After gaining the trust of users, an application that takes the method of 'gradually delivering malware with updates' is discovered

It was discovered that the malware 'Banking Trojan' that steals user information from account management apps and SNS was installed in the apps distributed on Google Play. The app has already been downloaded more than 300,000 times in total.
Deceive the Heavens to Cross the sea — Threat Fabric
Google Play apps downloaded 300,000 times stole bank credentials | Ars Technica
https://arstechnica.com/information-technology/2021/11/google-play-apps-downloaded-300000-times-stole-bank-credentials/
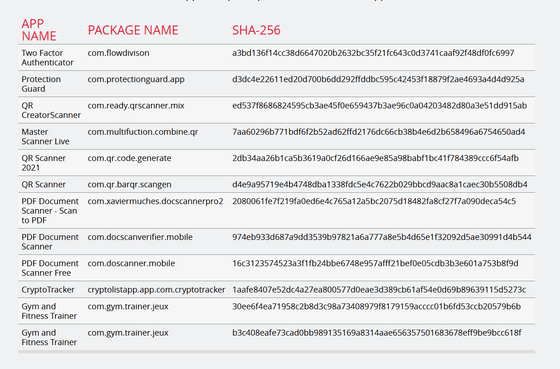
Threat Fabric , the security company that reported this issue, has published the names of 12 applicable apps such as 'Two Factor Authenticator' and 'Protection Guard', but they have already been removed from Google Play.
According to ThreatFabric, these apps are delivered under the guise of 'decent apps,' and when users install the app, they will be asked to update it, including additional features. In the process of this update, it is required to install the 'source unknown' application, and if the user approves, it will be infected with malware.
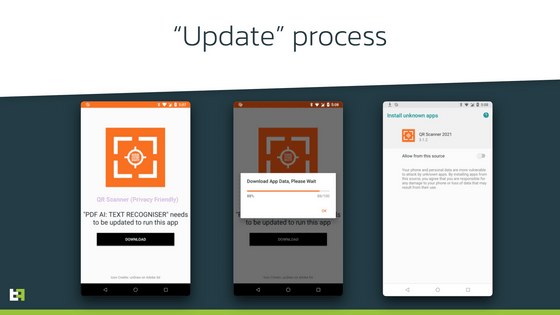
The app in question was delivered as a tool app such as a QR code reader or exercise. Many positive Sakura reviews have been posted for these apps to pretend to be decent apps, and the updates delivered as additional features are as announced, so users are not skeptical. He said he was doing it.
The four malware detected were 'Anatsa,' 'Alien,' 'Hydra,' and 'Ermac.' ThreatFabric says, 'It's worth noting that we are responding quickly to Google Play regulations. The difficulty of detecting malware from apps registered with a minimal footprint is also due to the low detection rate of detection apps. It's backed up. '

Related Posts: