The Microsoft account of an insurance company affiliated with the Toyota Group was leaked, and about 25GB of email and customer information could be viewed.

It has been reported that the login information for the Microsoft account of Toyota Tsusho Insurance Broker India (TTIBI), a subsidiary of Toyota Tsusho Insurance Management, was leaked, and emails sent from that account could be viewed.
Hacking into a Toyota/Eicher Motors insurance company by exploiting their premium calculator website
Security researcher Eaton Zveare reported this issue. According to him, Microsoft account credentials were leaked through the Eisher Motors insurance premium calculation website located on the TTIBI subdomain.
When Zveare accessed his account with this information, he was able to see every email TTIBI had ever sent to customers, including customer information, insurance policy PDFs, password reset links, one-time passwords, and more. It seems that there were 657,000 emails (approximately 25 GB) including .

TTIBI is an insurance broker with jurisdiction over India, and Aisher Motors is a company known as one of India's leading automobile manufacturers. Since TTIBI has a dedicated subdomain for Eisher Motors, it is thought that the two companies have some kind of partnership. Mr. Zveare discovered the TTIBI account while researching the Eisher Motors app.
When Mr. Zveare was analyzing Eisher Motors' app, he discovered that a link to an insurance premium calculation website was hidden in the code.
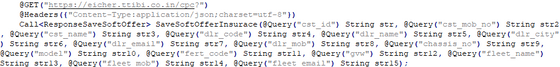
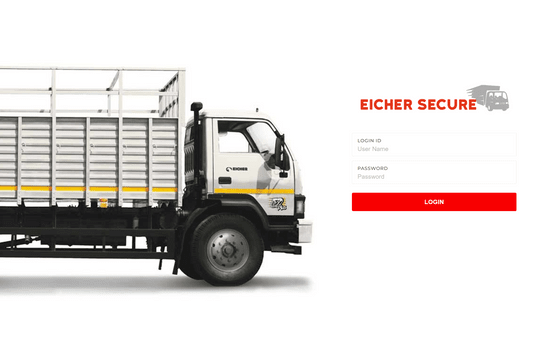
This link can be accessed below.
Eicher Secure
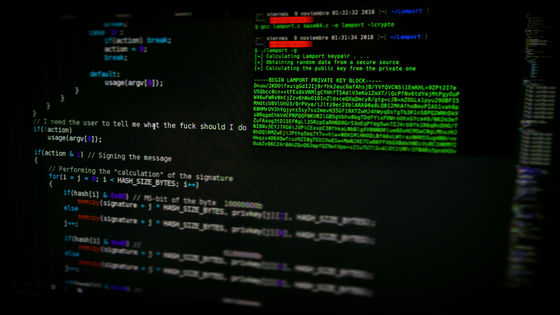
When Zveare followed the link above and checked the source code, he found that it mentioned a client-side email sending API. Here, Mr. Zveare thought, ``If this works, you can send an email with any subject or body to anyone, and it will be sent from the real Eisher Motors email address.''
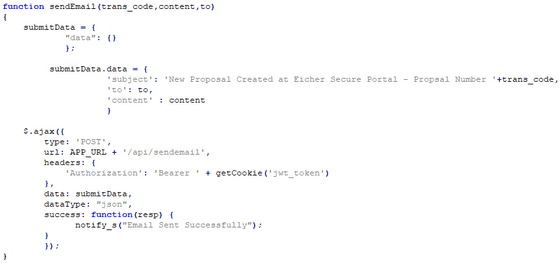
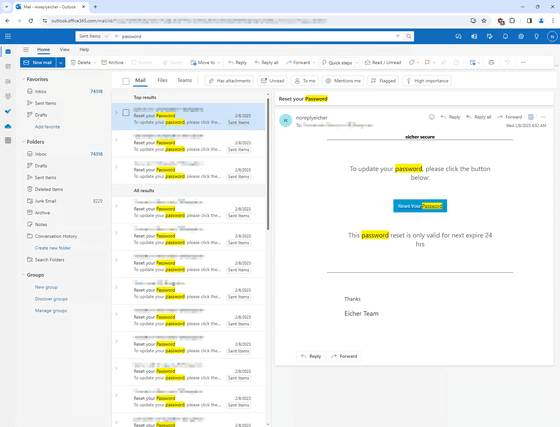
However, looking at Bearer authentication, it turns out that ``it is clear that you need to log in in some way to use this API.'' Mr. Zveare was intrigued and decided to try tweaking the API request to see what would happen. Mr. Zveare thought that he would receive a response of '401 - Unauthorized,' but in fact, not only was he able to send the email normally, but he also received a server error that revealed the email sending log. This log apparently contained the encoded password for TTIBI's noreply email account.
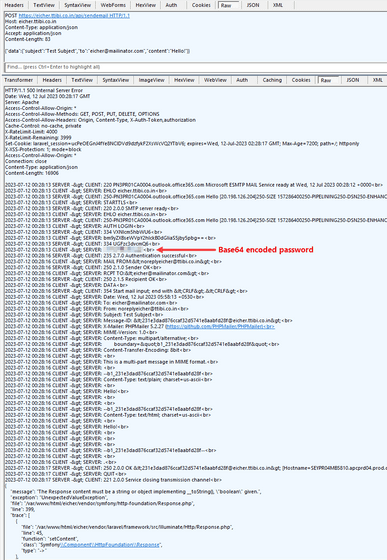
Mr. Zveare used the obtained credentials to access TTIBI's Microsoft account. At this time, it was also discovered that two-factor authentication was not enabled.
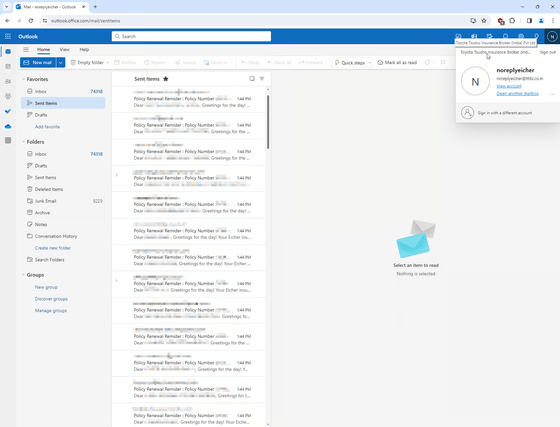
Insurance policy sent to customer
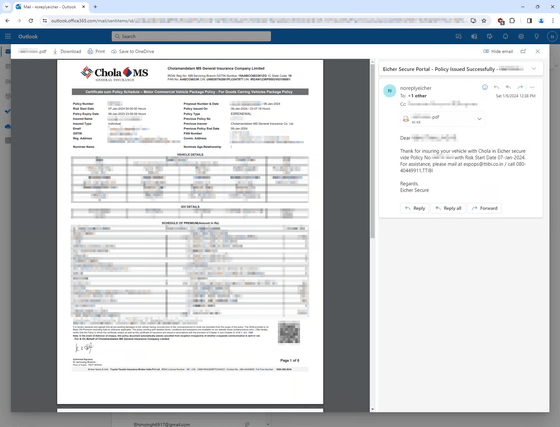
One-time password and password reset link
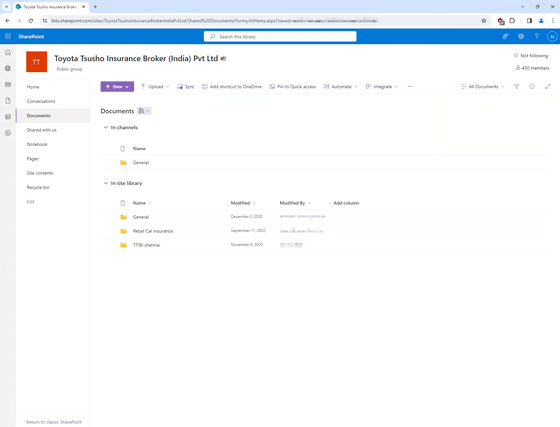
Zveare also reported that they were able to access resources on Microsoft's cloud, including corporate directories, SharePoint, and Teams.
Zveare reported the issue to CERT-In , the Indian government's cybersecurity incident response team. Although the information was conveyed to TTIBI through CERT-In, the response was delayed, and the vulnerability of the API was finally fixed more than two months after the report. However, because the password for the Microsoft account has not been changed, it seems that you will still be able to log into your account as of January 17, 2024. Zveare notes that he did not receive a response from TTIBI.
Related Posts:
in Security, Posted by log1p_kr