It turns out that 500 Chrome extensions were stealing personal information, more than 1.7 million victims

If you install an extension from the ``
Security researchers partner with Chrome to take down browser extension fraud network affecting millions of users. | Duo Security
https://duo.com/labs/research/crxcavator-malvertising-2020
500 Chrome Extensions Caught Stealing Private Data of 1.7 Million Users
https://thehackernews.com/2020/02/chrome-extension-malware.html
500 Malicious Chrome Extensions Impact Millions of Users | Threatpost
https://threatpost.com/500-malicious-chrome-extensions-millions/152918/
Researcher Jamila Kaya of security company Duo Security and engineer Jacob Rickard reported on February 13, 2020 that approximately 500 malicious Chrome extensions were identified and removed from the Chrome Web Store. Announced. According to the announcement, more than 1.7 million victims have installed malicious Chrome extensions in their browsers.
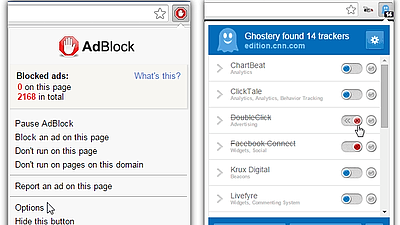
Kaya said, using the CRXcavator.io security evaluation tool for its Chrome extensions, 70 Chrome extensions secretly send commands to a PC that can be used as a platform for cyber attacks. C & C server) ]. When Kaya shared this information with Google, Google found that another 430 similar extensions existed on the Chrome Web Store. A total of 500 extensions found to be malicious by Kaya and Google were immediately removed from the Chrome Web Store.
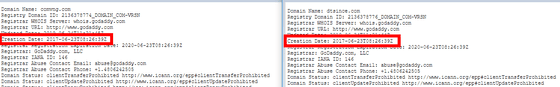
The source code of the malicious extension found this time was almost the same, but because it was registered with a different name, it escaped detection by the detection mechanism of the Chrome Web Store. According to Kaya, the author of the extension in question has been active since at least January 2019, and has been particularly active between March and June 2019.

In addition, the date of June 23, 2017 was found in the source code, suggesting that the activities of the criminal may be quite long-term.
Kaya and his colleagues discovered a malicious extension that communicated with a C & C server by masquerading as an advertisement displayed while using the extension to steal personal information. Many of the ads displayed in the extension were legitimate, issued by
These malicious ads, which are displayed for fraudulent purposes, have been called ' malvertizing ' by experts and have been increasing in recent years. 'This technique is extremely difficult to detect, despite years of rampage, and as long as there are ads that track users, it will continue to be a popular threat spreading technique.' I said.
To address the spread of these malicious extensions, Google revised the Chrome Web Store rules from October 2019 to prohibit extensions that do not have a privacy policy and require developers to use extensions Requesting the least privilege to do so. In addition, we have implemented a reward program that rewards those who find extensions that violate the rules, and strengthened the monitoring system.

According to a Google spokeswoman, 'We thank the research community for their efforts to detect fraud. We'll take action as soon as we find extensions that violate our policies, and turn cases into training materials.・ We will help improve the analysis both manually and manually. '
In addition, as a way to protect yourself from the extension that Malvertizing hides, Kaya said, `` Review the extension installed in the browser regularly, delete unnecessary ones, and report if you find suspicious ones We recommend that you pay more attention to extensions and check out information about extensions that you can easily access to help increase your security. '
Related Posts: