A report that a fake VSCode extension was created and downloaded and that a flaw in the VSCode extension system that makes it easy to insert malicious code was also revealed
Microsoft's text editor 'Visual Studio Code (VSCode)' allows you to add functions and customize the appearance by introducing extensions. Security researchers released 'fake extensions that insert code into popular extensions,' and in a short period of time, they were installed on the machines of many users, including large companies and security companies. Security researchers have pointed out flaws in Visual Studio Code's extension system and sounded the alarm.
1/6 | How We Hacked Multi-Billion Dollar Companies in 30 Minutes Using a Fake VSCode Extension | by Amit Assaraf | May, 2024 | Medium
2/6 | Exposing Malicious Extensions: Shocking Statistics from the VS Code Marketplace | by Amit Assaraf | Jun, 2024 | Medium
https://medium.com/@amitassaraf/2-6-exposing-malicious-extensions-shocking-statistics-from-the-vs-code-marketplace-cf88b7a7f38f
3/6 | A Letter to Microsoft: Uncovering Design Flaws of Visual Studio Code Extensions | by Amit Assaraf | Jun, 2024 | Medium
https://medium.com/@amitassaraf/3-6-uncovering-design-flaws-in-the-visual-studio-code-marketplace-ea1d8e8b0171
◆ An experiment to trick users into installing fake extensions disguised as popular extensions
In order to reproduce the attack of 'developing a fake extension disguised as a popular extension and embedding malicious code in the fake extension,' the research team developed a fake ' Dracula Official ' of the popular color theme ' Dracula Official' that has been installed more than 7 million times. Dracula Official was developed by 'downloading the real Dracula Official code, embedding the attack code, and copying and pasting all the marketplace materials,' and it took only 30 minutes from the start of development to publishing it on the extension marketplace.
In addition, since the real Dracula Official had obtained publisher authentication using the domain 'draculatheme.com', the research team obtained a new domain 'd ar culatheme.com' and obtained publisher authentication using d ar culatheme.com. All that was required to apply for publisher authentication was domain authentication.

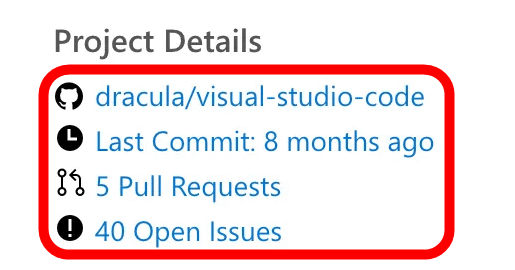
In addition, the extension distribution page can post a 'link to the GitHub repository that manages the extension code,' but this repository information is used as is in the 'package.json' registered in the marketplace, and no association check between the extension and the repository was performed. As a result, the research team was able to post the real Dracula Official repository on the distribution page of the fake Dracula Official.
After obtaining publisher authentication and publishing repository information, the research team inserted code into the fake extension that sends information such as hostname and domain to an external server every time a file is opened in Visual Studio Code, enabling them to obtain the attributes of users who installed the fake extension.
The first person downloaded the extension within minutes of its release. The number of downloads exceeded 100 within a day of its release, and within a few days, it was installed on 'Windows machines of a large company with a market capitalization of $483 billion,' 'machines of well-known companies with market capitalizations of several billion dollars,' 'machines of one of the world's largest security companies,' and 'machines connected to the court network.'
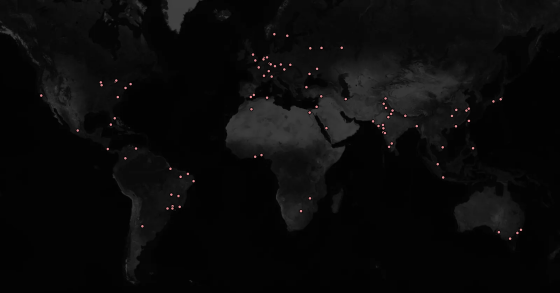
Below is a diagram summarizing the regions where the fake extensions were installed. It can be seen that they were installed all over the world, including Japan. In this case, the extension was a harmless one developed by the research team, but it was shown that extensions containing malicious code can also be introduced to many machines using the same technique.
Issues with the extension system
Based on the results of the above experiments, the research team points out that the problem is that code with various functions can be inserted into an extension that only changes the color theme. Extensions such as Chrome and Firefox have a permission management system, and extensions that require access to files, etc. require explicit permission from the user when installed. However, Visual Studio Code extensions do not have a permission management system like browser extensions, and both 'extensions that only change the color theme' and 'extensions that deploy child processes' can be installed without permission checks. An issue calling for the addition of a permission management system to Visual Studio Code extensions was issued in 2018, but Microsoft has not responded.
[Feature Request] Extension Permissions, Security Sandboxing & Update Management Proposal · Issue #52116 · microsoft/vscode · GitHub
https://github.com/microsoft/vscode/issues/52116
The research team also pointed out that the automatic update of extensions is enabled by default, which is a problem. If many users leave automatic updates enabled, it becomes easier for attacks to spread non-problematic extensions and then install malicious code later.
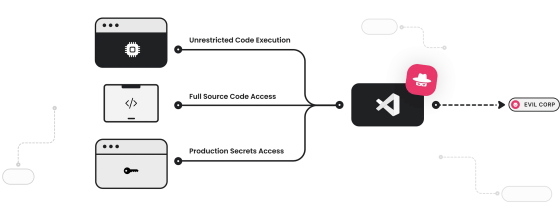
Another problem is that the extension strictly runs as a separate app from Visual Studio Code. Browser extensions basically run within the browser's process, but Visual Studio Code extensions run as separate apps and can do whatever they want, such as deploying child processes, making system calls, and importing arbitrary Node.js packages. According to the research team, even in organizations that strictly manage permissions for each app, they often give high permissions to the development tool Visual Studio Code. This means that Visual Studio Code extensions also gain high permissions, making it easier for malicious extensions to spread their influence.
◆ Problems with marketplaces
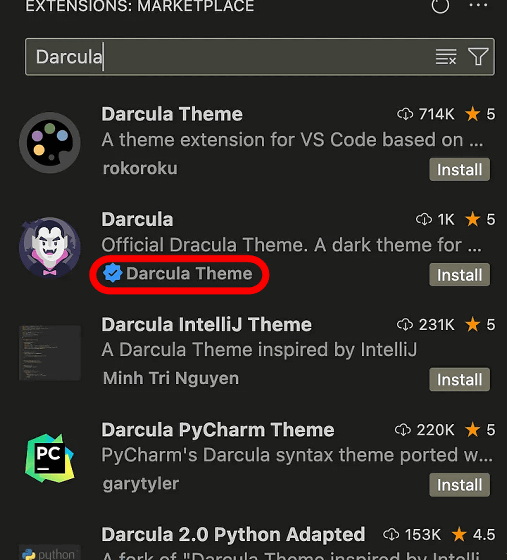
There are 45,000 publishers registered in the Visual Studio Code marketplace, of which 1,800 are verified publishers. Verified publishers are given a verified badge, which makes them seem trustworthy at first glance. However, the only thing required to become a verified publisher is to 'register a DNS-verified domain to your account.' Therefore, anyone can become a verified publisher as long as they have a domain.
The extension name and description written on the extension distribution page are contained in 'package.json', and package.json also contains 'the URL of the GitHub repository to be posted on the extension distribution page'. Since the contents of package.json are not checked, it is possible to include false information. For this reason, it is possible to increase the apparent credibility of a malicious extension by posting a completely unrelated GitHub repository on the distribution page of the extension. In this test, we were able to link to the real repository from the distribution page of the fake extension. In other words, the idea that 'Visual Studio Code extensions are safe because you can check the code in the GitHub repository' is a big mistake.
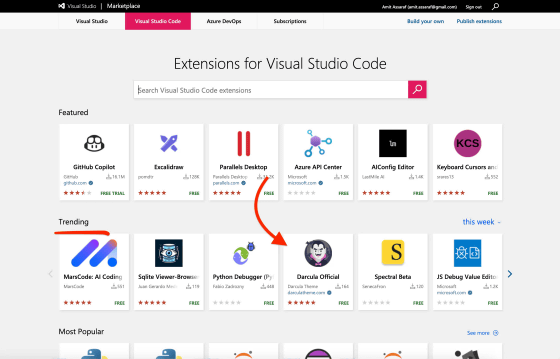
In addition, the fake extension developed by the research team was posted in the 'Trends' column on the top page of the marketplace within one day of its release. Although the trend extraction algorithm is unknown, the research team confirmed that it is possible to inflate the number of installations by looping the execution of a 'Docker container that installs extensions'. For this reason, the research team points out that it is possible to artificially make malicious extensions appear in trends.
◆ Forum is currently open
A forum related to this article has been set up on the official GIGAZINE Discord server . Anyone can post freely, so please feel free to comment! If you do not have a Discord account, please refer to the account creation procedure article to create an account!
• Discord | 'How do you determine whether an editor or browser extension is safe?' | GIGAZINE
https://discord.com/channels/1037961069903216680/1250010882705063948
Related Posts: