Microsoft launches new rules to name malicious threat actors such as Russia, North Korea, China, etc. after weather phenomena such as `` tsunami, typhoon, blizzard ''
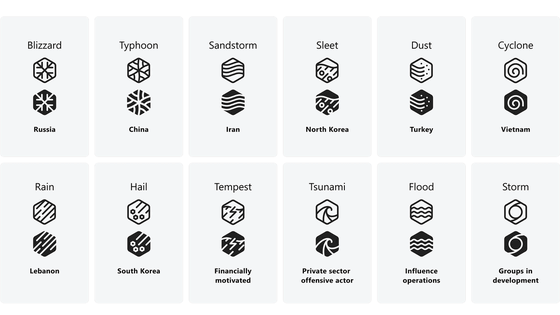
Naming rules for various threat actors named after weather phenomena, such as “XX blizzard” for Russian threat actors, “XX typhoon” for Chinese threat actors, and “XX flood” for influence operations. Microsoft has announced that it will apply.
Microsoft shifts to a new threat actor naming taxonomy - Microsoft Security Blog
How Microsoft names threat actors | Microsoft Learn
According to Microsoft, as threats grow in complexity, scale and number, they need to think not just about 'how Microsoft talks about threats,' but 'how to help users understand threats quickly and clearly.' He said. A new taxonomy of threat actors that has emerged is a nomenclature based on weather phenomena.
Microsoft categorizes threat actors into five main groups.
The first is the “national actor”. A cyber operator acting on behalf of or at the direction of a nation or a program associated with a nation, whether for espionage, financial gain, or retaliation. Most national actors continue to focus operations and attacks on government agencies, international intergovernmental organizations, non-governmental organizations, and think tanks, as an extension of past espionage and surveillance activities.
The second is 'actors with financial motives.' A cyber campaign or group led by a criminal organization or person motivated by financial gain that has no credible association with any known nation or entity. Includes groups using ransomware, business email attacks, phishing, and extortion.
The third is “private sector attackers”. A cyber activity led by a commercial actor that produces and sells cyber weapons to customers. These cyberweapons have been observed being used against dissidents, human rights activists, journalists, civil society advocates and even civilians, threatening global human rights efforts.
The fourth is 'influence manipulation attack'. An information campaign, online or offline, aimed at changing the perceptions, behaviors, and decision-making of the target population towards the interests and objectives of a nation or group.
The fifth is a “growing group”. This is a temporary state in which a threat is confirmed but set until a high degree of confidence is reached as to the origin or identity of the attacker behind the activity. If it meets the criteria, it will be converted to a named actor or merged with an existing name.
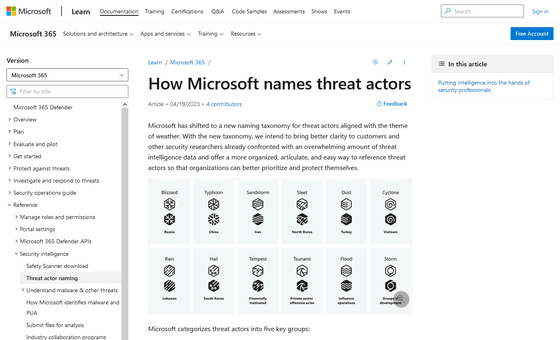
Specifically, the naming convention is as follows.
| Threat actor classification | threat actor | category name |
|---|---|---|
| national actor | China | Typhoon |
| Iran | Sandstorm | |
| Lebanon | Rain | |
| north korea | Sleet | |
| Russia | Blizzard | |
| Korea | Hail | |
| Türkiye | Dust | |
| Vietnam | Cyclone | |
| financially motivated actors | Tempest | |
| Private Sector Attack Actor | Tsunami | |
| influence attack | Flood | |
| growing group | Storm | |
For example, Russian threat actors are named 'Midnight Blizzard,' 'Forest Blizzard,' and 'Aqua Blizzard,' while Iranian threat actors are named 'Mint Sandstorm,' 'Gray Sandstorm,' and 'Hazel Sandstorm.' It will be.
Newly discovered actors are initially assigned a four-digit number, such as 'Storm-0257' or 'Storm-0539', and when reliable information about the origin or identity of the actor is obtained, the named actor is Converted.
In addition, when Chief Security Advisor Sarah Armstrong-Smith posted on LinkedIn about this new naming convention, other users said, `` It's useless work and will cause more confusion. '' `` Microsoft is simple. It turns what makes sense in , into something that's meaningless, confusing, and totally inconsistent with the community .
Sarah Armstrong-Smith on LinkedIn: Microsoft shifts to a new threat actor naming taxonomy - Microsoft… | 36 Comments
https://www.linkedin.com/feed/update/urn:li:share:7054119643635974145
Related Posts:
in Security, Posted by logc_nt