Tesla's car had a vulnerability that could be remotely controlled all at once via the net

Elon Musk, who attended a meeting of the Governor's Association in Rhode Island in July 2017, said, ``In principle, if someone could hack all of the autonomous Tesla, You can order all the cars on the island.” I jokingly commented. However, according to technical news media Electrek, a vulnerability that allows remote control of Tesla's cars all at once was discovered a few months ago from comments by CEO Musk.
The Big Tesla Hack: A hacker gained control over the entire fleet, but fortunately he's a good guy-Electrek
Jasson Hughes, who owns Tesla's car, unlocks features that have not been released by hacking, sells parts that modify Tesla's electrical components, and is known to the Tesla owner community It was there. In addition, Mr. Hughes was also active as a white hacker who found vulnerabilities in automobile firmware and system including Tesla and reported it to the manufacturer.
It turns out that Tesla has remotely downgraded the firmware of ``Model S P85D''-GIGAZINE

When Tesla started a service to deliver the location and status of the supercharger for charging to Navi, Mr. Hughes analyzed the system and found that the server side providing the service can be accessed through the car through the car It seems that a vulnerability has been found that can acquire the data of the charger station.

Hughes reported the vulnerability to Tesla, and Tesla paid Hughes $5,000 (about 520,000 yen) based on the bug reporting program. As a result of this incident, Mr. Hughes began to actively search for Tesla's vulnerability.
In 2017, Hughes discovered a vulnerability in Tesla's 'fleet learning' system. Fleet learning is to receive data from all Tesla vehicles in real time and feed it back to Tesla's onboard AI through machine learning. Mr. Hughes succeeded in accessing Tesla's server 'Mothership' used in this fleet learning communication using the car's VPN connection.
Hughes realized that it would be possible to have complete control of a car from Mothership, only by the vehicle identification number. Also, it was possible to send commands to all vehicles by accessing through a database in Tesla.
Actually, when the Electrek editor gave Hughes the vehicle identification number of his car at that time, Hughes immediately pulled out data such as vehicle position information and battery level.
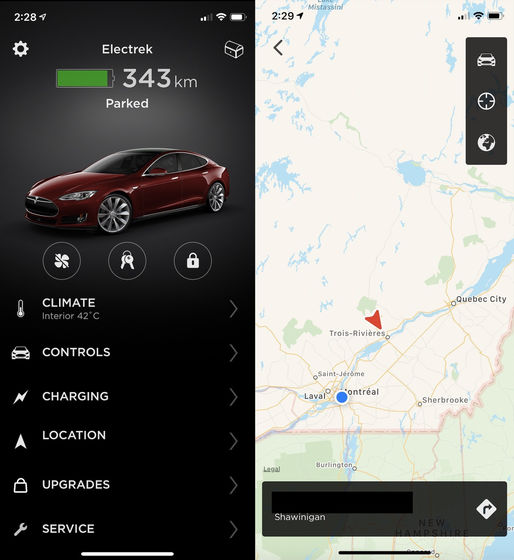
Hughes also reported that when he reported the vulnerability to Aaron Siguel, who was then head of software security at Tesla, he moved his California-based Sigel from his home in North Carolina about 3,800 km away. I tried to operate it.
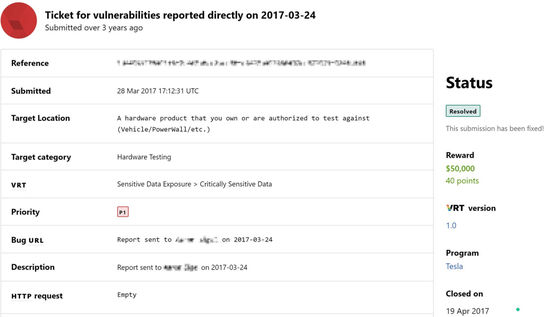
Tesla modified the system based on the information provided by Mr. Hughes and immediately protected the fleet learning network. And Mr. Hughes seems to have been specially paid $ 50,000 (about 5.2 million yen), which is 10 times the bug reward limit.
In January 2020, Tesla launched a hacking project ' Pwn2Own ' for its own car, with a prize money of 1 million dollars (about 100 million yen). 'We have continued to increase our investment in partnerships with security researchers since we launched our first bug bounty program in 2014,' said David Lau, Vice President of Vehicle Software at Tesla. 'Pwn2Own's excellent research will continue to improve our approach to designing products and intrinsically safe systems.'
Related Posts:







