How is the 'UUID' used as the only identifier in the world generated?

Due to the convenience of online competition systems and ranking systems, it may be necessary to create an 'identifier that is the only value in the world' without connecting to a server, and in such cases, '
Understanding How UUIDs Are Generated --Digital Bunker
https://digitalbunker.dev/2020/09/30/understanding-how-uuids-are-generated/
The UUID is designed to be unique and unique around the world, and its uniqueness is independent of factors such as the central server. If you use a UUID with these characteristics as the primary key of a database, you can freely combine it with another person's database or move data to another database. On the other hand, since anyone can create a UUID, it also has the disadvantage of not being able to track the UUID that currently exists in the world.
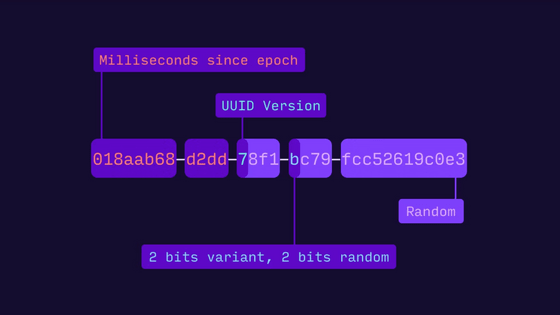
There are many ways to achieve unique, unique values around the world, but many modern UUID implementations are based on the IETF RFC 4122 , which defines five different generation methods. I am. The UUID defined here is a 128-bit bit string, and this bit string is generally displayed in hexadecimal notation in the format of 8-4-4-4-12.
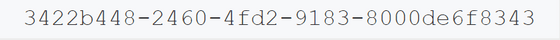
You can tell which format the UUID was generated by looking at the letters at the M and N positions in the figure below.
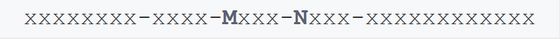
First, the UUID type 'variant' is determined by how many 1's are consecutive in the first few bits of N. Since RFC 4122 stipulates that the first bit is '1' and the second bit is '0', the UUID based on RFC 4122 has N positions of '8', '9', 'A', and 'B'. To become one of.
| 1st bit | 2nd bit | 3rd bit | Variant type |
|---|---|---|---|
0 | Reservation for backward compatibility with NCS | ||
| 1 | 0 | Standardized by RFC 4122 | |
| 1 | 1 | 0 | Reservation for backward compatibility with Microsoft GUID |
| 1 | 1 | 1 | Reservation for future standards |
The version is shown at the position of M, and you can see which of the five generation methods is used in this first 4 bits.
| 1st bit | 2nd bit | 3rd bit | 4th bit | version | detail |
|---|---|---|---|---|---|
| 0 | 0 | 0 | 1 | 1 | Time-based UUID |
| 0 | 0 | 1 | 0 | 2 | UUID combined with POSIX user ID |
| 0 | 0 | 1 | 1 | 3 | UUID based on MD5 of unique string |
| 0 | 1 | 0 | 0 | Four | UUID based on randomness |
| 0 | 1 | 0 | 1 | Five | UUID based on SHA-1 of unique string |
More commonly used today is the version 4 implementation, which randomly determines all 122 bits of the 128 bits, excluding the 6 bits that represent version variant information. If you decide completely randomly, duplication is likely to occur somewhere, but according to Mr. Shada, the risk of duplication is extremely low in reality.
For example, if you create 1 billion UUIDs per second for 100 years, there is about a 50% chance that duplicate UUIDs will be generated, and if you generate 10 trillion UUIDs, duplicates can be generated. The sex is 0.00000006%. However, these calculations are based on the case of using 'true random numbers', and there is a high possibility that they will be duplicated depending on the pseudo-random numbers used to generate the UUID. It seems necessary to pay attention to the quality of the random numbers used in order to protect the UUID's 'unique value that is unique in the world' feature.
Related Posts: