Why did White Hackers make public the zero-day vulnerability in Steam for Windows that could affect more than 96 million people?

The Windows version of Steam's
One more Steam Windows Client Local Privilege Escalation 0day
https://amonitoring.ru/article/onemore_steam_eop_0day/
Researcher Discloses Second Steam Zero-Day After Valve Bug Bounty Ban | Threatpost
https://threatpost.com/researcher-discloses-second-steam-zero-day-after-valve-bug-bounty-ban/147593/
Second Steam Zero-Day Impacts Over 96 Million Windows Users
https://www.bleepingcomputer.com/news/security/second-steam-zero-day-impacts-over-96-million-windows-users/
Researcher publishes second Steam zero day after getting banned on Valve's bug bounty program | ZDNet
https://www.zdnet.com/article/researcher-publishes-second-steam-zero-day-after-getting-banned-on-valves-bug-bounty-program/
White hacker Vasily Kravets announced a Windows version of Steam's zero-day vulnerability that allows all local users to gain Windows 'administrative privileges'. Obtaining administrator privileges makes it possible to execute important Windows files without permission, which may lead to malware installation and unauthorized access to files.
Kravets reports Steam vulnerabilities to HackerOne , a company that runs a “bug bounty” service that pays a bounty based on discovered vulnerabilities. However, Valve said that the reported vulnerability of Steam was 'a type of vulnerability that can only be used by manipulating files inside the PC using other vulnerabilities' and refused to accept it as a vulnerability. Furthermore, Mr. Kravets was banned from Valve's bounty program on HackerOne.
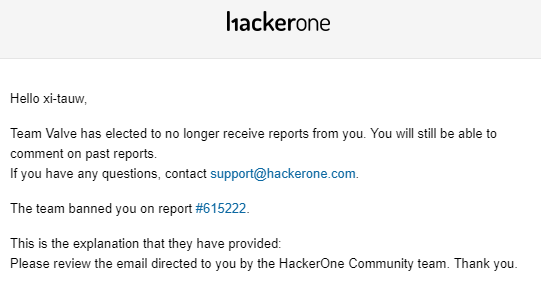
Kravets notified the announcement of the vulnerability, and HackerOne stopped the reporting thread without explanation. On August 2, 2019, more than 45 days have passed since the report, Kravets will disclose the vulnerability.
This is my #ZeroDay #PublicDisclosure of a security vulnerability at Steam Windows client which allows a local privilege escalation. # 0day
— Felix aka [xi-tauw] (@PsiDragon) August 7, 2019
Rus-https: //t.co/W4VNdHIBCI
Eng-https: //t.co/1ZDFzx3uxt
After the announcement, Kravets will receive an email from HackerOne stating that Valve has no plans to fix this vulnerability. However, as a result of the public vulnerability that became a hot topic among Steam users and security researchers, Valve finally released a patch.
After the release of the patch, Kravets will receive a report that the vulnerability is still alive. Kravets developed a new method related to vulnerabilities that gained administrator rights and released it to the public, and why: `` Valve prefers reporting to the public rather than confidentially reporting That ’s why. ”
One more Steam Windows Client Local Privilege Escalation 0day
The announced vulnerabilities are quite detailed, and a reproduction movie has also been posted.
Steam EoP 0day vulnerability (filesystem based)-YouTube
Kravets said in a series of uproars, 'It's sad and simple. Valve continues to fail.' Meanwhile, ZDNet, Threatpost, and Bleeping Computer have asked Valve for comments, but Valve seems to be silent.
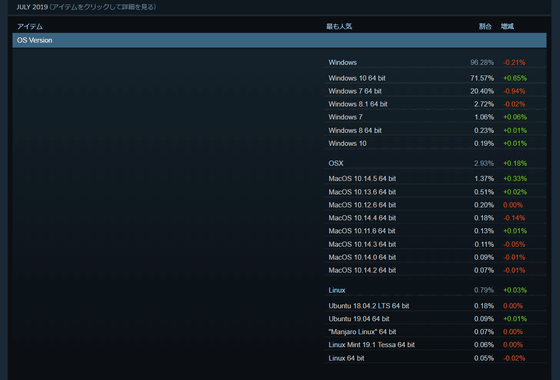
Steam is the world's largest gaming platform with over 1 billion registered accounts and over 100 million users. According to a Valve survey in July 2019 , about 96% of users are using Windows PCs, and it is reported that the vulnerability of Steam for Windows can affect 96 million people.
Related Posts: