A ransomware attack group with 'pro-Russian policy' was attacked by a hacker near Ukraine and a year's worth of internal chat logs leaked

A pro-Ukrainian security researcher who was indignant at the pro-Russian policy of the Russian-based ransomware attack group 'Conti' obtained a year's worth of internal chat logs with the message 'Glory to Ukraine' I sent it to journalists and cyber security researchers.
Conti ransomware gang chats leaked by pro-Ukraine member --The Record by Recorded Future
Conti ransomware's internal chats leaked after siding with Russia
https://www.bleepingcomputer.com/news/security/conti-ransomwares-internal-chats-leaked-after-siding-with-russia/
Ukrainian Researcher Leaks Conti Ransomware Gang Data
https://www.databreachtoday.com/ukrainian-researcher-leaks-conti-ransomware-gang-data-a-18620
Pro-Russia Conti Ransomware Gang Targeted, Internal Chats Leaked
https://www.vice.com/en/article/z3ng84/pro-russia-conti-ransomware-messages-leaked
Conti, a ransomware attack group, had its internal chat logs stolen because the leader set a policy of 'formally supporting the Russian government' during the invasion of Ukraine. In addition to supporting cyberattacks against Ukraine, the announcement at the time declared that if an organization that launched a cyberattack against Russia emerged, it would counterattack its critical infrastructure.
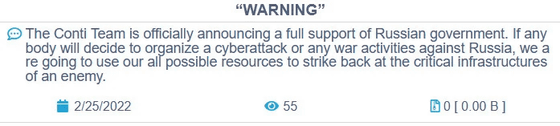
However, someone from the pro-Ukrainian school rewrote the above declaration as 'doing nothing with any government' and 'condemning the ongoing war' ...
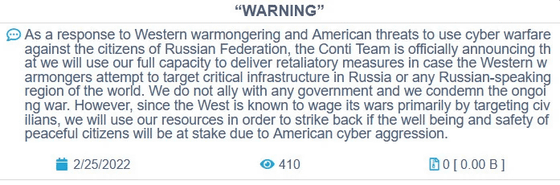
In addition, we sent all chat logs from January 29, 2021 to February 27, 2022 to journalists and cybersecurity researchers. According to vx-underground of the malware research group that this chat log arrived, the message 'Glory to Ukraine!' Was enclosed in the sent log. The leaked person is divided into 'Ukrainian department of Conti' and 'Ukrainian security researcher' by the media, but the truth is unknown. In any case, it is said to be 'someone who has access to Conti's internal information.'
Conti ransomware group previously put out a message siding with the Russian government.
https://t.co/BDzHQU5mgw pic.twitter.com/AL7BXnihza — Vx-underground (@vxunderground) February 27, 2022
Today a Conti member has begun leaking data with the message 'Fuck the Russian government, Glory to Ukraine!'
You can download the leaked Conti data here:
This chat log was extracted from the database of the XMPP server used by Conti, and is said to be 'genuine' by the security company. Since Conti went live in July 2020, the leaked chat logs aren't all, but cover 13 of the 20 months of activity.
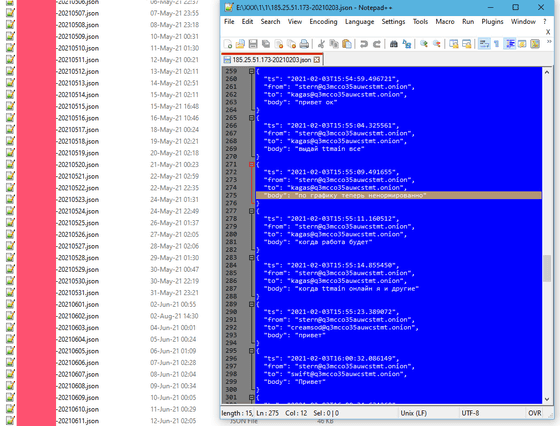
The content of the chat log is diverse, including discussions about interactions and operations with victims, topics related to specific exploits, interactions with the botnet ' TrickBot ' and the cybercriminal group 'Emotet', and Bitcoin wallets. Addresses, conversations seeking to break through the tools of security companies such as Carbon Black and Sophos are reported to be of great benefit to law enforcement agencies in each country.
Related Posts:
in Security, Posted by darkhorse_log







