More than 2000 extensions for Google Chrome point out that they are degrading security

It has been reported that many of the extensions distributed on the '
madweb21-paper16-pre_print_version.pdf
(PDF link) https://madweb.work/preprints/madweb21-paper16-pre_print_version.pdf

Thousands of Chrome extensions are tampering with security headers | The Record by Recorded Future
https://therecord.media/thousands-of-chrome-extensions-are-tampering-with-security-headers/
When accessing a website, the web browser receives security headers from the server, such as HTTP Strict Transport Security (HSTS) , which requires communication over HTTPS, and Content Security Policy (CSP), which mitigates external attacks. These security headers are used by many websites, but they can also be targeted by attackers. Therefore, the research team investigated the effects of Google Chrome extensions on four types of security headers, 'HSTS', 'CSP', 'X-Frame-Options ', and ' X-Content-Type-Options'. ..
Research has shown that out of 186,434 extensions distributed on the Chrome Web Store, 2,485 extensions make changes to at least one type of security header. In addition, 553 extensions revealed that they made changes to all four types of security headers.
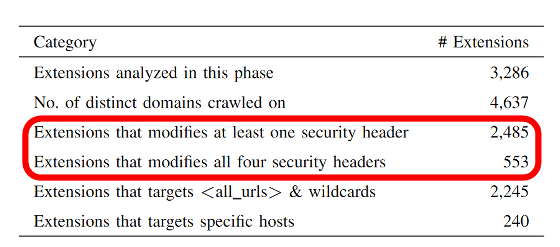
The breakdown of the security header that has been changed is like this. You can see that the most modified security header is the CSP, and the other security headers have also been modified from over 1000 extensions.
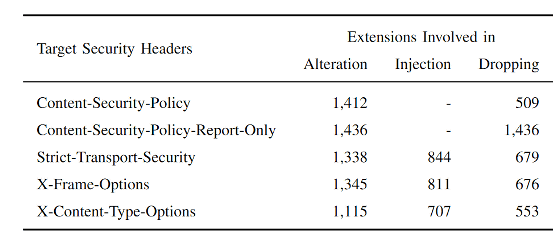
According to the research team, the security header changes made by most extensions were intended to improve the user experience and were not malicious. However, the research team disagrees with tampering with security headers, saying that 'modifications to security headers can put users at risk of attack.'
Related Posts: