Salesforce releases AWS account attack tool but removes it in haste

GitHub --salesforce / endgame: An AWS Pentesting tool that lets you use one-liner commands to backdoor an AWS account's resources with a rogue AWS account --or share the resources with the entire internet
https://web.archive.org/web/20210216153239/https://github.com/salesforce/endgame
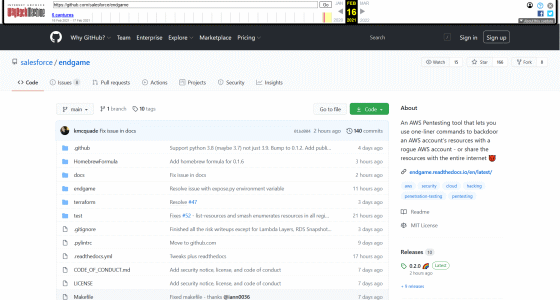
Endgame is a
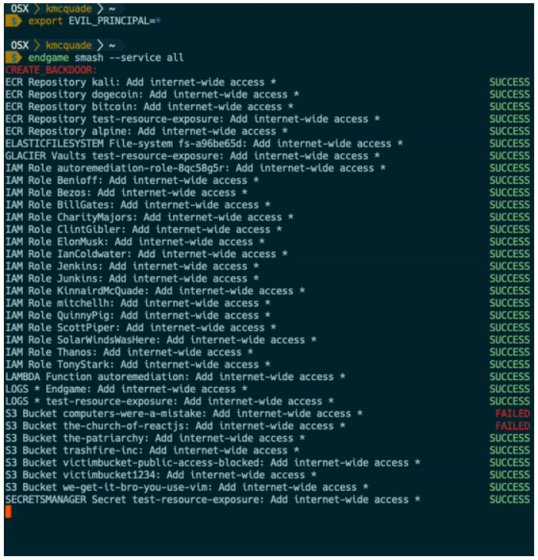
As a mechanism, it seems that it is abusing
Managing permissions for cloud services is so complex that human error can always occur, assigning extra permissions. AWS offers an ' AWS IAM Access Analyzer ' that can detect such vulnerabilities, but McQuade points out that the AWS IAM Access Analyzer is not fully functional. The table below shows that AWS IAM Access Analyzer only supports 7 of the resources that Endgame is attacking.
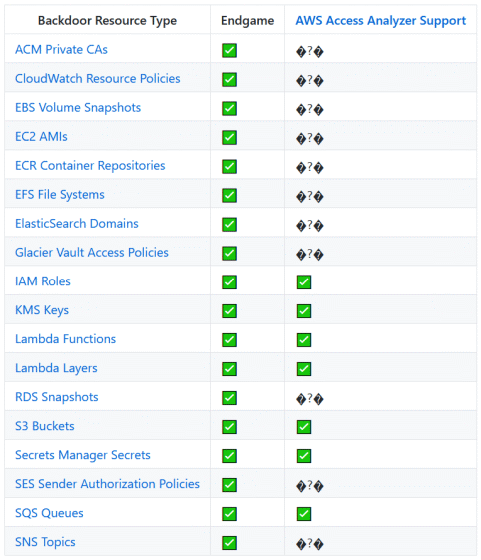
Endgame is not for hacking, it was developed to ask AWS to improve permission management in addition to raising the security awareness of AWS users and developers. McQuade lists 'improvements in AWS IAM Access Analyzer' and 'increase in the number of
In addition, Endgame was published in Salesforce's GitHub repository, but at the time of article creation, it can no longer be viewed from the outside.
Page not found · GitHub · GitHub
https://github.com/salesforce/endgame
Endgame was also published in the developer McQuade's own GitHub repository, but at the time of writing the article, it was inaccessible like the Salesforce repository, and it seems that some measures were taken. Under these circumstances, the repositories that copied Endgame were scattered, but they have been deleted.
Page not found · GitHub · GitHub
https://github.com/kmcquade/endgame
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log