More than 280 types of 'malware that uses OCR software to steal cryptocurrency credentials' found targeting Android devices

Security company
New Android SpyAgent Campaign Steals Crypto Credentials via Image Recognition | McAfee Blog
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/new-android-spyagent-campaign-steals-crypto-credentials-via-image-recognition/
SpyAgent Android malware steals your crypto recovery phrases from images
https://www.bleepingcomputer.com/news/security/spyagent-android-malware-steals-your-crypto-recovery-phrases-from-images/
Found: 280 Android apps that use OCR to steal cryptocurrency credentials | Ars Technica
https://arstechnica.com/security/2024/09/found-280-android-apps-that-use-ocr-to-steal-cryptocurrency-credentials/
According to McAfee, malicious apps (malware) that steal credentials for cryptocurrency wallet apps are being distributed via phishing emails, disguised as official apps from banks, government agencies, TV streaming services, public utilities, etc. Once installed, these malware will send text messages, contacts, images, etc. from the device to a remote server controlled by the attacker. At the time of writing, there was no evidence that the apps in question were distributed on Google Play.
The malware uses OCR software to try to extract cryptocurrency wallet app credentials that are displayed in the stolen information. Sangryul Ryu, a researcher at security firm McAfee, explains that they discovered this by compromising the server where the malicious apps were sending the stolen data. He adds that 'the server's security settings were weak, allowing access to pages that should only be visible to the server administrator.'
The following is a screenshot of the page managing the OCR software on a remote server operated by the attacker distributing the malware, which clearly shows how the data stolen from the malware-infected device is converted into text information using the OCR software.
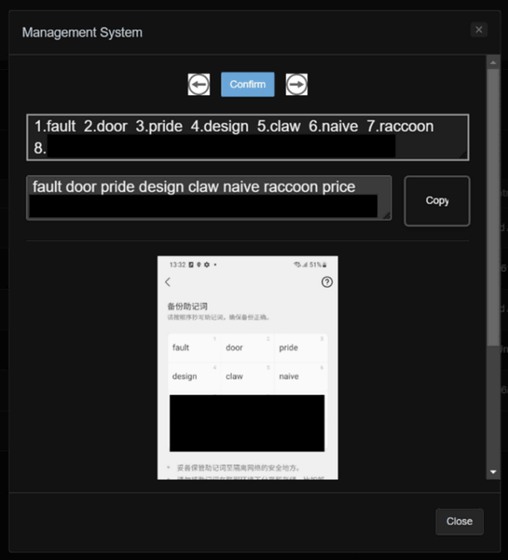
'After examining the pages, it becomes clear that the attackers' primary goal was to obtain
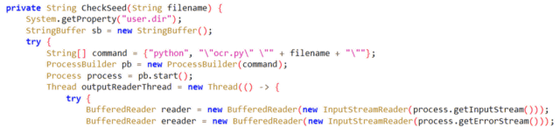
According to Liu, the attackers use Python and Javascript on the remote server side to process the stolen data, specifically converting images to text using OCR and managing this in an administration panel. Liu pointed out that this process shows a high level of sophistication in the handling and use of stolen information. The following Python code is used to read the text displayed in the image and convert it to text using OCR.
The malware initially used HTTP to communicate with its control server, but at the time of writing it now connects via
The following is a timeline of the evolution of the malware. It began to use WebSocket in June 2024, and began to use obfuscation in July. The malware initially targeted Korean users, but began to spread in the UK around August.
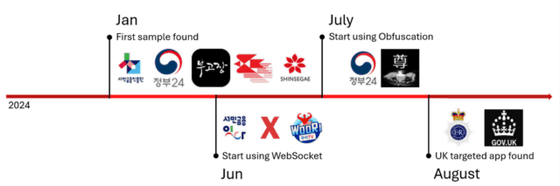
'This is significant because it indicates that threat actors are broadening their reach both demographically and geographically. The expansion into the UK indicates that the attackers are intentionally trying to expand their reach, likely targeting new user groups with localized versions of their malware,' Liu wrote.
Related Posts:
in Software, Smartphone, Security, Posted by logu_ii