Malware `` xHelper '' that can not be repelled even if it is returned to the factory default state on Android is discovered

by
Symantec, which is developing an anti-virus application, announced that it has been confirmed that more than 45,000 Android devices have been infected in 6 months. The malware, named “ xHelper ”, was re-installed immediately after returning the smartphone to the factory state, and there is no way to prevent the article creation at present.
Xhelper: Persistent Android dropper app infects 45K devices in past 6 months | Symantec Blogs
https://www.symantec.com/blogs/threat-intelligence/xhelper-android-malware
Mobile Menace Monday: Android Trojan raises xHelper Malwarebytes Labs | Malwarebytes Labs
https://blog.malwarebytes.com/android/2019/08/mobile-menace-monday-android-trojan-raises-xhelper/
New 'unremovable' xHelper malware has infected 45,000 Android devices | ZDNet
https://www.zdnet.com/article/new-unremovable-xhelper-malware-has-infected-45000-android-devices/
A nearly impossible to remove Android malware has infected 45,000 devices | Android Central
https://www.androidcentral.com/nearly-impossible-remove-android-malware-has-infected-45000-devices
xHelper was discovered in March 2019. Initially it was not attracting much attention, but after that, the spread of explosive infection was confirmed, and in August 2019 Malwarebytes releasing the anti-malware application Malwarebytes Security `` 33,000 units ”Devices are infected.” On October 29, 2019, Symantec confirmed that 45,000 devices were infected.
According to Malwarebytes, xHelper was discovered by a very minor puzzle game app that has not downloaded more than 10 times on Google Play. In addition, Symantec said, “There are some types of samples that were not found on Google Play, so there seems to be an unknown source of infection,” said that the main cause is the download of apps from unknown sources by users I showed how to see.
If an Android device is infected with xHelper, an advertisement notification will be displayed, but it will not cause any significant damage.
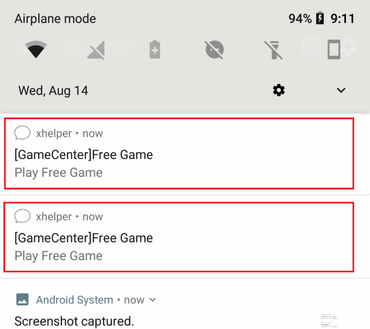
However, a notable feature of xHelper is that it is almost impossible to delete. Even if xHelper is uninstalled from the terminal, it will be reinstalled immediately, and even if the terminal is returned to the factory default settings, it will be reinstalled after a few minutes. Symantec has confirmed that `` xHelper does not tamper with Android system applications and there is no evidence that it is preinstalled on the terminal itself '', but it will be reinstalled every time the terminal is reset The cause is “unknown”.

by geralt
What's more, Symantec discovered from the xHelper source code that it was still under development and found that it is currently evolving. Initially discovered in March, xHelper had only the function to display advertisements, but the function has gradually increased, and as of October 2019 `` C & C server '' that sends commands to terminals infected with malware It is said that the connection function to has been acquired. This is expected to enable data theft and terminal hijacking in the future.
Malwarebytes, who reported about xHelper in August, said, “It's no exaggeration to say that xHelper is hosted on New York and Texas IP addresses and is targeted at American users.” On the other hand, Symantec analyzed xHelper in October, “The code under development of xHelper is tagged with the same name as 4G carrier Jio , the largest in India, and the attacker planned an attack targeting Jio users. “It ’s likely that they ’re likely,” he said, saying that more than 300 million users in India are potential targets.
Symantec recommended the following precautions to address xHelper:
-Keep your OS and apps up to date.
・ Do not get apps from untrusted sources.
• Pay close attention to the permissions required by the app.
・Install appropriate mobile security apps such as “ Norton Mobile Security ” and “ SEP Mobile ”.
・ Back up important data frequently.
Related Posts:
in Smartphone, Security, Posted by log1l_ks







