'The official Beijing Olympics app collects athletes' voice data,' researchers point out.

At the Beijing Winter Olympics to be held in February 2022, all participants will be required to install the dedicated health management app 'MY2022 ' in order to be vaccinated against the new coronavirus infection (COVID-19) and to understand their health status. It has been. However, a security researcher who reverse engineered MY2022 reports that 'My2022 collects various data including voice data and sends it to a server in China.'
GitHub --jonathandata1 / 222_beijing: Decompiled 2022 Beijing iOS & Android Apps
Mandatory Olympics iOS and Android apps are spying on athletes for China | AppleInsider
https://appleinsider.com/articles/22/01/28/mandatory-olympics-ios-and-android-apps-are-spying-on-athletes-for-china
Beijing spy games: watch out for the application of the Olympics! --The Switzerland Times
https://www.theswitzerlandtimes.com/beijing-spy-games-watch-out-for-the-application-of-the-olympics/
Athletes and attendees participating in the Beijing Winter Olympics are required to install the official app MY2022 on their smartphones 14 days before entering China. MY2022 is designed to act as a hub for providing information on local events, weather and things of interest, as well as the purpose of monitoring vaccination status and health to limit the spread of COVID-19. It is said that there is.
Citizen Lab, an interdisciplinary research institute at the University of Toronto that analyzed MY2022, reported that MY2022 has a security flaw that makes it easy to circumvent encryption that protects users' voices and transfer files. We also know that the Android version of MY2022 contained a 2422 word 'censorship word list' for Xinjiang Uygur Autonomous Region, Tibet, politics, crime, pornography, religion, and more. At the time of the survey, the censorship keyword list was not used.
The 2022 Beijing Olympics athlete app turns out to have a serious security flaw, and a keyword censorship list is also discovered-GIGAZINE
Meanwhile, American security researcher Jonathan Scott reports the results of reverse engineering and analysis of MY2022 on Twitter and GitHub. 'The decompiled iOS and Android apps for the 2022 Olympics are now available on GitHub, despite claiming'no data collection'on Apple's App Store,' Scott said. There is evidence of a data breach. This repository is directly related to the full report I release, 'tweeted with the tag #spyware.
Decompiled # Olympics2022 #iOS and #Android Apps available on Github Now.
— Jonathan Scott (@ jonathandata1) January 23, 2022
Evidence of Chinese data exfiltration although the Apple App store claims 'Data Not Collected'
This repo directly correlates with my full report I will be releasing. #Spyware https://t.co/hBAxyLMzBp
According to Scott, as of January 22, 2022, the App Store's MY2022 page says 'Data Not Collected,' but on January 24, it will collect contact information. It was changed to the notation.
One of the biggest deceptions is how the app is listed in the Apple App store ...
— Jonathan Scott (@ jonathandata1) January 27, 2022
Jan 22nd, 2022 --No Data was collected
Jan 24th, 2022 --Only Contact Info, but not really? Pic.twitter.com/aGq1yk7EcB
Scott, who analyzed MY2022, claims that 'I can assure you that the audio of all Olympic athletes has been collected, analyzed and stored on a server in China.' It is said that the technology of iFlytek , a state-owned voice recognition AI company in China, is used for this process, but iFlytek has been blacklisted by the U.S. government as being involved in the suppression of Muslims in China. I will .
After reverse engineering all of the # Beijing2022 #spyware app for @Apple #ios and @Google #Android
— Jonathan Scott (@ jonathandata1) January 26, 2022
I can definitively say all Olympian audio is being collected, analyzed and saved on Chinese servers using tech from USA blacklisted AI firm @ iflytek1999 https://t.co/9wX1sP8PZP pic.twitter.com/hdIfiKX37m
The privacy policy agreed by app users also states that voice information and information about apps installed on smartphones will be collected by iFlytek. However, this is not specified on the App Store page.
https://t.co/h9JnRJlWNs
— Jonathan Scott (@ jonathandata1) January 27, 2022
This is the privacy policy that app users are required to agree to. It vaguely states that 'voice information' is collected by iFlytek, and does not go into detail. Furthermore, the apple app store requires developers to disclose what is being collected pic. twitter.com/AcpLoabEFc
It is said that MY2022 does not operate in the background by exploiting vulnerabilities in smartphones, but maintains the foreground state in order to access the microphone.
it doesn't get rid of the dot, the application forces itself to the foreground to make sure it has the capability to listen. so for example on android
— Jonathan Scott (@ jonathandata1) January 27, 2022
<uses-permission android: name = 'android.permission.REORDER_TASKS' />
for iOS a monitor is triggered & brings the app up front pic.twitter.com/5zbdT9WTfi
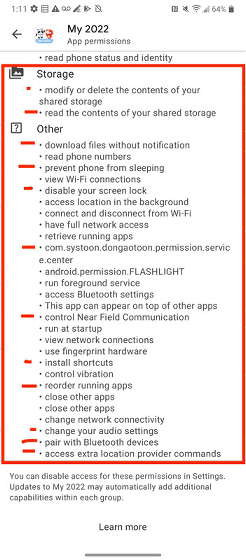
In addition, in the Android version of MY2022, in addition to permission to access calendars, cameras, contacts, microphones, storage, etc ...
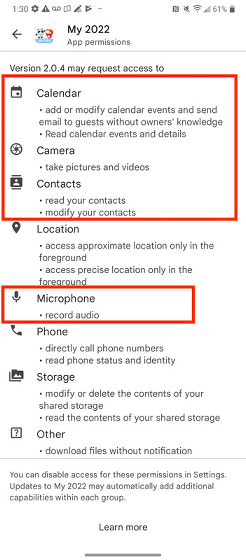
'Unfortunately Google has allowed the MY2022 app to create a permanent backdoor on your device,' said Max, who may ask for permission to download files and unlock the screen. '.
Due to concerns about China's espionage, the Netherlands has long urged players not to bring their smartphones and PCs to China, and the United States and Canada have also replaced their own smartphones with prepaid and disposable devices. Recommended to use.
Related Posts: