What are the tips for successfully using G Suite, as revealed by a former Google employee?

'
Newsrooms, let's talk about G Suite
https://freedom.press/training/blog/newsrooms-lets-talk-about-gsuite/
◆ G Suite security itself is strong
When users access Google services, including G Suite, Google protects data by encrypting communications and stores it in Google data centers . The stored data itself is also completely encrypted, so in principle it is impossible for anyone other than the user to view the contents. However, there are exceptions.
For example, Google has stated that it will not divert G Suite data to advertisements, but in addition to detecting spam, malware, targeted attacks, etc., as well as applications that support spell checking and searching within a user's Google account I use it. We may also scan your data for content that violates laws and Google regulations.
Some of them were mistakenly considered content that violated the terms, and “Your account was frozen because a report on wildlife trafficking that was stored in Google Docs violated the terms of service. I was sometimes heard.
Has anyone had @googledocs lock you out of a doc before? My draft of a story about wildlife crime was just frozen for violating their TOS.
— Rachael Bale (@Rachael_Bale) October 31, 2017
However, Google explained about the large number of false positives that occurred in 2017 , `` Automatic blocking due to faulty flags to protect users from viruses, malware, and other malicious content '' And the account was also frozen quickly, so it did not develop into a major problem.
In addition, the data center that stores the data is physically protected by a strict security system, and the number of employees who can enter and leave the facility and access the data is severely restricted. In a document explaining security (PDF file) , `` We have set up an incident response team to investigate unauthorized use of customer data, We are taking disciplinary action, including criminal prosecution. ' However, there are cases where third parties who are not Google employees can view G Suite data without being litigated or prosecuted. That is the law enforcement investigation.
◆ Request for disclosure of G Suite data to law enforcement agencies
One case in which G Suite data was revealed by law enforcement agencies was an investigation into the exposure book published in 2012 : Confront and Conceal: Obama's Secret Wars and Surprising Use of American Power . Under the Obama administration, Stuxnet 's investigation into the book discussing cyber attacks on the Iranian nuclear facility from the United States, FBI was deputy former James Cartwright headquarters of the Joint Chiefs of Staff , who allegedly directed the attack against Google We asked for disclosure of the interaction between the chairman and three journalists, including David Sanger , author of the exposure book.
In response to this, the trial document created based on the data submitted by Google (PDF file) describes the date and frequency of Mr. Cartwright who is the subject of the survey and the reporter's Gmail correspondence .
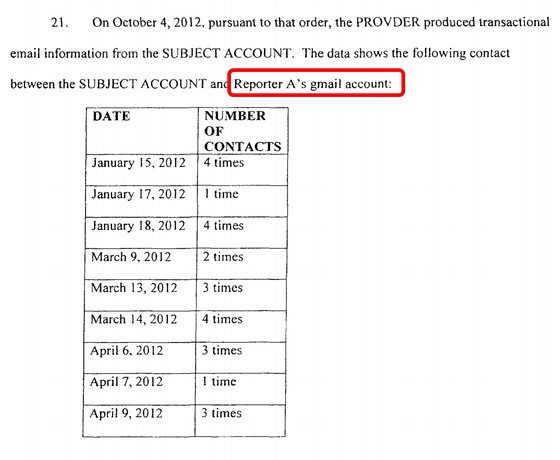
In addition to the date and time of the exchange, various data such as transmission / reception history, deleted messages, address book contents, communication log, account setting contents, IP address, etc. were handled in the court.
If you look at the following movie, you can see how Google responds to such disclosure requests by law enforcement agencies.
First, suppose you want to get data for a Gmail user with an investigative authority.

The investigator then goes to court to obtain a search warrant.

The Google “examiner” will receive the first search warrant in effect. The main task of the examiner is to prioritize the contents of the search warrant.

The search warrant that the examiner has determined to be 'promptly addressed' is handed over to the 'producer' where it undergoes a detailed check.

For example, if the content of a search warrant is unclear, or if the target user is someone else who is unrelated to the search, send it back to the search authorities and ask them to reacquire the warrant.

In addition, the data requested in the search warrant is often too broad, such as “data for all services” ...

Negotiations will be made regarding the content and scope of data required for the investigation.

A series of data disclosure is completed by bringing the resulting material to the court with a certificate certifying that the data is authentic by the “record custodian”.

◆ View by boss
If you use G Suite at work, the G Suite workplace administrator can also view the data. G Suite is divided into three versions: “

Of course, you can view all files in Google Drive and Google Docs as well as Gmail. You can even restore deleted emails from the draft folder and read them.

◆ Tips for using G Suite well
In using G Suite, which can be viewed by investigative agencies and supervisors, Mr. Shelton specifically confirmed ' activity check ' ' check G Suite version ' ' check whether data should be saved in G Suite ' We recommend three. The activity can be confirmed from the account information, but the G Suite version must be confirmed with the G Suite administrator at work. Checking with the manager at work may be a bit hurdle, but the third “Don't put too much private information in G Suite” is a self-defense measure that you can do right away.
Shelton emphasized that “G Suite is protected with strong encryption during communication, but it is not encrypted end-to-end ”, and the service that allows sharing of encrypted files “ Tresorit ” I recommend that you can also use it or save it to offline storage.
Shelton said at the end, “G Suite is a powerful tool that helps you store data for long periods of time and build a collaborative environment, but it can also save what we want to keep secret.” , He expressed his belief that convenience and privacy are a trade-off.
Related Posts:
in Web Service, Web Application, Posted by log1l_ks







