Vulnerability 'NAME: WRECK' affecting millions of IoT and industrial devices

NAME: WRECK --Forescout
https://www.forescout.com/research-labs/namewreck/
NAME: WRECK vulnerabilities impact millions of smart and industrial devices | The Record by Recorded Future
https://therecord.media/namewreck-vulnerabilities-impact-millions-of-smart-and-industrial-devices/
How the NAME: WRECK Bugs Impact Consumers, Businesses | Threatpost
https://threatpost.com/namewreck-bugs-businesses/165385/
A vulnerability called 'NAME: WRECK' discovered in Project Memoria, Forescout's internal research program, is related to the TCP / IP stack. The TCP / IP stack is a collection of programs related to the TCP / IP communication protocol required when creating applications that communicate using LAN (protocol stack ), and the vendor connects the device to the Internet and other networks. A library that is added to the firmware to support features.
This library is very small and most often supports the most basic functionality of the device. However, by using 'NAME: WRECK', a malicious attacker can remotely attack the user via the TCP / IP stack.

'NAME: WRECK' is the fifth set of vulnerabilities that have been disclosed over the last three years that affect the TCP / IP stack. Vulnerabilities other than 'NAME: WRECK' were revealed in the investigation on various mechanisms of TCP / IP communication, but 'NAME: WRECK' is not TCP / IP communication, but the library used for them. Found while investigating how to handle DNS traffic.
More precisely, researchers have

Project Memoria's research into this message compression feature revealed a total of nine vulnerabilities affecting seven of the 15 TCP / IP stacks. The nine vulnerabilities are as follows.
・
・CVE-2016-20009
・CVE-2020-15795
・CVE-2020-27009
・CVE-2020-27736
・CVE-2020-27737
・CVE-2020-27738
・CVE-2021-25677
・ Unallocated
The following is a diagram summarizing the TCP / IP stack affected by the nine vulnerabilities discovered this time. The red part is the TCP / IP stack affected by the newly discovered 'NAME: WRECK', which corresponds to FreeBSD, IPnet, NetX, and Nucleus NET.
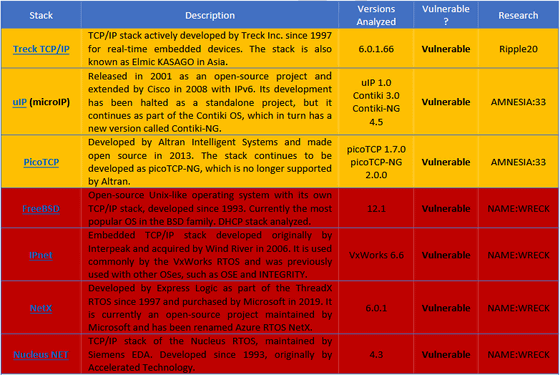
On the other hand, TCP / IP stacks such as FNET, cycloneTCP, uC / TCP-IP, FreeRTOS + TCP, Zephyr, and OpenThread have been shown to securely implement message compression functionality. And since the two stacks Nut / Net and lwIP do not support the message compression function, they are not affected by the vulnerability.
Forescout has reported issues to the developers of the four TCP / IP stacks affected by 'NAME: WRECK', but only three have released patches for FreeBSD, Nucleus NET, and NetX. IPNet is continuing to support 'NAME: WRECK'.
SECURITY VULNERABILITY RESPONSE INFORMATION --TCP / IP Network Stack (IPnet, Urgent / 11) | Wind River
https://www.windriver.com/security/announcements/tcp-ip-network-stack-ipnet-urgent11/
It seems reassuring that multiple TCP / IP stacks have released patches, but in reality 'the situation is far from perfect,' says security media The Record . The reason is that patching IoT and industrial devices requires manufacturers to release their own firmware updates that integrate the patches, which can take a long time.
Also, even if the manufacturer releases a firmware update that corresponds to the patch, the customer does not necessarily carry out the update. Many IoT and industrial devices that utilize the TCP / IP stack are deployed in remote locations and are difficult to update unless they support FOTA. However, according to The Record, 'there are very few devices that support FOTA.'
In addition, some device owners may not even be aware that servers, smart devices, and industrial devices are using the TCP / IP stack in the first place. So, 'Unfortunately, many devices can remain vulnerable to attacks using'NAME: WRECK',' The Record pointed out.
According to Forescout security researcher Daniel Dos Santos, some 'NAME: WRECK' patterns require the ability to tamper with the victim's DNS traffic, but 'become vulnerable systems.' There is also a vulnerability that enables remote attacks simply by continuing to send invalid DNS replies. '

According to Santos, most of the TCP / IP stack vulnerabilities discovered in this survey are due to misinterpretation of the vendor's DNS standard. So, The Record points out, 'You may have to ask yourself if the DNS standard itself is too complex.'
Related Posts: