Reportedly succeeded in hacking Hyundai's car and running its own application

Mr. greenluigi1, who bought Hyundai Motor's IONIQ 5, hacked the self-driving software and made it run its own application. The situation is spelled on the blog.
How I Hacked my Car :: Programming With Style
According to Mr. greenluigi1, the automatic driving software installed in IONIQ 5 was able to use developer mode and was able to check a large amount of logs and debug information.
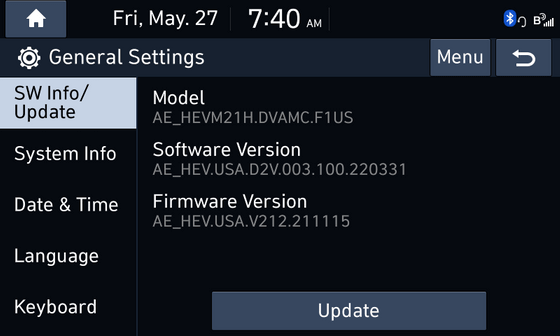
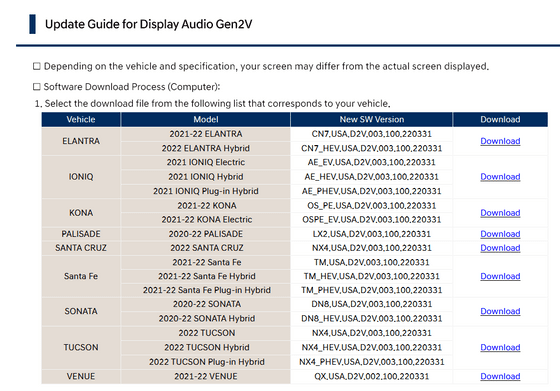
From that information, Mr. greenluigi1 learned that the software is running the second generation 'D-Audio2V' of Display Audio OS, which is often used in Hyundai Motor and Kia. or download firmware files. But important files were encrypted.
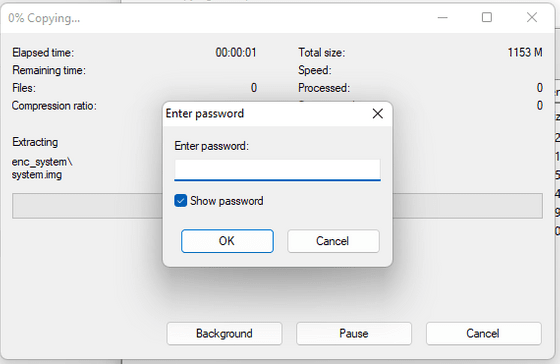
However, after repeating trial and error using a tool that cracks the encrypted ZIP file, he said that he succeeded in successfully extracting all the files. Having successfully accessed the file, greenluigi1 begins reverse engineering the app.
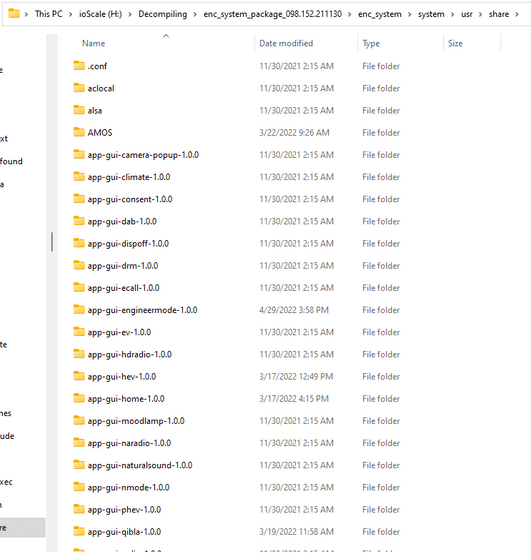
Believing that knowing all the security measures for firmware updates would allow full access to the system, greenluigi1 continued reverse-engineering the update process and apps, as well as searching for encryption keys related to update files.
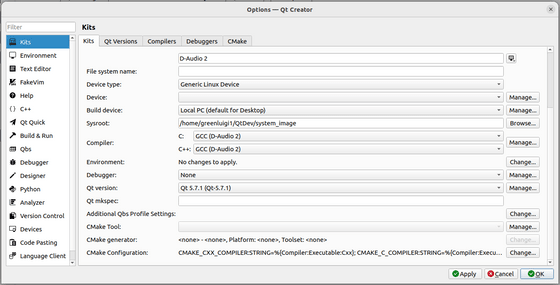
Meanwhile, he discovered that the script that creates the update file contains the encryption method and public key. A Google search for the public key reveals that a sample listed by the US National Institute of Standards and Technology (NIST) was used.
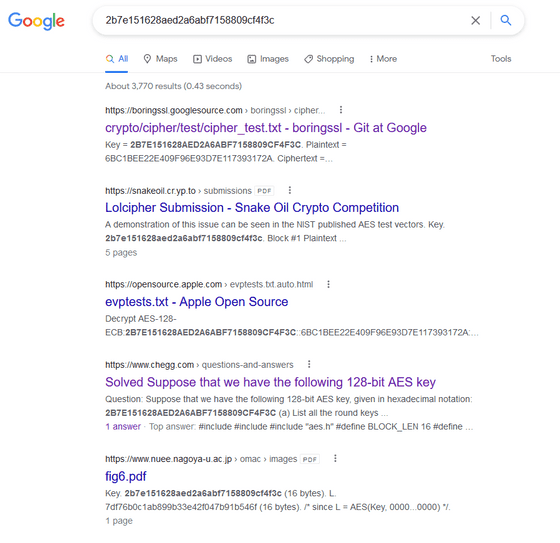
It waited for new firmware updates, learned through scripts exactly how D-Audio2V's encrypted firmware updates were done, and changed the system image with its own backdoor to allow full access.
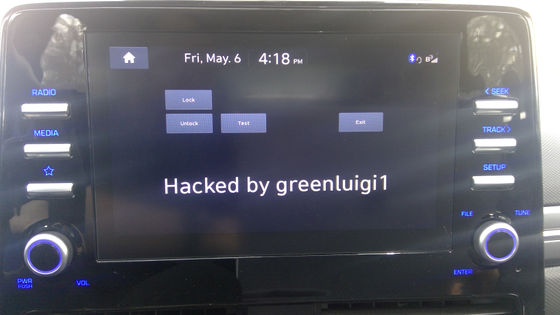
After various tasks, he succeeded in developing his own application, became able to monitor the state of the car from the application, unlock the door, and succeeded in ``completely controlling'' the software.
Related Posts:







