Could the surge in SMS phishing spam be due to new features in China's popular phishing kit?

In the United States,
Chinese Innovations Spawn Wave of Toll Phishing Via SMS – Krebs on Security
https://krebsonsecurity.com/2025/01/chinese-innovations-spawn-wave-of-toll-phishing-via-sms/
During the second week of January 2025, the Massachusetts Department of Transportation (MassDOT) warned users to be on the lookout for a new SMS phishing scam targeting users of MassDOT's electronic toll collection program, EZDriveMA, in which users are asked to enter credit card data and ultimately provide a one-time password sent via SMS or a mobile authentication app.
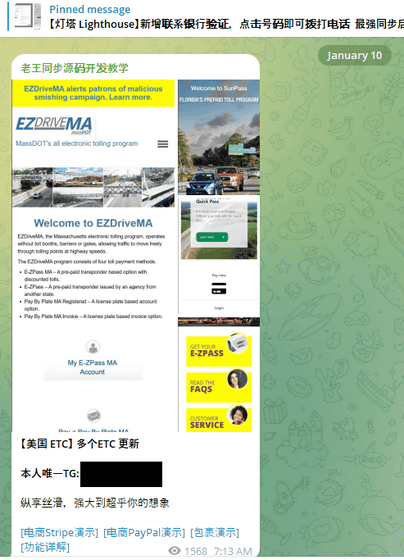
Around the same time that MassDOT issued its warning about the existence of SMS phishing (
In Texas, a smishing scam that claims 'you have unpaid tolls with the North Texas Toll Department' is becoming popular, and Krebs on Security has received reports of similar phishing messages from California, Colorado, Connecticut, Minnesota and Washington.
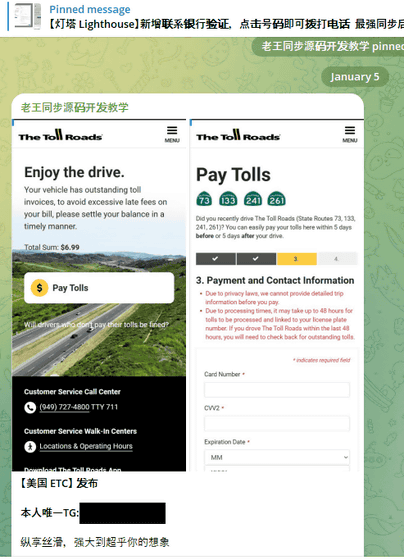
The following screenshot shows a phishing site created for users of The Toll Roads in Orange County, California.
Ford Merrill, a security analyst at SecAlliance , a division of the CSIS Security Group , reports that the volume of phishing messages impersonating toll road operators has skyrocketed since a Chinese cybercrime group known for selling sophisticated smishing kits began hosting phishing pages impersonating at least one U.S. toll road operator.
Merrill said the Chinese cybercrime group has hundreds or even thousands of clients selling different smishing kits that steal enough information from victims to add their credit cards to mobile wallets for online shopping or money laundering.
One of the problematic smishing kits is the commercial phishing kit 'Lighthouse.' Lighthouse added new features on January 10, 2025, and it seems that phishing messages began to increase sharply in the United States at this time. Krebs on Security explains that Lighthouse's new features are to faithfully mimic specific websites, and what is noteworthy is that 'websites will not load phishing pages unless they detect that the visitor is accessing them from a mobile device.'
While smishing kits themselves are nothing new, Merrill said Chinese smishing groups have been able to more seamlessly integrate their spam messages with Apple's iMessage and Android's RCS , which has revolutionized deliverability. Merrill pointed out, 'Traditionally, smishing kits have relied heavily on SMS to deliver messages, but recently they have been using iMessage and RCS more frequently because they can't be filtered by carriers and have a higher success rate.'
It is unclear how attackers select targets for smishing, but MassDOT warns that 'the target phone numbers appear to be randomly selected and not uniquely associated with accounts or toll road usage.' In fact, one Krebs on Security user reported that he was smishing even though he does not own a car.
Krebs on Security recommends ignoring or deleting smishing messages and warns against visiting phishing sites, while the Federal Bureau of Investigation (FBI) recommends filing a complaint with the Internet Crime Complaint Center (IC3) before deleting the messages.
Related Posts:
in Security, Posted by logu_ii