Exploit ``BLASTPASS'', which allows arbitrary code to be executed simply by receiving a malicious file on the iPhone, has been discovered, and Apple has distributed a software update as it is also used to distribute notorious spyware.

BLASTPASS: NSO Group iPhone Zero-Click, Zero-Day Exploit Captured in the Wild - The Citizen Lab
https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/

During the fifth week of August 2023, The Citizen Lab was analyzing the devices of individuals employed by civil society organizations based overseas and discovered an iPhone being exploited to distribute NSO Group's Pegasus. discovered a zero-click vulnerability.
The exploit chain that exploits this vulnerability is named 'BLASTPASS.' BLASTPASS can compromise a target iPhone ``without user intervention'' and may be affected even if the latest version of iOS 16.6 is installed at the time of writing.
The Citizen Lab has identified a vulnerability used in BLASTPASS and has disclosed its findings to Apple. Apple has identified two vulnerabilities related to BLASTPASS as CVE-2023-41064 and CVE-2023-41061 .
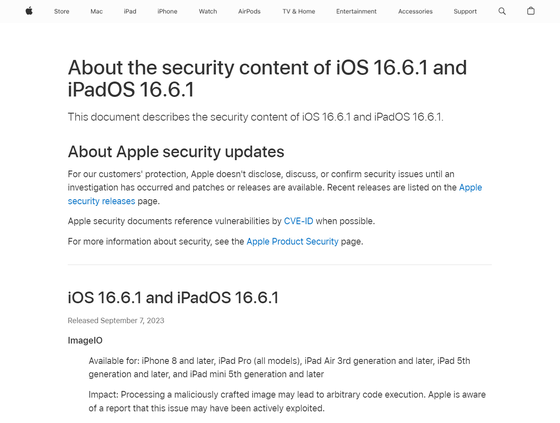
According to Apple, the vulnerability 'CVE-2023-41064' was identified based on information provided by The Citizen Lab. This vulnerability affects iPhone 8 and later models, iPad Pro (all models), 3rd generation iPad Air and later models, 5th generation iPad and later models, and 5th generation iPad mini and later models. Specifically, ``Processing a maliciously crafted image may lead to arbitrary code execution,'' and Apple has stated that this vulnerability may have been actively exploited. is.
Another vulnerability, CVE-2023-41061, was identified by Apple, and devices that may be affected include iPhone 8 and later models, iPad Pro (all models), and 3rd generation iPad Air and later models. , 5th generation iPad or later models, 5th generation iPad mini or later models. The specific impact is that ``arbitrary code may be executed by a maliciously created attachment,'' and there is a possibility that this was also actively exploited.
Although the details of BLASTPASS were not disclosed at the time of article creation, The Citizen Lab explained that ``we plan to publish a detailed explanation of BLASTPASS in the future.''

In addition, Apple has released iOS 16.6.1 as a software update to fix the vulnerability used in BLASTPASS. If you want to immediately update software on your iPhone and iPad, open the Settings app, tap 'General' → 'Software Update' → 'Download and Install' and enter your passcode. The Citizen Lab also writes, ``We recommend updating your iPhone immediately.''
About the security content of iOS 16.6.1 and iPadOS 16.6.1 - Apple Support
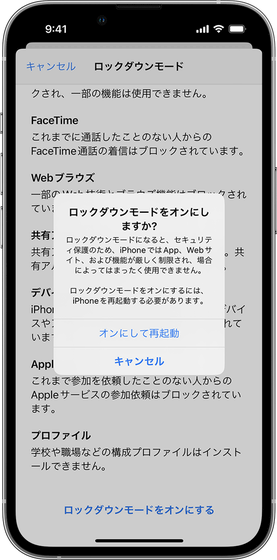
If you are unable to perform an iOS software update, The Citizen Lab recommends enabling Lockdown Mode on your iPhone. The Citizen Lab points out that enabling lockdown mode can block attacks, and Apple's security engineering and architecture team also confirmed this.
Related Posts:
in Software, Smartphone, Security, Posted by logu_ii