Law enforcement agencies in Japan, the US, and the EU seize the RagnarLocker dark web portal that launched an unauthorized access attack on Capcom

RagnarLocker is a ransomware group that is famous for launching
RagnarLocker ransomware dark web site seized in international sting | TechCrunch
https://techcrunch.com/2023/10/19/ragnarlocker-ransomware-dark-web-portal-seized-in-international-sting/
Ragnar Locker ransomware's dark web extortion sites seized by police
https://www.bleepingcomputer.com/news/security/ragnar-locker-ransomwares-dark-web-extortion-sites-seized-by-police/
RagnarLocker ransoms its last victim as cybercops seize site • The Register
https://www.theregister.com/2023/10/19/europol_knocks_ragnarlocker_offline/
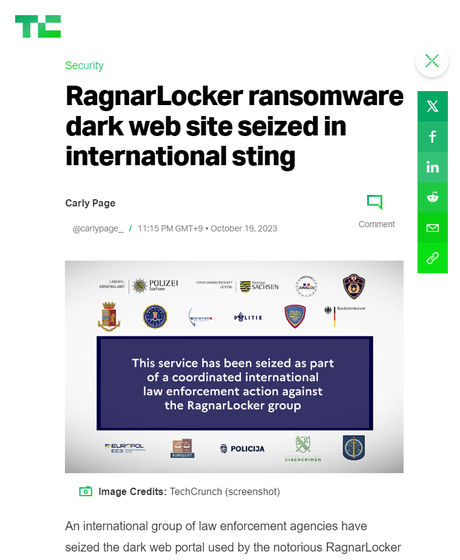
When you visit RagnarLocker's website on the dark web, you will see a message that says, 'This service has been seized as part of an international law enforcement action against RagnarLocker.' According to the notice, the German State Police of Saxony , the Staatsanwaltschaft Leipzig (Germany's public prosecutor's office), the Japanese National Police Agency , the Federal Bureau of Investigation (FBI) of the United States, and the Polizia Postale e delle Comunicazioni , the cybercrime countermeasures unit of the Italian State Police, are involved. It is understood that multiple law enforcement agencies are involved in the seizure, including Germany's Federal Criminal Agency , Europol, and the European Organization for Justice .

The full details of the operation have not been disclosed, and it is unclear whether other infrastructure used by RagnarLocker has been seized, whether any arrests have been made, or whether the stolen funds have been recovered.
When TechCrunch contacted the European Criminal Police Organization, spokesperson Claire Georges said it was 'involved in ongoing operations against this ransomware group,' but did not provide further details on the operation. It seems that he did not receive any explanation. In addition, the European Criminal Police Organization explains that it plans to make an announcement regarding the seizure on ``Friday when all actions are complete''. TechCrunch also reported that a similar response was received from the Italian state police, saying that ``details of the operation will be announced on Friday.''
TechCrunch has also contacted law enforcement agencies in Spain, Latvia, Germany, and the Netherlands, as well as the FBI, but these agencies did not seem to be able to comment.

RagnarLocker is a criminal group that develops and operates ransomware, and some security experts have linked it to Russia. RagnarLocker has been observed conducting attacks since around 2020, primarily targeting critical infrastructure organizations.
In 2022, the FBI warned that it had identified at least 52 companies in 10 major infrastructure sectors, including manufacturing, energy, and government, that were victims of RagnarLocker ransomware attacks. At this time, the FBI released the Bitcoin address used by RagnarLocker to collect the ransom and the contact email address.
RagnarLocker Ransomware Indicators of Compromise - FBI FLASH
(PDF file) https://www.ic3.gov/Media/News/2022/220307.pdf

According to ransomware tracker Ransomwatch, RagnarLocker has been under law enforcement surveillance for some time, but appears to have started attacking new targets in September 2023. In addition, RagnarLocker claimed to have stolen more than 1TB of data from Mayanei Haishua Hospital in Israel in September 2023.
Related Posts: