Research result that the 'smart home' constructed by IoT may be peeping at life even if encrypting communication

" IoT (Internet of Things)" is a technology that connects various objects to the Internet by wireless communication and controls each other. By making full use of IoT, it becomes possible to " home smart " where home appliances and appliances are interlocked with sensors and remotely controlled by smartphones. Of course, the wireless communication used for IoT is encrypted to prevent interception, but even if you do not bother to decipher the encryption, just by analyzing the amount and timing of the information flowing over the network, Research results have been reported that living can be fully grasped.
[1808.02741] Peek-a-Boo: I see your smart home activities, even encrypted!
https://arxiv.org/abs/1808.02741
Encryption does not stop him or her or you ... from working out what Thing 1 is up to • The Register
https://www.theregister.co.uk/2018/08/10/internet_of_things_encryption_snooping/
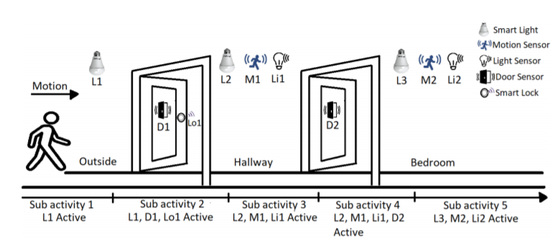
IoT makes it possible to operate various furniture and equipment at home from the network. For example, as shown in the illustration below, "Lights the entrance light before returning home" "When Smart Lock is released and the door is opened, the light in the corridor will light up with the sensor" "When the sensor detects the light in the corridor and people's movement Read "and so on are done automatically automatically. The whole house system adapts automatically to the human life.
Wireless communication used in IoT, such as Wi-Fi, Bluetooth, ZigBee, etc., is encrypted so that it can not be deciphered even if it is intercepted by a third party. However, research teams such as Florida International University and Darmstadt Institute of Technology have revealed users' actions from traffic patterns such as the packet amount and arrival time of information flowing on the network without decrypting the encrypted data I pointed out.
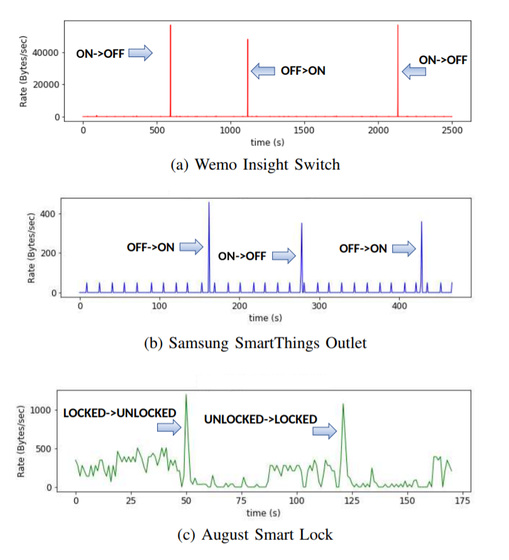
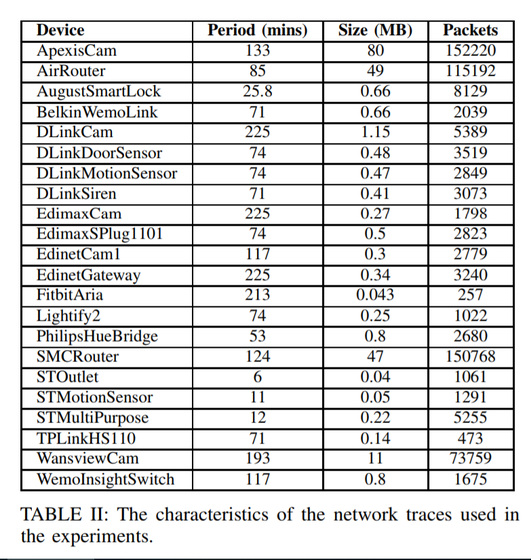
The research team actually sampled the traffic from 22 smart devices and sensors and decoded the unencrypted headers along with the traffic patterns and decoded them to locate the arrival time and packet size of each smart instrument or sensor I made it.
Furthermore, we intercepted network traffic and analyzed by machine learning, and we were able to distinguish user's state and behavior with high accuracy of 90% or more. Even if the content of the wireless signal is strongly encrypted, simply analyzing the amount and timing of the information flowing on the IoT network will cause the user's life pattern to go through to a third party.
In addition, the research team says that if the manufacturer protects the user, it will be easy to disrupt the traffic stream by deliberately flowing random noise data so that the state of the device can not be inferred.
Related Posts:
in Security, Posted by log1i_yk