It has been revealed that the Dark Angels received the largest ransomware ransom in history, more than 11 billion yen

Security company
ThreatLabz 2024_Ransomware Report
(PDF file) https://www.zscaler.com/resources/industry-reports/threatlabz-ransomware-report.pdf

Ransomware Hit $1 Billion in 2023
https://www.chainalysis.com/blog/ransomware-2024/
Dark Angels ransomware receives record-breaking $75 million ransom
https://www.bleepingcomputer.com/news/security/dark-angels-ransomware-receives-record-breaking-75-million-ransom/
Ransomware attacks on education continue to rise, report shows | EdScoop
https://edscoop.com/ransomware-cyberattacks-education-trend-2024/
$75 Million Ransom Paid to Dark Angels Ransomware Group
https://hackread.com/75-million-ransom-paid-dark-angels-ransomware-group/
Record-breaking $75M ransom paid to Dark Angels gang | Cybernews
https://cybernews.com/cybercrime/record-breaking-ransom-dark-angels/
Dark Angels Ransomware Group Scores Record-Breaking $75 Million Payday
https://blog.knowbe4.com/dark-angels-ransomware-group-scores-record-breaking-75-million-payday
$75M Ransomware Payment Exposed in New Zscaler Report
https://www.technewsworld.com/story/75-million-ransomware-payment-exposed-in-new-zscaler-report-179304.html
In recent years, the damage caused by ransomware attacks has been increasing. In Japan, Capcom was attacked by ransomware in November 2020, resulting in the leakage of personal information , a container terminal at Nagoya Port was forced to suspend operations due to a ransomware attack in July 2023, and Niconico's entire service was suspended due to a ransomware attack in June 2024.
A report summarizing the damage caused by such ransomware attacks was published on July 31, 2024 by ThreatLabz, the security research division of Zscaler. According to the report, it was revealed that one company had paid $75 million to the Dark Angels, the largest ransom ever paid by a single company. This is approximately double the amount of ransom payments known to the public.
Regarding Zscaler's published report, blockchain analysis company Chainalysis also posted, 'We can confirm that in early 2024, $75 million was paid, the largest ransom ever paid in a ransomware attack,' acknowledging that the $75 million ransom was paid.
We can confirm that early this year we saw the largest ransomware payment ever at $75M. The 'big game hunting' trend we discussed in our 2024 crime report – fewer attacks on larger targets with deeper pockets – is becoming more pronounced. https://t.co/Z0yvg3Zvp2 pic.twitter.com/4FsivojtA5
— Chainalysis (@chainalysis) July 30, 2024
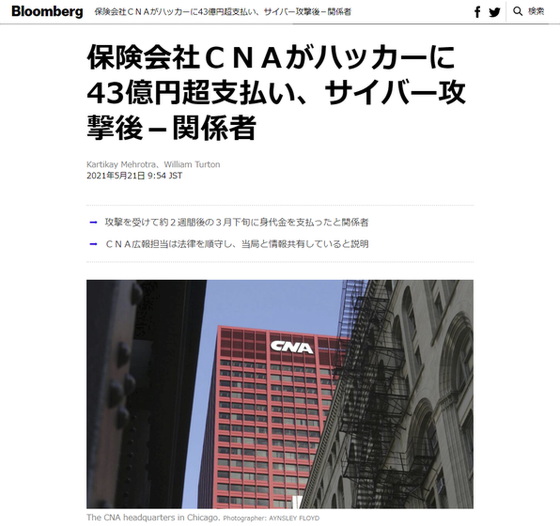
The largest ransom ever paid in a known ransomware attack was $40 million paid by insurance giant CNA to ransomware group Evil Corp.
Insurance company CNA pays over $43 million to hackers after cyberattack - sources - Bloomber
https://www.bloomberg.co.jp/news/articles/2021-05-21/QTFDTVT1UM0W01
Zscaler has not revealed the name of the company that paid the $75 million ransom, but the company is ranked in the Fortune 50 and was reportedly the victim of a ransomware attack in early 2024. Among Fortune 50 companies, pharmaceutical giant Cencora was attacked by a cyberattack in February 2024. Since the ransomware group Dark Angels has not claimed responsibility for this cyberattack, security media BleepingComputer pointed out that 'the company may have paid the ransom.'
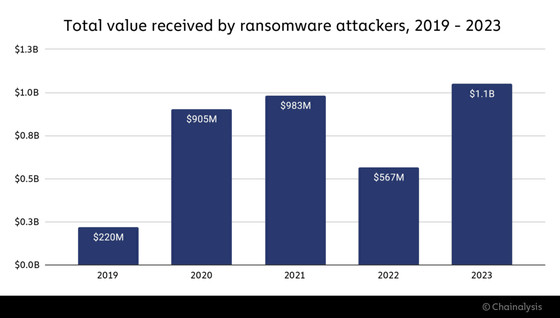
Chainalysis has published a graph summarizing the total amount of ransoms paid for ransomware attacks annually since 2019, when ransomware attacks began to become more active. According to this, the highest annual ransom payment was in 2023, at $1.1 billion (about 168 billion yen).
The ransomware group Dark Angels began operating in May 2022 and is an organization that launches ransomware attacks targeting companies around the world. Dark Angels operators infiltrate corporate networks, gain administrative privileges, and then steal data from servers. They then gain access to
The Dark Angels used a tool based on the source code of a ransomware called 'Babuk' to encrypt Windows and VMware ESXi , but gradually began to use the same Linux-based encryption tool used by the ransomware group 'Ragnar Locker.'
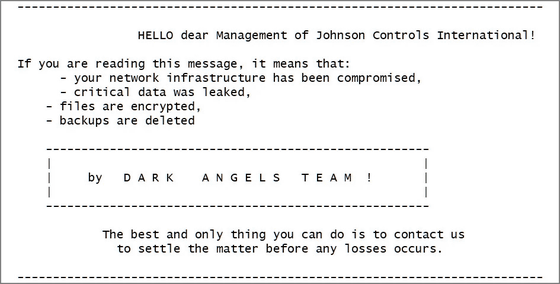
In September 2023, the Dark Angels used a Linux-based encryption tool to launch a ransomware attack on Johnson Controls , stealing 27 terabytes of corporate data and demanding a ransom of $51 million.
Below is the ransom notice issued by the Dark Angels to Johnson Controls demanding payment.
The Dark Angels also run a data leak website called 'Dunghill Leaks,' where they publish the data of companies that did not pay the ransom.
According to Zscaler, Dark Angels adopts a strategy of targeting large ransom payments from a single company, rather than collecting small ransom payments from multiple companies. Therefore, ThreatLabz researchers wrote that 'Dark Angels adopts a highly targeted approach, typically attacking one large company at a time,' and that 'this is in stark contrast to most ransomware groups, which target victims indiscriminately and outsource most of their attacks to associated networks of initial access brokers and penetration testing teams.'
Related Posts:
in Security, Posted by logu_ii