It was pointed out that airport and cockpit security could be breached by SQL injection attacks

The Transportation Security Administration (TSA) has a program called 'KCM (Known Crewmember)' that allows pilots and flight attendants to pass security checks even when they are off. Similarly, there is a similar mechanism called 'CASS (Cockpit Access Security System)' that allows entry into the cockpit, and if you are confirmed as a certified pilot, you can use the auxiliary seat in the cockpit. It has been pointed out that this KCM and CASS could be breached by a SQL injection attack.
Bypassing airport security via SQL injection
Bypassing airport security via SQL injection | Hacker News
The flaws were made by Ian Carroll , founder of flight support service Seats.aero , who conducts security research outside of work, and bug hunter Sam Curry.
In April, @samwcyo and I discovered a way to bypass airport security via SQL injection in a database of crewmembers. Unfortunately, DHS ghosted us after we disclosed the issue, and the TSA attempted to cover up what we found.
— Ian Carroll (@iangcarroll) August 29, 2024
Here is our writeup: https://t.co/g9orwwgoxt
The KCM system works simply: you show your KCM barcode at a designated lane, or tell a TSA agent your airline and employee number to verify your employment status. If the authentication is successful, you can enter the restricted area of the airport without going through security.
CASS is a system that allows pilots to use auxiliary seats in the cockpit when they are commuting or traveling and regular seats are not available. Similar to KCM, once the pilot is authenticated, a notification is sent from the gate to the flight crew that the auxiliary seat user has been authenticated by CASS.
A key aspect of either authentication is airline employment verification, and Carroll and his team wondered how KCM and CASS worked, since airlines likely store employee information in different ways.
According to Carroll and others, ARINC, a subsidiary of aerospace company Collins Aerospace, operates core components such as a website for checking the status of KCMs and an API for forwarding authentication requests between different airlines.
While large airlines can build their own systems, this isn't necessarily the case for smaller companies. So Carroll and his team looked into vendors and discovered a site called FlyCASS.com , which sells a web-based interface to small airlines such as Air Transport International.
Carroll and his team thought they couldn't find any more information than that, since only the login pages for each airline were publicly available. But just to be sure, they tried entering a single quote (') into the username as a SQL injection test, which resulted in a MySQL error.
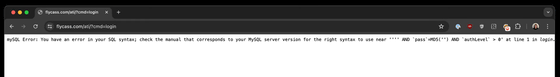
Using this error as a breakthrough, Carroll and his team used sqlmap to discover a SQL injection vulnerability and successfully logged into FlyCASS as an Air Transport International administrator.
FlyCASS provides both KCM and CASS for participating airlines, and when logged in as an administrator, it was possible to manage the list of pilots and flight attendants. In addition, since there were no checks or authentications beyond logging in, new employees could be added freely. When tested using the query function, the test user added by Carroll and his colleagues was approved to use both KCM and CASS.
Carroll and others reported the problem to the Department of Homeland Security on April 23, 2024. FlyCASS was then separated from KCM and CASS, and the problem was fixed. However, while Carroll and others were thinking about how to safely publicize the problem, the Department of Homeland Security cut off contact with Carroll and others, and the TSA denied that Carroll and others had discovered the problem.
The TSA explained that it was now 'screening passengers before issuing bar codes' and removed the reference to manually entering employee IDs, but Carroll and his team confirmed that it is still possible to manually enter employee IDs.
In response to this, the social news site Hacker News has posted comments such as, ' It's not unheard of for security researchers to arrest and imprison those who legitimately point out their own failures, ' as well as comments such as, 'I thought the FBI was going to get involved,' indicating that the Department of Homeland Security and the TSA would not take any serious action.
Related Posts: