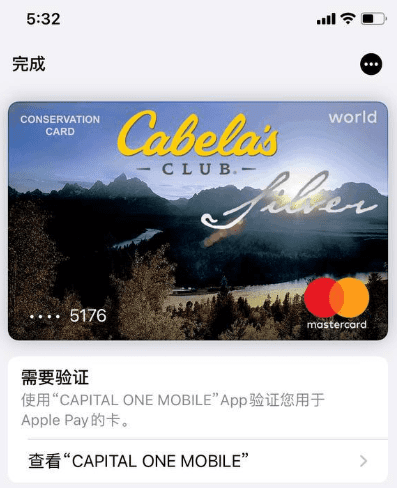
According to Merrill, when Chinese criminal groups first began to operate in earnest around 2023, users had to wait 60 to 90 days before they could sell or use a smartphone linked to someone else's information for fraud purposes. But two years later, that wait time has shrunk to around seven to 10 days.
According to a survey by security firm Resecurity, a Chinese phishing kit has collected 108,044 credit card details from 31 domains. Merrill pointed out that 'each mobile wallet card is expected to result in a loss of $100 to $500,' and estimated that overall, the fraudulent charges amounted to about $15 billion a year.
Krebs on Security points out that 'in the United States, the adoption of touchless payments has accelerated since the outbreak of the COVID-19 pandemic, and many financial institutions have rushed to easily link payment cards to mobile wallets. The authentication requirement for this was to send a one-time code to customers via SMS by default,' and adds that experts 'continued use of one-time codes has contributed to this new wave of card crime.'
Google is reportedly planning to phase out sending one-time SMS codes as a two-factor authentication tool for Gmail in order to mitigate the impact of SMS abuse.
Google is replacing Gmail's two-factor authentication with QR codes instead of six-digit authentication codes - GIGAZINE

Related Posts:
in Note, Posted by log1p_kr







