It turns out that there is a vulnerability `` Kr00k '' that can be intercepted by more than 1 billion Wi-Fi terminals such as iPhone and Galaxy

Wi-Fi, which is widely used in smartphones and notebook PCs, achieves secure communications by encrypting communications using one of the security protocols, such as
kr00k | ESET
https://www.eset.com/int/kr00k/
New Kr00k vulnerability lets attackers decrypt WiFi packets | ZDNet
https://www.zdnet.com/article/new-kr00k-vulnerability-lets-attackers-decrypt-wifi-packets/
The vulnerability, named ' Kr00k ', is due to a bug in the Wi-Fi chips from
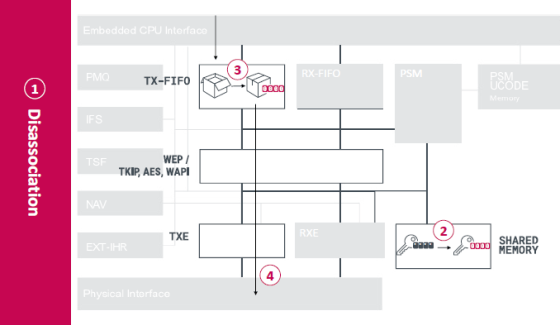
Normally, Wi-Fi terminals encrypt communication using a key encryption generated by an encryption algorithm such as AES from a Wi-Fi password. However, Wi-Fi devices equipped with Broadcom and Cypress chips reset the key value to zero during the ` ` Disassociation '' process, which disconnects itself when Wi-Fi communication strength is weak. You. In addition, ESET states that the vulnerability is that data frames encrypted while the key value is zero remain in the buffer memory and are transmitted as is.
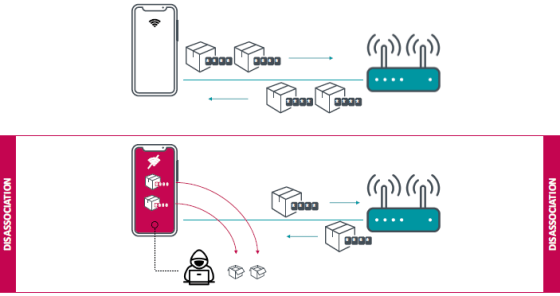
In addition, Wi-Fi disconnection, which triggers this vulnerability, can be triggered using management data frames, which do not require encryption. As long as the device's Wi-Fi is within physical reach, an attacker can trigger a disconnect at their own time, capture the frame, decrypt it, and see the contents of the frame.
The following devices were tested by ESET and found to be vulnerable. There are a number of devices with Broadcom and Cypress Wi-Fi chips in addition to the tested devices.
• Amazon Echo 2nd gen
• Amazon Kindle 8th gen
• Apple iPad mini 2
• Apple iPhone 6, 6S, 8, XR
• Apple MacBook Air Retina 13-inch 2018
• Google Nexus 5
• Google Nexus 6
• Google Nexus 6S
• Raspberry Pi 3
• Samsung Galaxy S4 GT-I9505
• Samsung Galaxy S8
• Xiaomi Redmi 3S
• Asus RT-N12
• Huawei B612S-25d
• Huawei EchoLife HG8245H
• Huawei E5577Cs-321
The newly discovered vulnerability 'Kr00k' differs from '
What is the vulnerability 'KRACK' of WPA2 itself that affects almost all Wi-Fi devices such as smartphones and PCs, and what are the measures? -GIGAZINE

ESET is urging both Wi-Fi chip makers and device makers to recognize the vulnerability following the discovery of this vulnerability, and Apple has already corrected the vulnerability with iOS 13.2, iPadOS 13.2, macOS Catalina 10.15.1 Is said to be.
Related Posts:
in Security, Posted by darkhorse_log







