More than 6 million personal information leaked from insurance software developer following LockBit ransomware attack; victims negotiated to recover data for 8 million yen but sold it for 10 times the price

Infosys McCamish Systems (IMS), a company that develops software and services related to life insurance, was hit by a ransomware attack, resulting in the personal information of over 6 million people being leaked. The attack on IMS is believed to have been carried out by the Russia-based cybercrime group LockBit.
Notice of Cybersecurity Incident
Office of the Maine AG: Consumer Protection: Privacy, Identity Theft and Data Security Breaches
https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/b152fd39-9f84-4ca5-a149-d20b94ed8ef6.html
Infosys notifies 6 million people about data breach claimed by LockBit ransomware gang - Comparitech
https://www.comparitech.com/news/infosys-notifies-6-million-people-about-data-breach-claimed-by-lockbit-ransomware-gang/
IMS is a software development company based in the United States that provides services to more than 34 insurance companies. On June 27, 2024, IMS reported a data breach to the Maine State Department.
According to IMS's report, IMS was subject to unauthorized access from outside between October 29, 2023 and November 2, 2023, and internally managed information was stolen. In addition, on November 2, 2023, IMS's system was encrypted by ransomware.
After analyzing the details of the unauthorized access, it was found that the stolen data included personal information of 6,078,263 people. The personal information included a huge amount of information such as 'Social Security numbers,' 'dates of birth,' 'medical records,' 'biometric information,' 'email addresses,' 'passwords,' 'driver's license numbers,' 'state IDs,' 'bank account information,' 'payment card information,' 'passport numbers,' 'Tribal ID numbers,' and 'Military ID numbers.'
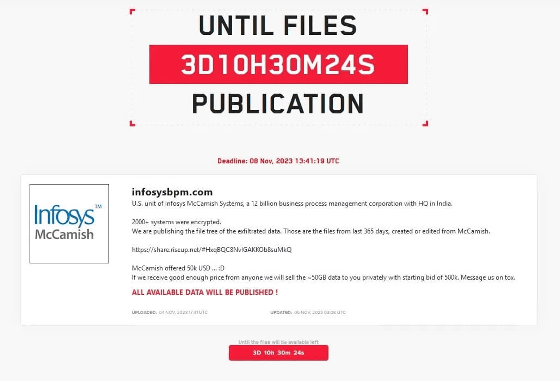
IMS has not revealed the name of the attacker, but on November 4, 2023, the cybercrime group LockBit announced a statement of responsibility for the attack against IMS. LockBit claims to have stolen 50GB of data from IMS, and also claims that 'IMS offered to pay LockBit $50,000 (approximately 8 million yen) to prevent the data from leaking. However, since $50,000 is not enough, IMS will sell the data for $500,000 (approximately 80 million yen).'
The central figure of LockBit was arrested in February 2024, and in April 2024, the FBI announced that it had obtained the decryption key for LockBit ransomware. However, cybercrimes using LockBit ransomware have been confirmed even after the arrest of the central figure of LockBit, and it has been found that LockBit ransomware was also used in the Indonesian national data center breach incident that occurred in June 2024.
Indonesia's national data center hit by ransomware attack demanding more than 1.2 billion yen - GIGAZINE

Related Posts:
in Security, Posted by log1o_hf