Phishing scams to disable 2-step authentication of Gmail and Yahoo! Mail are rampant

by pixelcreatures
Researchers at the security company " Certfa " reported on blogs that a group of hackers connected to the Iranian government collect target information and prepare spear-phishing e-mails tailored to the security level of the target I will. Since hackers can see the state of the target in real time, two-step authentication has been invalidated.
The Return of The Charming Kitten - Certfa Blog
https://blog.certfa.com/posts/the-return-of-the-charming-kitten/
Iranian phishers bypass 2fa protections offered by Yahoo Mail and Gmail | Ars Technica
https://arstechnica.com/information-technology/2018/12/iranian-phishers-bypass-2fa-protections-offered-by-yahoo-mail-and-gmail/
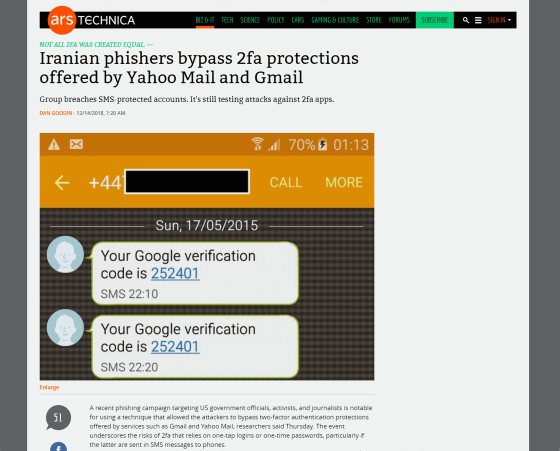
According to the researcher, the image sent by the attacker is hidden, and by using it, the attacker can check whether the target is watching mail in real time. When the target opens a fake security page pretending as Gmail or Yahoo! and entering a password, the attacker immediately inputs that information into a real login page. If the target account adopts 2-step verification, the attacker redirects from the target web page to a new page requiring a one-time password, but this information can also be checked in real time It will be possible to steal.
Certfa researchers have confirmed that this technology can break through SMS based two-step verification. Although it has not been confirmed whether using the application such as Google Authenticator similarly is also confirmed, technically, there is almost no reason to say that attacks will fail if it is an application such as Google Authenticator.
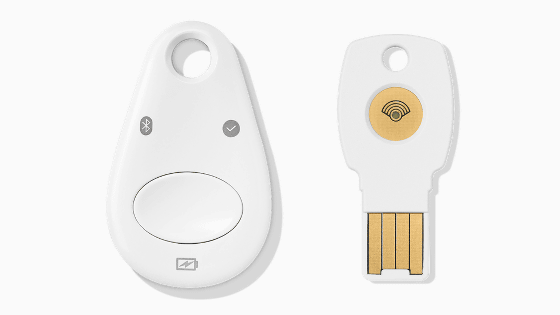
A possible way to avoid attacks by attackers is to use 2-step authentication using industry standard security keys. The Google Account functions also with the USB security key "FIDO U2F Security Key" , but it is thought that attacks can be avoided if it is such a type of security key connected via USB, Bluetooth, NFC. In fact, Google has introduced Yubico's two-step security key "YubiKey" as an employee's authentication tool.

In addition, since 2017, Google has launched the " Advanced Protection Function Program " that provides the highest level of security protection for people who are susceptible to attack by hackers, such as government officials, journalists and companies. However, since most of the general public is doing normal two-step authentication, it is said that the necessity of training to direct "suspicion eyes" to general users is called for.
According to Certfa, attackers are not only concerned with phishing scams that break through 2-step certification, but also have email addresses that feel connection with officials such as "notifications.mailservices@gmail.com" or "noreply.customermails@gmail.com" We use phishing scams we use, phishing scams that utilize 20 domains tailored to the services used by the target, and so on.
Certfa confirmed that the domain and IP address used for phishing scams is connected to a group of hackers related to the Iranian government called "Charming Kitten". The latest attack took place a few weeks before November 2018 when the United States resumed Iran sanctions. Targets of attacks include individuals and politicians involved in sanctions, civil rights and human rights activists, journalists, etc. According to the AP , executives involved in nuclear negotiations and Arab atomic scientists, Iran's civil society, Washington Think tank employees, US Treasury officials and so on.
Related Posts:
in Security, Posted by darkhorse_log