Vulnerability found that allows anyone to modify Bing search results to access users' Microsoft 365 data
A dangerous vulnerability has been discovered in Microsoft's search engine, Bing, that can change search results and access personal information of other Bing users from Teams, Outlook, Microsoft 365, and more. The vulnerability has already been fixed, but it has been pointed out that the contents of emails and documents may be exposed.
BingBang: AAD misconfiguration led to Bing.com results manipulation and account takeover | Wiz Blog
https://www.wiz.io/blog/azure-active-directory-bing-misconfiguration
Guidance on Potential Misconfiguration of Authorization of Multi-Tenant Applications that use Azure AD | MSRC Blog | Microsoft Security Response Center
https://msrc.microsoft.com/blog/2023/03/guidance-on-potential-misconfiguration-of-authorization-of-multi-tenant-applications-that-use-azure-ad/
Microsoft exploit could control Bing search results and Office 365 data - The Verge
https://www.theverge.com/2023/3/30/23661426/microsoft-azure-bing-office365-security-exploit-search-results
Microsoft's cloud computing platform, Azure, was misconfigured, allowing attackers to compromise Bing and allow any Azure user to access applications without authentication, according to security firm Wiz Research. About.
Microsoft has introduced its own single sign-on (SSO) service to its Azure system called Azure Active Directory (Azure AD) . Azure AD offers different types of account access: single-tenant , multi-tenant , individual accounts, or a combination of the latter two, but single-tenant applications require only users from the same tenant to issue OAuth tokens for the app. On the other hand, for multi-tenant applications, any Azure tenant can issue OAuth tokens. Therefore, app developers should inspect the token in their code to see which users are allowed to log in.
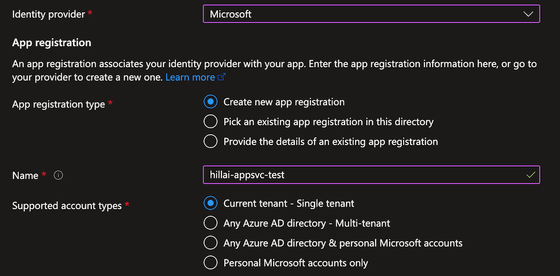
With Azure App Services and Azure Functions, users can add authentication functionality with the click of a button. While seemingly a smooth process for the application owner, the service only ensures token validity and is responsible for the act of verifying the user's identity via OAuth claims and provisioning access accordingly. It is not made clear that it belongs to the application owner.
This leads to the problem of frequent mistakes in configuration and verification. Security firm Wiz Research has found that Microsoft itself has fallen into the trap of misconfiguration, exposing critical applications with vulnerabilities to anyone on the internet. It seems that it turned out.
One of them was the domain 'bingtrivia.azurewebsites.net'. Wiz Research researchers logged into the app using their Azure accounts and discovered a content management system that allowed them to control Bing's live search results. And when the researcher made changes to the system, he was able to display the movie he set in the recommended column of Bing's search results.
I hacked into a
@Bing CMS that allowed me to alter search results and take over millions of @Office365 accounts.
How did I do it? Well, it all started with a simple click in @Azure … ????
This is the story of #BingBang ????⬇️ pic.twitter.com/9pydWvHhJs — Hillai Ben-Sasson (@hillai) March 29, 2023
Wiz Research stresses that anyone who landed on the 'bingtrivia.azurewebsites.net' page could have manipulated Bing search results to launch misinformation and phishing campaigns.
Wiz Research also investigated Bing's Work section and found that similar vulnerabilities were used to access other users' Microsoft 365 data, exfiltrating Outlook emails, calendars, Teams messages, SharePoint documents, and OneDrive files. I also found that it was possible to Wiz Research has demonstrated that it has successfully used this vulnerability to read emails from other people's inboxes.
The same vulnerability has been found in over 1000 apps and websites on Microsoft's cloud, including Mag News, Contact Center, PoliCheck, Power Automate Blog, Cosmos, and more.
The vulnerability was patched days before Microsoft released Bing's AI-powered chat feature. Wiz Research subsequently flagged other affected applications on February 25, and Microsoft announced on March 20 that it had fixed all reported issues. Microsoft also said it made additional changes to reduce the risk of future misconfigurations.
Wiz Research says there's no evidence the vulnerability was being exploited prior to the patch, but since AzureAD's logs don't reveal all the details about previous activity, the issue has been around for years. It also claims that it may have been exploited before. Wiz Research recommends that organizations using Azure AD applications review their application logs for suspicious logins that indicate compromised security.
Related Posts:
in Software, Web Service, Security, Posted by log1p_kr