Hackers claim they stole 87 million customer records from Temu, a claim Temu denies

by
A threat actor has leaked some of the data on a hacking forum, claiming to have stolen 87 million customer records from Temu, a Chinese online marketplace. The threat actor claims to have successfully infiltrated Temu's systems, but Temu denies the intrusion, saying this is not true.
Temu denies breach after hacker claims theft of 87 million data records
https://www.bleepingcomputer.com/news/security/temu-denies-breach-after-hacker-claims-theft-of-87-million-data-records/

On September 16, 2024, a threat actor going by the name 'smokinthashit' posted on the underground forum BreachForums that he had stolen 87 million records from Temu and was seeking buyers for the data.
The threat actors have released samples of data as evidence, including usernames, IDs, IP addresses, names, dates of birth, gender, shipping addresses, phone numbers, hashed passwords, and more.
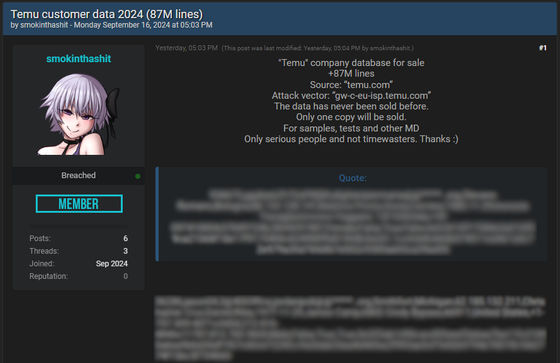
In response to a request for comment from IT news site BleepingComputer, Temu stated that the data did not belong to the company, that the data leak was false, and that it would sue those who spread such false information.
Temu said: 'Our security team conducted a thorough investigation into the alleged data leak and confirmed that the claims are completely false. The data circulating did not originate from our systems and not a single row of data matches our transaction records. We take seriously any attempt to tarnish our reputation or cause harm to our users and reserve the right to take legal action against those who spread false information and seek to profit from such nefarious activities.'
Temu also highlighted its industry-leading data protection and cybersecurity practices, including Mobile Application Security Assessment (MASA) certification, independent validation, a bug bounty program with bug bounty platform HackerOne, and compliance with the Payment Card Industry Data Security Standard (PCI DSS).
Meanwhile, the threat actors have also declared that they have successfully compromised Temu.
When contacted by BleepingComputer, the threat actors said they still maintained access to email and internal panels of Temu's internal systems, claiming that this was due to a code vulnerability.
However, the threat actors did not provide any evidence beyond the sample data, which Temu determined to be fake, and BleepingComputer was unable to determine the authenticity of the intrusion.
BleepingComputer also called for caution, saying, 'If you are a Temu user, it would be wise to enable two-factor authentication on your account, change your password to a new, unique one, and be on the lookout for phishing attacks.'
Following the threat actor's response, BleepingComputer reached out to Temu again, but had not received a response at the time of writing.
September 24, 2024 Update:
According to a contact from Temu's public relations representative in Japan, on September 19, 2024, BleepingComputer updated their article to add the following statement about the threat actor in question: 'He was banned from BreachForums for attempting to falsely sell data that was already public. CheckPointResearch, which is investigating the claim, told BleepingComputer that some of the information posted by the threat actor appears to originate from a data breach at foreup.com dating back to mid-2021.'
Related Posts:
in Free Member, Web Service, Security, Posted by log1l_ks







